As the value of assets on the blockchain surpasses $1 trillion in 2023, staying ahead of blockchain-specific cyber threats is more imperative than ever.
In our recent update on crypto crime, we noted an encouraging 65% decline in year-over-year illicit transaction volume halfway through 2023. Yet, as the blockchain ecosystem continues to mature, so do the tactics used by cybercriminals. To thrive in this new reality, organizations must adopt a robust security framework.
The rapid growth of decentralized technologies has ignited groundbreaking innovation, but the nature of decentralization presents its own unique challenges. Following similar pathways as the adoption of the Internet, soon every institution will require a blockchain security strategy to safeguard their operations.
In this blockchain security overview, we’ll discuss vulnerabilities and exploits commonly encountered in the crypto space, explore protective measures, and take a look at the promising future of on-chain security.
In this article, we discuss:
- What is blockchain security?
- Public blockchain security
- Private blockchain security
- How are blockchains secured?
- How are transactions on a blockchain secured?
- Are blockchains vulnerable to security threats?
- Types of blockchain security breaches
- Creating a robust blockchain security strategy
- Blockchain security and enterprises
- Blockchain custody, security, and reporting solutions
- Blockchain security: Regulatory and legal considerations
- The future of blockchain security
What is blockchain security?
Blockchain security refers to the combination of cybersecurity principles, tools, and best practices in order to mitigate risk and avoid malicious attacks and unauthorized access while operating on blockchain networks.
While all blockchains run on distributed ledger technology (DLT), not all blockchains are functionally the same or equally secure. While both public and private blockchains have their own sets of advantages and disadvantages, their security models are fundamentally different due to the open versus closed nature of their networks.
Public blockchain security
Public blockchains like Bitcoin and Ethereum are open, permissionless networks where anyone can join and participate in validating transactions. The codebase of public blockchains like Bitcoin and Ethereum is open source. This means it is publicly available and is continually vetted by a community of developers who review the code for bugs, vulnerabilities, and other issues. By leveraging the collective expertise of open-source communities, the security, features, and efficiency of these blockchains are continuously examined and improved. At the same time, hackers and malicious entities are also continuously examining the code, searching for vulnerabilities to exploit.
Who is responsible for the security of a public blockchain?
While the founders are responsible for the initial source code and often inform the progress of the network through active participation, the overall responsibility for securing a public blockchain like Ethereum is distributed among all participants in the network across the world. This includes validators and node operators who maintain the network, and hundreds of thousands of developers who write code. Users also contribute to the overall security of the network by practicing good security hygiene. Since a public blockchain is a decentralized system, no single entity can claim sole responsibility for its security, making it resilient against various types of attacks.
Maintenance and development of public blockchains
Public blockchains often have associated organizations dedicated to advancing development and community engagement, such as the Ethereum Foundation. Even Bitcoin, created by the anonymous entity Satoshi Nakamoto, has a dedicated team of maintainers responsible for continuously updating and improving the Bitcoin Core software. Like any software, it is a “living” thing that requires regular maintenance and updates to address bugs and adapt to new circumstances. Any proposed changes to the core network must still be accepted by consensus. In Bitcoin, this is known as a Bitcoin Improvement Proposal or BIP. Anyone — not just maintainers — can propose a BIP.
Private blockchain security
Private blockchains are exclusive networks with limited access, making them more centralized. This centralized control potentially enhances their resistance to certain external threats. Securing a private blockchain is the sole responsibility of the operating entity. The centralized nature of these blockchains means that there is a single point of failure, making it crucial for the institution to implement strong security measures.
Although private blockchains may not benefit as much from the decentralized and security-by-numbers approach of public blockchains, they are generally faster and more efficient due to less computational work required for consensus algorithms. However, because the entity granting permission also has authority over the network, there is a theoretical risk of the network being shut down or manipulated, a security risk that is not typically found in public blockchains.
How are blockchains secured?
