TL;DR
- OFAC, in coordination with the U.K. and Australia, designated Russian bulletproof hosting provider Media Land, LLC and its network for enabling cybercriminal activities, including ransomware attacks.
- The action includes one Bitcoin address linked to Aleksandr Volosovik (alias “Yalishanda”), though Chainalysis is monitoring thousands of addresses and millions of dollars in transactions attributed to him.
- Volosovik’s hosting services supported nearly every component of the cyber kill chain, serving underground exchanges, laundering services, scammers, hackers, and ransomware operators, including sanctioned LockBit administrator Dmitry Khoroshev.
- Several designated entities were established in July 2025, shortly after OFAC’s AEZA Group designation, suggesting attempts to continue operations through new corporate structures.
- This trilateral action demonstrates continued international focus on disrupting the infrastructure layer that enables cybercrime, rather than solely pursuing individual threat actors.
- Separately, OFAC also sanctioned Ryan James Wedding, a former Canadian Olympic snowboarder, along with nine of his close affiliates. He is charged with trafficking cocaine through Mexico and Colombia to then be sold in the US and Canada.
Russian cybercrime infrastructure supporting ransomware
On November 19, 2025, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC), in coordination with counterparts in the United Kingdom and Australia, designated a network of Russian bulletproof hosting providers and associated individuals for enabling cybercriminal activities, including ransomware attacks. The action targets Media Land, LLC and its related entities, along with key individuals operating this infrastructure that has facilitated malicious cyber operations globally.
Bulletproof hosting: Critical infrastructure for cybercrime
Bulletproof hosting providers offer internet infrastructure services specifically designed to ignore abuse complaints and host malicious content with minimal risk of takedown. These services are essential for cybercriminals conducting ransomware attacks, phishing campaigns, malware distribution, DDOS attacks, and other malicious activities. By providing hosting that is resistant to law enforcement actions and abuse reports, these providers enable criminals to maintain persistent infrastructure for their illegal operations.
Modern cybercrime infrastructure operates through sophisticated networks that transcend traditional borders. The technical infrastructure supporting these operations typically involves multiple connected entities. In this case, the designated entities included Media Land LLC, Media Land Technology LLC, Data Center Kirishi LLC, and ML.Cloud LLC. The Media Land network demonstrates how these operations maintain resilience through a distributed structure of interconnected entities. By establishing presence across multiple jurisdictions, these networks exploit regulatory gaps and create deliberate complexity to shield themselves from disruption.
The AEZA Group connection
Several of the designated entities and individuals are linked to AEZA Group LLC, which OFAC previously designated in July 2025 for providing bulletproof hosting services. Today’s action expands on that designation by targeting additional individuals and entities within the same ecosystem. Maksim Makarov and Ilya Zakirov, both linked to AEZA Group, were designated for their roles in supporting the network’s operations.
The designation also includes entities that appear to have been established to continue operations following previous enforcement actions. Datavice MCHJ in Uzbekistan and Hypercore Ltd in the United Kingdom were both established in July 2025, shortly after the AEZA Group designation, suggesting attempts to maintain operations through new corporate structures.
