Earlier this year, one of the largest crypto exchanges in South Korea detected abnormal withdrawal activity from one of its hot wallets. Around 15 minutes and hundreds of transactions later, approximately ₩44.5B KRW ($33 – 35 million) had been siphoned off and the platform paused all withdrawals. Assets stolen included major tokens like USDC, BONK, SOL, ORCA, RAY, PYTH, JUP, and, although the exchange was able to freeze more than half of the stolen funds (₩23B KRW worth of LAYER tokens), the rest was already unrecoverable. An analysis of the pattern and timing of the withdrawals suggests that the attack was not due to a smart-contract bug or user-level error, but rather a compromise of the hot-wallet signing flow.
In this post, we’ll walk through current exchange hacking trends, take a deeper look into the heist, and illustrate how Hexagate’s Wallet Compromise Detection Kit and GateSigner could have detected the compromise early to limit the amount stolen.
CEX and custodian breaches are on the rise
This latest incident on a large exchange reflects a clear industry trend: CEX and custodian breaches are rising, driven by the growing complexity of running fast, multi-chain withdrawal systems in complex cloud environments. Despite the fact that exchanges and custodians now manage some of the market’s most complex on-chain flows, many developers underestimate the need for robust on-chain security, often relying on efforts that later prove insufficient.
After nearly a decade of tracking customer environments and following threat groups like Lazarus, the shift is obvious: attackers are increasingly targeting custodians and CEXs because the stakes are high and the operational stack is large and intricate. Recent attacks on Bybit, BTCTurk, SwissBorg, Phemex, and now this Korean exchange all follow the same pattern: multi-million-dollar losses caused by a single breach point.
Each case had a different root cause — social engineering that led to an account compromise, cybersecurity bugs within a tech stack, malware, internal threats, and many more. That’s how advanced attackers work: they only need one weakness. The realistic assumption is not “we’re fully protected,” but “eventually something will break.” And when it does, everything depends on how quickly you can detect and respond. Strong real-time detection and response won’t eliminate risk, but it’s what prevents an operational breach from becoming a catastrophic loss.