Blockchain technology runs on a distributed digital ledger system. A blockchain network is made up of a worldwide network of computers, known as nodes, validating and recording transactions. Every participant maintains a copy of the ledger, so there is no centralized authority or point of failure. Each time a transaction occurs — such as sending or receiving cryptocurrency — it is recorded on a block.
Before a block (made up of a group of transactions that occurred during a given time frame) is added to the chain, it must be verified by consensus. That’s where consensus mechanisms come into play. There are several different consensus mechanisms, but the two most popular methods are Proof-of-Work and Proof-of-Stake. In a Proof-of-Work system, miners compete to solve computationally intensive algorithms to validate transactions. In a Proof-of-Stake system, network participants lock up a certain quantity of tokens to run a node to validate transactions. Miners and stakers are incentivized with rewards to secure the network. This process ensures everyone agrees (or reaches consensus) on the validity of each transaction. Once a block is full, it is sealed and linked to the previous block using a cryptographic code, forming a chain. By linking each block using cryptography and distributing the ledger across numerous computers, any attempt to tamper with a block would disrupt the entire chain. With the ledger visible to all participants, any suspicious activity can be quickly identified.
With blockchain, every participant has a role in maintaining its integrity. This technology is the foundation of popular cryptocurrencies like bitcoin and ether, and holds immense potential for the future of digital transactions and beyond.
How are transactions on a blockchain secured?
Unlike traditional finance — which operates on permissions to pull funds — a crypto transaction is a push transaction, initiated peer-to-peer without the need for an intermediary. Participants in blockchain networks control their digital assets on the blockchain with a private key — a cryptographically secured method of authentication and access.
Crypto requires you to be deliberate. Because no intermediary is required, personal responsibility becomes much more important when transferring value on-chain.There is no undoing a transaction that is confirmed on the blockchain. This makes it notoriously difficult to recover funds that are lost or stolen.
Are blockchains vulnerable to security threats?
The notion that blockchain technology is inherently immune to security threats is somewhat misleading, but there are several unique structural features of blockchain that bolster its intrinsic security properties:
- Cryptography: Every transaction on the blockchain is secured with cryptographic principles, ensuring data integrity and authentication. Public key infrastructure (PKI) grants users a public key to receive assets and a private key to safeguard them.
- Decentralization: Instead of a centralized server or authority, blockchains operate across a network of computers (nodes). This distributed nature means that even if a node or a group of nodes are compromised, the entire system remains largely unaffected.
- Consensus: These algorithms ensure that all nodes in the network agree on the validity of a transaction. Common consensus algorithms include Proof-of-Work (PoW) and Proof-of-Stake (PoS). Features like PoW or PoS make it computationally non-viable for a single attacker to control the majority of nodes, known as a Sybil Attack.
- Immutability: Once a block is added to the blockchain, its content becomes immutable, meaning it cannot be changed or altered. This ensures that transaction records are always kept intact.
- Transparency: Since many blockchains are public ledgers, any change or transaction can be viewed by anyone, making malicious activity easily detectable.
While these defining characteristics are the reason blockchain technology is considered so revolutionary, there are still vulnerabilities that can be exploited. Paradoxically, some of the traits of blockchain (e.g. immutability) can introduce unique complexities if the system itself is compromised.
Types of blockchain security breaches
Blockchain vulnerabilities and security breaches can be broadly broken down in three distinct categories: ecosystem vulnerabilities, attacks on smart contracts and protocols that operate on top of the blockchain, and attacks on popular infrastructure (like wallets) and users. It’s important to note that this is not an exhaustive list of all the possible types of vulnerabilities.
Blockchain ecosystem vulnerabilities
A blockchain with a small number of nodes is more susceptible to ecosystem attacks than a large, well-distributed network. Sybil attacks or 51% attacks, for instance, are now virtually impossible to achieve on blockchains like Bitcoin or Ethereum due to the computing power or quantity of assets required. Nevertheless, it is worthwhile to understand the full scope of risks, especially if your organization is considering using smaller emerging blockchains or developing your own blockchain.