Cryptocurrency infrastructure
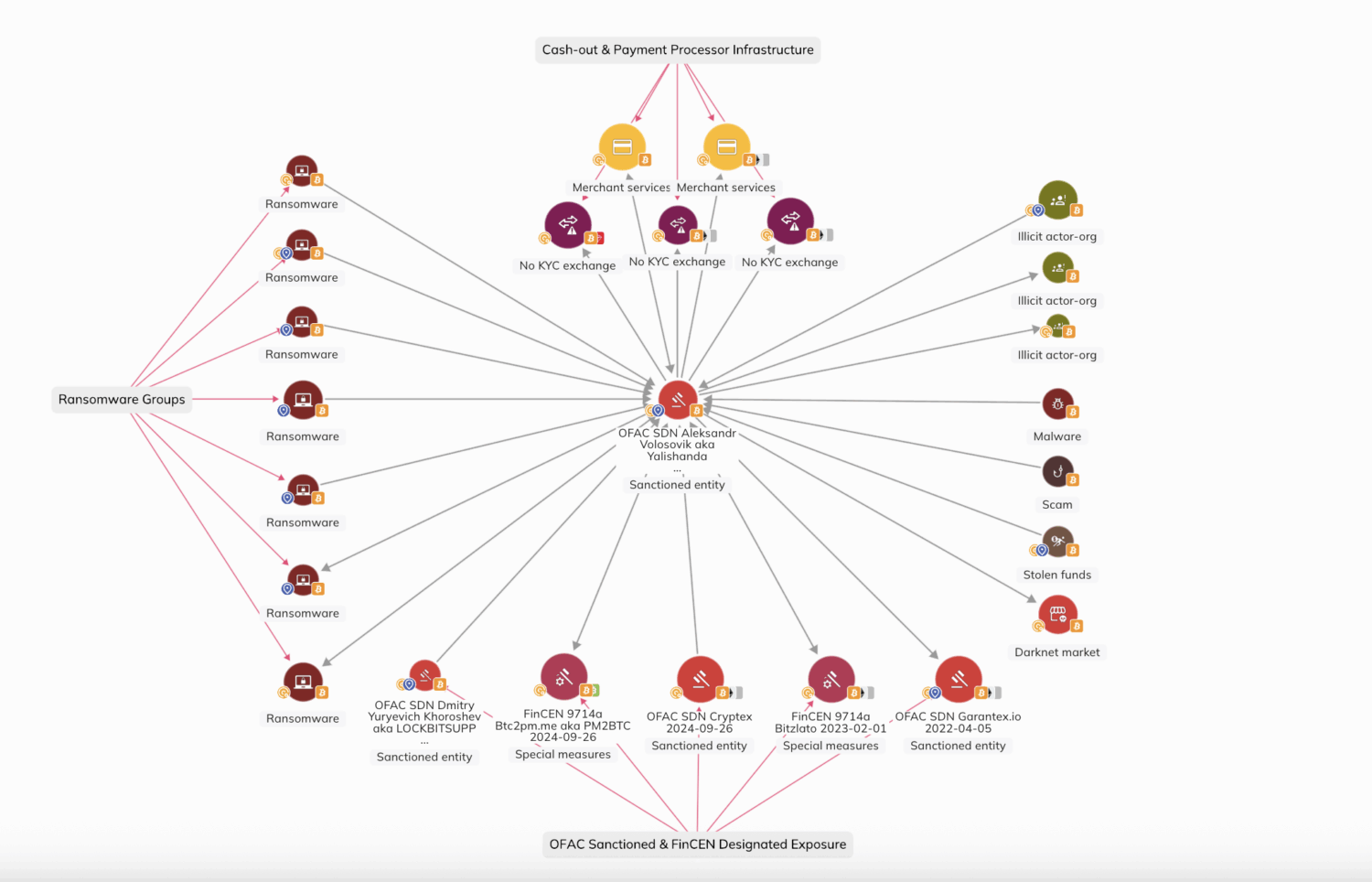
OFAC included one Bitcoin address (18dLDAWi8LmrHbEq3QzDJb9SLxCf4uimXB) in today’s designation, associated with Aleksandr Volosovik, also known by the aliases “Ohyeahhellno,” “podzemniy1,” and “Yalishanda.” Although one address was listed in the designation, Chainalysis is monitoring thousands of addresses and millions of dollars worth of cryptocurrency transactions attributed to Yalishanda and his enterprises.
Yalishanda’s hosting services underpinned nearly every component of the cyber kill chain, spanning from access to monetization. On-chain analysis reveals Yalishanda was being leveraged by underground exchanges, laundering-as-a-service providers, scammers, hackers, individuals selling access and malware-as-a-service, as well as ransomware operators and their affiliates, notably including sanctioned Lockbit ransomware administrator, Dmitry Khoroshev, AKA Lockbitsupp. Indeed, Yalishanda catered to criminal clientele, and the Chainalysis Reactor graph shows Yalishanda made repeated payments to an underground market, ostensibly payments for advertising his services.