What happened?
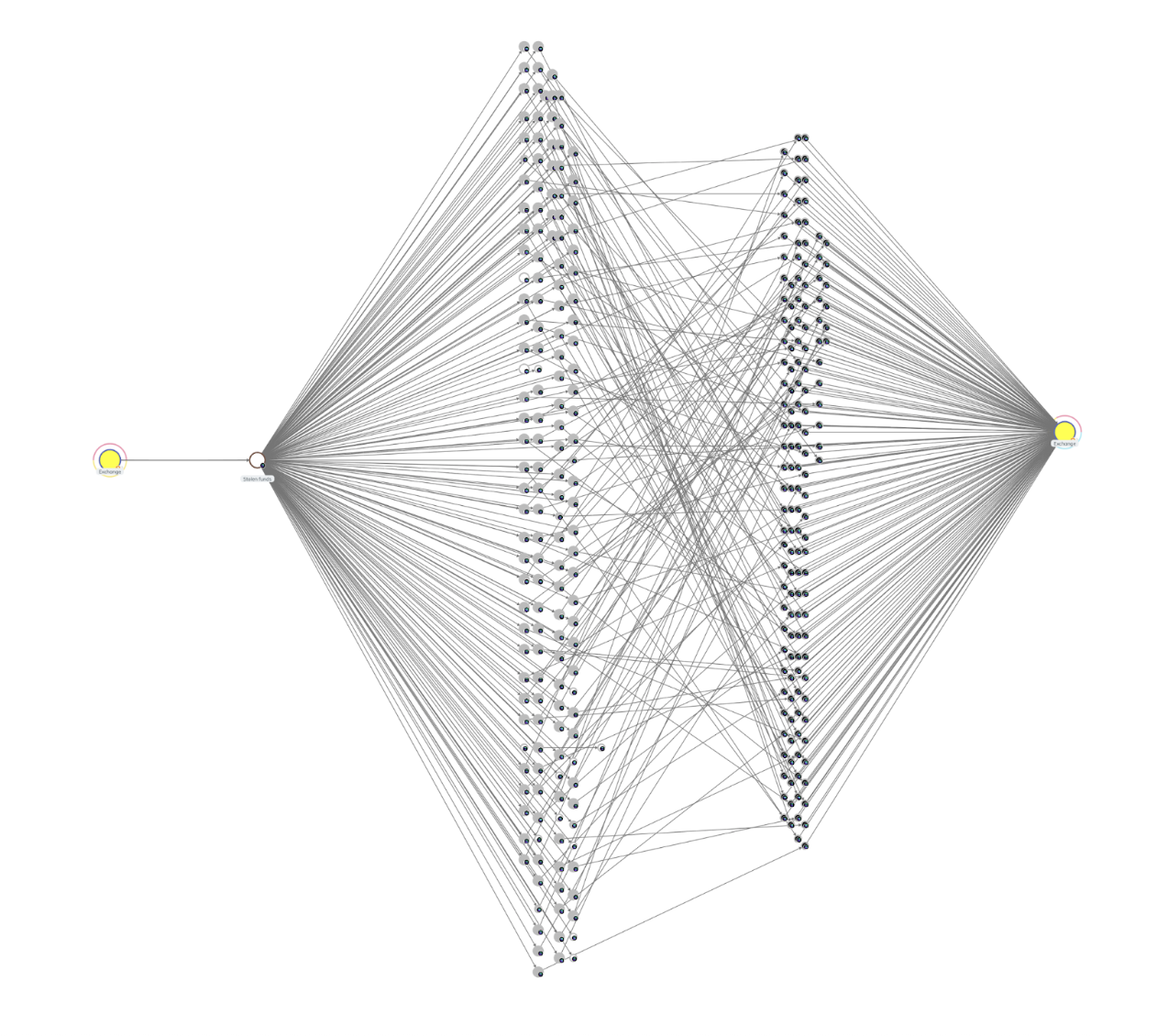
Before the incident, one of the hundreds of the exchange-linked Solana wallets involved in the incident behaved normally for weeks; its balances rose and fell, but never once dropped to zero. During the attack, however, it was fully drained in minutes — a pattern that is extremely rare in legitimate operations and highly indicative of compromise. Several key signals stand out:
- Drained-to-zero pattern: Every wallet involved shows the same signature: balances collapsing to zero in a very short window. That behavior simply does not occur in normal exchange operations.
- Massive spike in high-value outflows: In the seven days prior, there was only one outflow of around $100,000 from any of the exchange’s Solana wallets. During the attack, there were around 80 such transfers in a 15 minute window.
- High-frequency execution across many assets: The attacker moved dozens of tokens across hundreds of transactions, a burst pattern that stands out sharply against baseline behavior.
These are exactly the types of signals that advanced, automated behavioral-analytics systems, such as Chainalysis Hexagate, are designed to detect in real time. The exchange ultimately made the right call by pausing withdrawals, a decisive action that protected users and the platform. Incidents like this highlight how powerful fully automated detection and response mechanisms can be: with the right real-time pipelines in place, anomalies can be flagged and mitigated within just a few early transactions, before significant movement occurs.
Initial post-theft activity
At this stage, the exploiter was likely focusing on swapping the stolen assets through automated market makers (AMMs) to convert them into tokens that are harder for issuers to freeze. This is typical early-stage behavior following a large hot-wallet compromise. In the Chainalysis Reactor graph below, we see that most movements so far were consolidation and asset-type rotation rather than dispersion.