Sybil attack
A Sybil attack occurs when a bad actor targets the peer-to-peer layer of the network in order to gain control of multiple nodes.
51% or double-spending attack
This type of attack targets the consensus layer of Proof-of-Work blockchains. If an entity controls more than 50% of the network’s mining hashrate, they can disrupt the network by attempting to double-spend coins and/or censor transactions.
Centralization risks
While public blockchains aim for decentralization, in practice, factors like mining pools can centralize control and introduce vulnerabilities due to imbalances in the concentration of power. The centralization of infrastructure is also a point of concern. For instance, many blockchain nodes that validate transactions are run on centralized cloud services like Amazon Web Services. If centralized cloud infrastructure was targeted and a large portion of nodes were taken down, a network could become increasingly centralized and thus more vulnerable to other types of attacks.
Blockchain network congestion
This occurs when there are not enough validators to confirm the amount of proposed transactions, leading to delays in transaction processing and an increase in fees. In the worst cases, this can lead to downtime and instability, affecting confidence in the resiliency of a network.
Attacks on protocols and smart contracts that run on top of blockchain networks
Bridge attacks
Blockchain bridges are tools that connect and allow seamless transfer of assets between different blockchain networks, enhancing the decentralized finance (DeFi) ecosystem. Because bridges store a large amount of assets and are less secure than the blockchains themselves, they are an attractive target to hackers. According to our data, bridge attacks account for 70% of crypto cyber attacks.
Layer2 vulnerabilities
While many of the same general blockchain vulnerabilities apply, there are some considerations unique to L2s including the possibility of transaction censoring from rollup providers and DoS and malware attacks targeting rollup providers.
Protocol hacks and exploits
A particular concern in the realm of DeFi, protocol hacks can lead to significant financial losses and damage trust in the greater DeFi landscape. While security audits are commonly conducted to minimize risks, the intricate nature of these financial instruments means that vulnerabilities can easily slip through the cracks. A notable example is the BadgerDAO incident, where a hacker compromised a Cloudflare API key and was able to steal $120M in funds.
Other smart contract vulnerabilities
Coding flaws in smart contracts can be exploited in various ways. The DAO incident on Ethereum is a notable example. An attacker exploited a vulnerability in its smart contract, draining around a third of The DAO’s funds (valued at about $50 million at the time). This event led to a contentious hard fork in the Ethereum community, resulting in the creation of Ethereum (ETH) and Ethereum Classic (ETC).
Attacks on popular infrastructure and users
Popular software attacks
Crypto wallets and other popular pieces of software are often targeted by attackers. One notable example is an exploit on a popular Solana mobile wallet Slope, enabling an attacker to steal over $8M worth of SOL. This wallet was so widely used that for a time, it was thought that the Solana blockchain itself was compromised.
Centralized exchange hacks
Cryptocurrency exchanges, which are centralized platforms where users trade digital assets, have always been targets for hackers. One of the most famous incidents is the Mt. Gox hack in 2014, where approximately 850,000 bitcoins were stolen.
Malware
One method used by attackers is to infect a user’s computer with malware designed to steal wallet keys or perform unauthorized transactions. This can be as subtle as malware detecting when a cryptocurrency address is copied, and substituting that address with a bad actor’s wallet address when pasted.
Phishing attacks
Crypto phishing attacks exploit individuals by fooling them into divulging sensitive information, such as private keys or passwords, typically through a bogus website or message that appears authentic.
SIM swap attack
SMS is never recommended as a method for multi-factor authentication due to the possibility of a SIM swap attack. This happens when an unauthorized individual gains access to your SIM card details and transfers them to their own device, gaining control over accounts linked to your phone number. Some of these attacks have been carried out by scammers simply calling the service provider and pretending to be the account owner.
Social engineering scams
This occurs when an attacker convinces someone to send them cryptocurrency or divulge private keys and passwords under false pretenses.
User error
Losing private keys, accidentally revealing private keys, and sending assets to the wrong address are all risks that crypto users face, but these aren’t flaws in the blockchain itself.