International coordination against cyber threats
Today’s action represents a coordinated trilateral effort between the United States, United Kingdom, and Australia to disrupt cybercrime infrastructure. This international cooperation is critical, given the global nature of bulletproof hosting operations and their use by cybercriminals worldwide.
The designation carries secondary sanctions risk under the Ukraine-/Russia-Related Sanctions Regulations, meaning that non-U.S. persons could face sanctions exposure for engaging in certain transactions with the designated parties. This expanded sanctions framework increases pressure on these networks by making it riskier for international service providers and financial institutions to do business with them.
Pattern of targeting cybercrime infrastructure
This action continues OFAC’s strategy of targeting the infrastructure layer that enables cybercrime rather than solely pursuing individual threat actors. Recent similar actions include:
- July 2025: OFAC designated AEZA Group LLC for providing bulletproof hosting services
- February 2025: OFAC designated ZServers for similar bulletproof hosting activities
By targeting the hosting providers, payment processors, and technical infrastructure that cybercriminals rely on, authorities can disrupt multiple criminal operations simultaneously and increase the operational costs and risks for threat actors.
Global drug trafficking ring operated by former Olympian
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) has sanctioned Ryan James Wedding, a former Canadian Olympic snowboarder who competed in the 2002 Winter Olympics, along with nine of his close affiliates. He is charged with trafficking cocaine through Mexico and Colombia to then be sold in the US and Canada. According to press releases from the Department of Treasury and U.S. Department of Justice (DOJ), Wedding is known to engage in extreme violence and has orchestrated the murders of dozens of people across Latin America, Canada, and the United States.
Wedding is currently on the FBI’s Ten Most Wanted Fugitives list, and is believed to be hiding in Mexico while directing the operations of this large drug trafficking operation.
Drug trafficking laundering on-chain
As seen in today’s designation, stablecoins are leveraged by large-scale drug trafficking organizations due to their price comparability to the US dollar, which lowers overhead costs and maximizes profits. However, the use of stablecoins provides law enforcement with the opportunity to seize assets on the blockchain, as issuers can block any further movement. Wedding’s USDT_TRX wallets, as well as other related wallets, were blocked by Tether in July.