How Chainalysis Hexagate detects and stops wallet draining
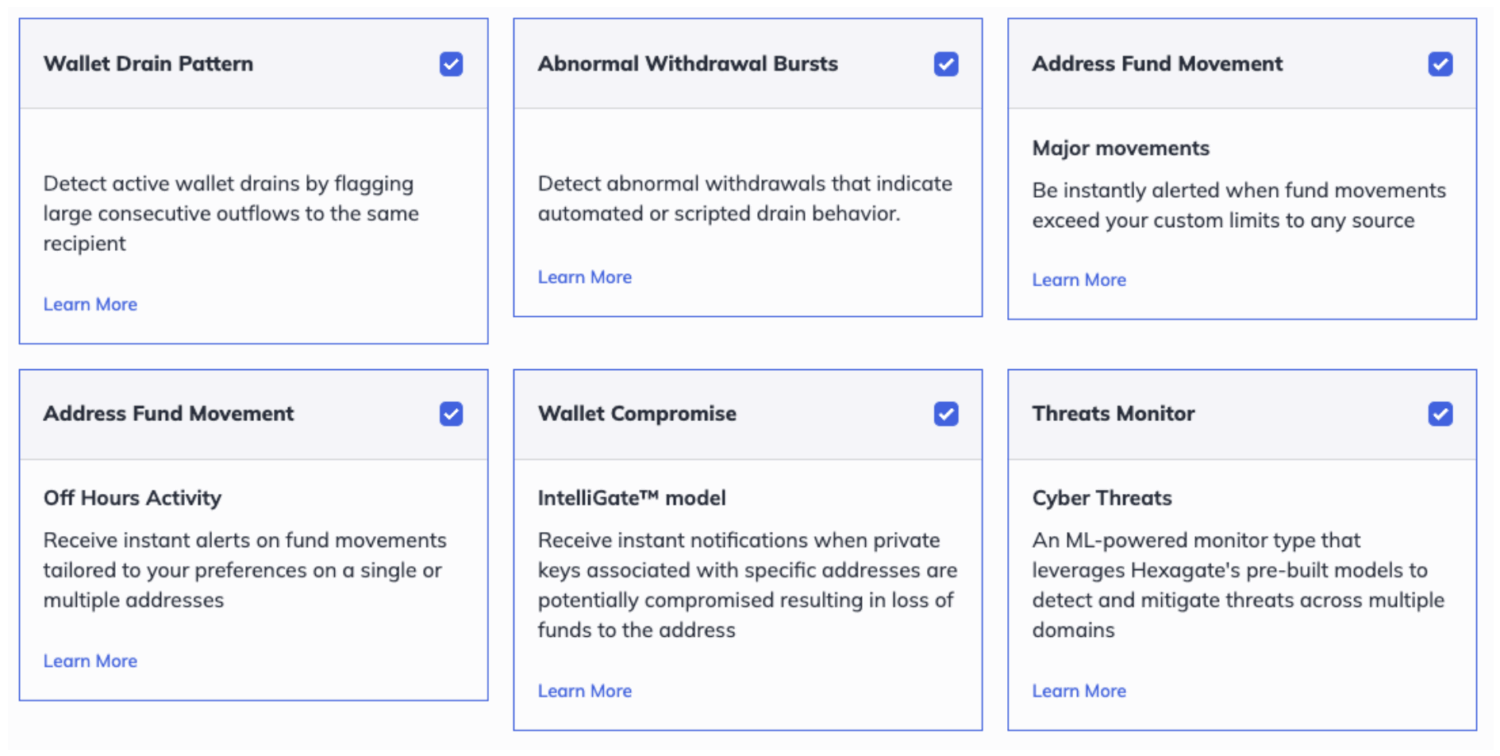
1. Wallet Compromise Detection Kit
A set of real-time monitors that look for the earliest signs of a compromised hot wallet, enriched with Chainalysis intelligence, including:
- Drain-pattern detection: spots wallets suddenly dropping toward zero.
- Burst detection: flags rapid, high-value withdrawals in short windows.
- Unknown-recipient detection: alerts when funds move to addresses outside an internal, trusted ecosystem.
- ML-based compromise detection: models trained on historical CEX compromise events and broader ecosystem behavior.
These signals fire within the first few malicious transactions, and in some cases, even before, based on early behavioral drift. With these early detectors, CEXs can also set up automated responses, so when you raise your defenses (pausing withdrawals, routing to cold storage, quarantining flows), it happens faster, more consistently, and with fewer operational mistakes.
2. GateSigner (pre-signing protection)
GateSigner plugs into your signing flow and simulates every transaction for risky activity, providing your team a critical check before approving the transaction:
- The withdrawal is simulated first.
- The result is checked against your compromise monitors.
- If something looks wrong, GateSigner blocks or escalates the transaction before it ever hits the chain. This prevents your infrastructure from unintentionally signing the very transactions an attacker is trying to push through.
Some final thoughts
Hot-wallet compromises are becoming one of the most expensive and frequent risks facing custodians and exchanges today. The organizations that are best positioned are the ones that invest in early detection and strong controls around their signing pipelines. Hexagate’s Wallet Compromise Detection Kit and GateSigner give CEXs the ability to catch anomalies immediately, block dangerous withdrawals before they execute, and automate the right response at the right moment. It’s the most effective way to turn an inevitable breach into a contained event and protect users, operations, and the business as a whole.
Learn more about how Wallet Compromise Detection Kit and Gatesigner can prevent you from being a victim of the next big heist, or request a demo today.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.