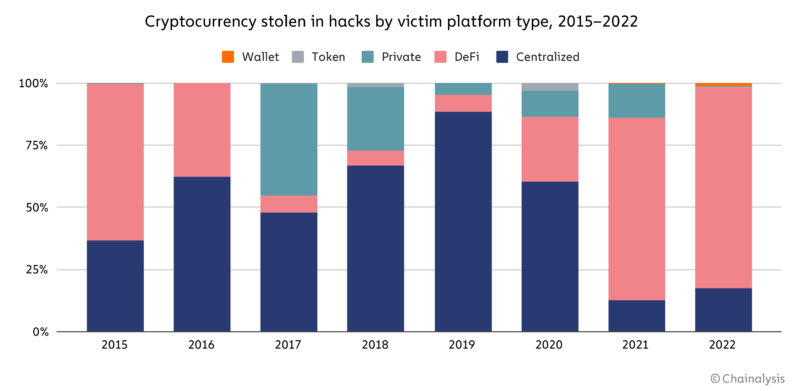
Attacks on DeFi protocols accounted for the majority of cryptocurrency stolen in hacks in 2021 and 2022.
Creating a robust blockchain security strategy
A comprehensive blockchain security plan should address not only technical considerations but also governance, risk management, and compliance. While the individual components of a successful blockchain security strategy vary depending on use-case, here are some universal considerations.
Understand the philosophical implications of blockchain and decentralization
While deep technical knowledge is not required to participate in a blockchain-enabled world, a foundational understanding of the core philosophy is helpful for effectively navigating it.
Blockchain is rooted in principles of open-source governance, trustless systems, and peer-to-peer interaction. Understanding the underlying philosophy can help you appreciate why and how blockchain can disrupt traditional business models and empower individual users and institutions. The internet built on blockchain is fundamentally different from the internet we know today. At scale, it endeavors to offer more control over personal data, greater security, and increased transparency in transactions. This shift implies not only technological changes but also social and economic shifts that will impact how we interact with the world at large.
Evaluate the stakes and risks
Before embarking on any blockchain project or investment, it’s important to understand the stakes and potential risks involved. These can range from financial losses due to volatile cryptocurrency markets to legal implications related to data storage and management.
Understand your use case and tailor your approach
Every blockchain strategy is unique. Whether you’re looking to streamline operations or create a secure voting system, understanding your specific use-case is the first step to support a successful blockchain security strategy.
Equip your organization with the proper tools
Identify the hardware and software you need to support your on-chain activities and thoroughly vet your vendors. After all, your security is only as good as your weakest link.
Think of your own clients. Have you considered what security clearances the tools and infrastructure you’re using have achieved? For instance, is it important for them to be SOC2, ISO 27001, or GDPR compliant?
Blockchain security and enterprises
When it comes to blockchain security in an enterprise setting, multiple strategies can come into play, ranging from identifying vulnerabilities in infrastructure to training employees in blockchain cybersecurity.
Access control mechanisms
Some companies choose to implement access control mechanisms, identifying who is authorized to interact with assets such as crypto wallets and private keys. Techniques like multi-factor authentication and encryption algorithms are commonly used to bolster security. Role-based access can be an effective way to limit the range of actions available to each user.
Shared transactional responsibilities
In order to minimize risks associated with fraud, errors, or conflicts of interest, many organizations choose to distribute transactional responsibilities among multiple individuals or teams.
Evaluating privacy and storage requirements
Privacy and storage needs vary by use-case. Some options include cold storage for long-term asset protection, and multi-signature (multisig) wallets for enhanced transactional security.
Contingency planning
Establishing fallback measures and backup plans can ensure that transactions and operations can continue smoothly in the event of system malfunctions, personnel unavailability, or other unforeseen circumstances. This might include alternative transaction authorization processes and data backup systems.
Monitoring and updating tools and technology
Ensuring the security, efficiency, and effectiveness of your tools and technology is a critical component of maintaining agile and resilient security infrastructure. Whether you are a small startup or a large enterprise, continuously monitoring and patching your software and hardware is extremely important.