Money laundering conducted by drug trafficking organizations also requires global collaboration, and can sometimes include accomplices in seemingly unrelated industries. The nine other individuals who were designated alongside Wedding include his wife, who laundered proceeds on his behalf, a Canadian jeweler who laundered drug proceeds through his business, and numerous other individuals from Italy and the UK. On-chain, laundering affiliates of Wedding would break the USDT up into smaller pieces before directing the funds to a wallet controlled by Wedding.
Wedding’s cryptocurrency connections
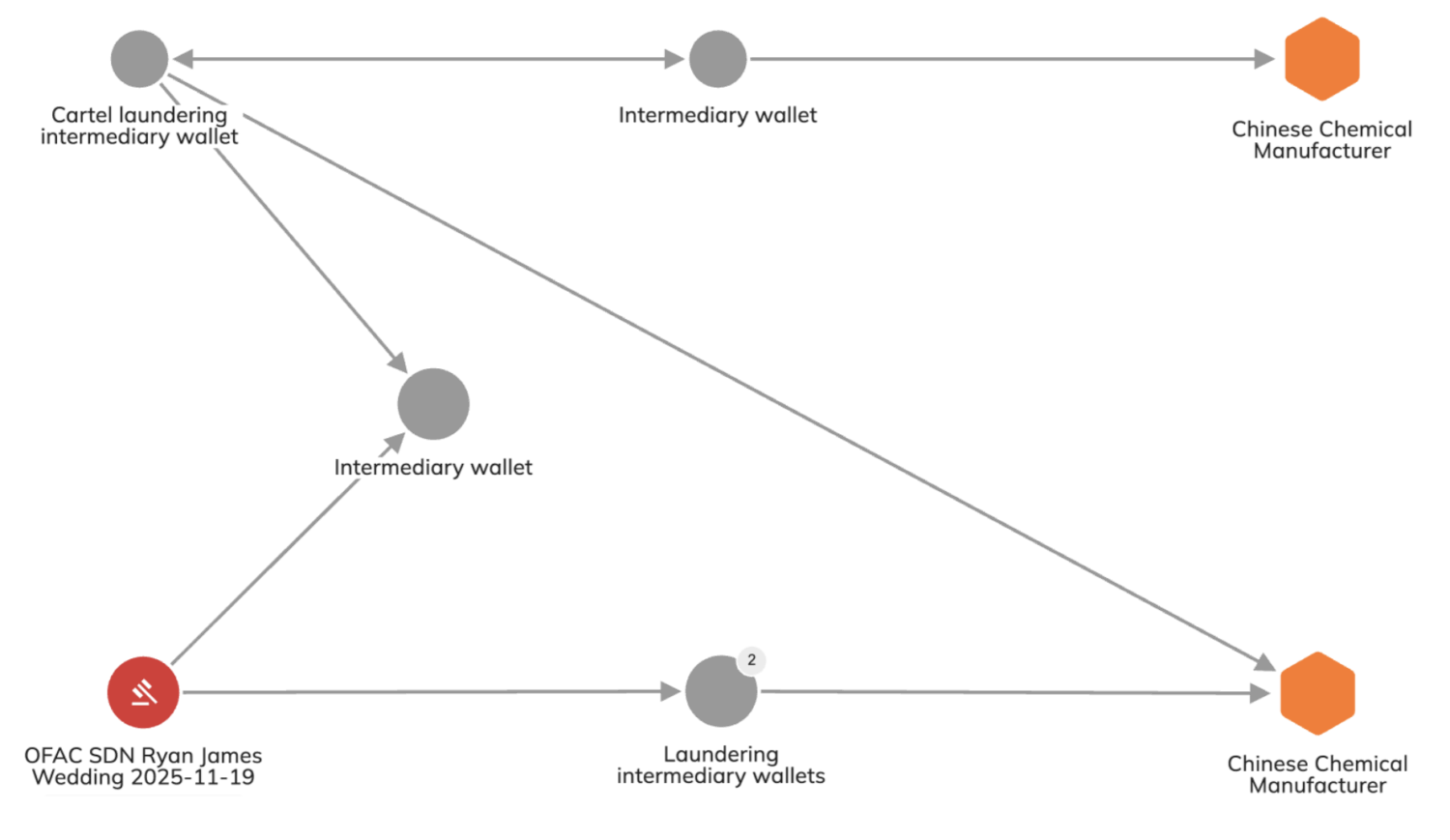
Three TRX addresses belonging to Wedding were included in OFAC’s designations. Overall, Wedding received over 263 million dollars worth of USDT_TRX. As shown in the graph below, these wallets have indirect ties to China-based chemical manufacturers identified by Chainalysis. Further, there were close connections to other intermediary laundering wallets that have been involved in cartel-related laundering activities.
This on-chain behavior illuminates the connection between the laundering of drug proceeds and trusted Chinese chemical manufacturers, who provide everything from synthetic drug precursors to cutting agents that stretch out batches of cocaine, and serve anyone from darknet vendors to larger-scale groups.
The graph above shows that the same persons/group laundering on behalf of Wedding were also involved in the sourcing of chemical material; whether it was for Wedding, or some other criminal actor, is unknown. However, it illustrates the quick and efficient turnaround between the laundering of proceeds and reinvestment back into the supply chain.
Impact on cryptocurrency compliance
Cryptocurrency businesses should implement enhanced screening for transactions involving the newly designated individuals and entities.
Organizations should:
- screen all transactions against updated OFAC sanctions lists as well as Chainalysis data;
- monitor for connections to previously designated bulletproof hosting providers like AEZA Group and ZServers;
- implement enhanced due diligence for customers operating hosting or infrastructure services, particularly those in high-risk jurisdictions;
- and be alert to patterns consistent with bulletproof hosting payment flows.
If you’d like to learn more about how Chainalysis products can help protect your organization from sanctions risk, click here to request a demo.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.