Monitoring exposure
Many institutions deploy real-time monitoring to assess their exposure to various digital assets, protocols, and services and keep up with the latest security updates and news affecting those platforms.
Onboarding and continuing education for staff
Crypto moves at the speed of light. Regular knowledge and training programs can keep everyone on your team up to speed on best practices, technologies, and threats.
Blockchain custody, security, and reporting solutions
Custodial vs. non-custodial blockchain solutions
Non-custodial solutions like decentralized wallets provide a higher amount of control and autonomy, but they also come with increased responsibility for security.
Many institutions prefer to use the services of a trusted custodian to hold assets and/or facilitate transactions, which is functionally much like a bank. This eliminates the peer-to-peer benefits of crypto, but offers the assurance of institutional-grade security.
Assets held by custodians are often insured against hacks/exploits targeting the platform itself. It’s important to note that assets held on these platforms are typically not insured against theft due to a bad actor gaining access to your account, so it’s still important to practice good security hygiene like multi-factor authentication.
Blockchain security and intelligence solutions
As digital currencies enter the mainstream, tools for monitoring transactions, and combating crypto crime have become essential for businesses, law enforcement agencies, financial institutions, and regulatory bodies. These security solutions demonstrate the growing maturity of the blockchain ecosystem and the commitment to strengthening operations and promoting widespread adoption.
Blockchain forensics involves examining blockchain data to identify suspicious activities, trace funds, and ensure compliance with regulations. Organizations rely on Chainalysis to handle these activities. Additionally, we provide an incident response retainer to promptly intervene and collaborate with law enforcement in the unfortunate event of a hack to recover stolen assets.
Blockchain reporting solutions
Financial transactions and key operational actions often need to be documented for audit trails, compliance, and legal requirements. While manual accounting is an option, leveraging technology solutions from specialized crypto accounting service providers can greatly streamline this process, reducing the risk of human error and enhancing operational efficiency.
Blockchain security: Regulatory and legal considerations
As blockchain technology becomes more integrated into the mainstream, global leaders are grappling with how to negotiate the dance between innovation and regulation. On one hand, there’s a need to ensure that blockchain systems comply with existing laws, especially those concerning anti-money laundering (AML), consumer protection laws, sanctions compliance, and tax and reporting requirements.
On the other hand, there’s sentiment to not stifle innovation with overregulation. Upholding the security and integrity of blockchain systems, while also providing a conducive environment for their growth is a complex regulatory challenge.
Although regulations surrounding digital assets are still evolving, compliance is not optional. Make sure that you’re up-to-date with current laws and reporting requirements in your jurisdiction. This may involve working closely with legal and compliance teams to ensure that all activities are in line with regulatory standards.
Lowering the barriers to entry and ensuring institutions feel secure and compliant when entering the crypto space is key for mass adoption. Compliance may seem like an overwhelming endeavor, but organizations have risen to meet the dynamic challenges of an on-chain world with Chainalysis. From free sanctions screening on-chain oracles and APIs to continuous transaction monitoring for all forms of risk, Chainalysis provides tailor-made solutions to effectively navigate compliance challenges.
The future of blockchain security
As the ecosystem continues to develop and mature, blockchain security will continue to evolve in tandem. We can anticipate:
- Enhanced frameworks for cybersecurity tailored for specific blockchain applications.
- A united effort from tech communities, governments, and organizations to establish global cybersecurity standards.
- The opportunity to build and innovate in public thanks to the shift towards decentralization.
Chainalysis amplifies this vision as the leading blockchain data platform. Serving clients in over 70 countries — including government agencies, financial institutions, and crypto firms — we offer a range of solutions from data and technology, to research and training. We’re committed to building trust in blockchain ecosystems, aiming to maximize financial freedom while minimizing risk.
By harnessing collective wisdom, distributed ownership, and transparency, together we can bolster trust, spur innovation, and create robust, resilient systems.
This material is for informational purposes only, and is not intended to provide legal, regulatory, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.

