TL;DR
- North Korean hackers stole $2.02 billion in cryptocurrency in 2025, a 51% year-over-year increase, pushing their all-time total to $6.75 billion despite fewer attacks.
- The DPRK is achieving larger thefts with fewer incidents, often by embedding IT workers inside crypto services or using sophisticated impersonation tactics targeting executives.
- The DPRK shows clear preferences for Chinese-language money laundering services, bridge services, and mixing protocols, with a 45-day laundering cycle following major thefts.
- Individual wallet compromises surged to 158,000 incidents affecting 80,000 unique victims in 2025, though total value stolen ($713M) decreased from 2024.
- Despite increased Total Value Locked in DeFi, hack losses remained suppressed in 2024-2025, suggesting improved security practices are making a meaningful difference.
The cryptocurrency ecosystem faced another challenging year in 2025, with stolen funds continuing their upward trajectory. Our analysis reveals a shift in crypto theft patterns, characterized by four key developments: the persistence of the Democratic People’s Republic of Korea (DPRK) as a primary threat actor, the growing severity of individual attacks on centralized services, a surge in personal wallet compromises, and an unexpected divergence in decentralized finance (DeFi) hack trends.
These patterns emerge clearly from the data and reveal significant changes in how crypto theft is occurring across different platform types and victim categories. As digital asset adoption expands and valuations reach new heights, understanding these evolving security threats has become increasingly critical.
The big picture: Over $3.4 billion stolen in 2025
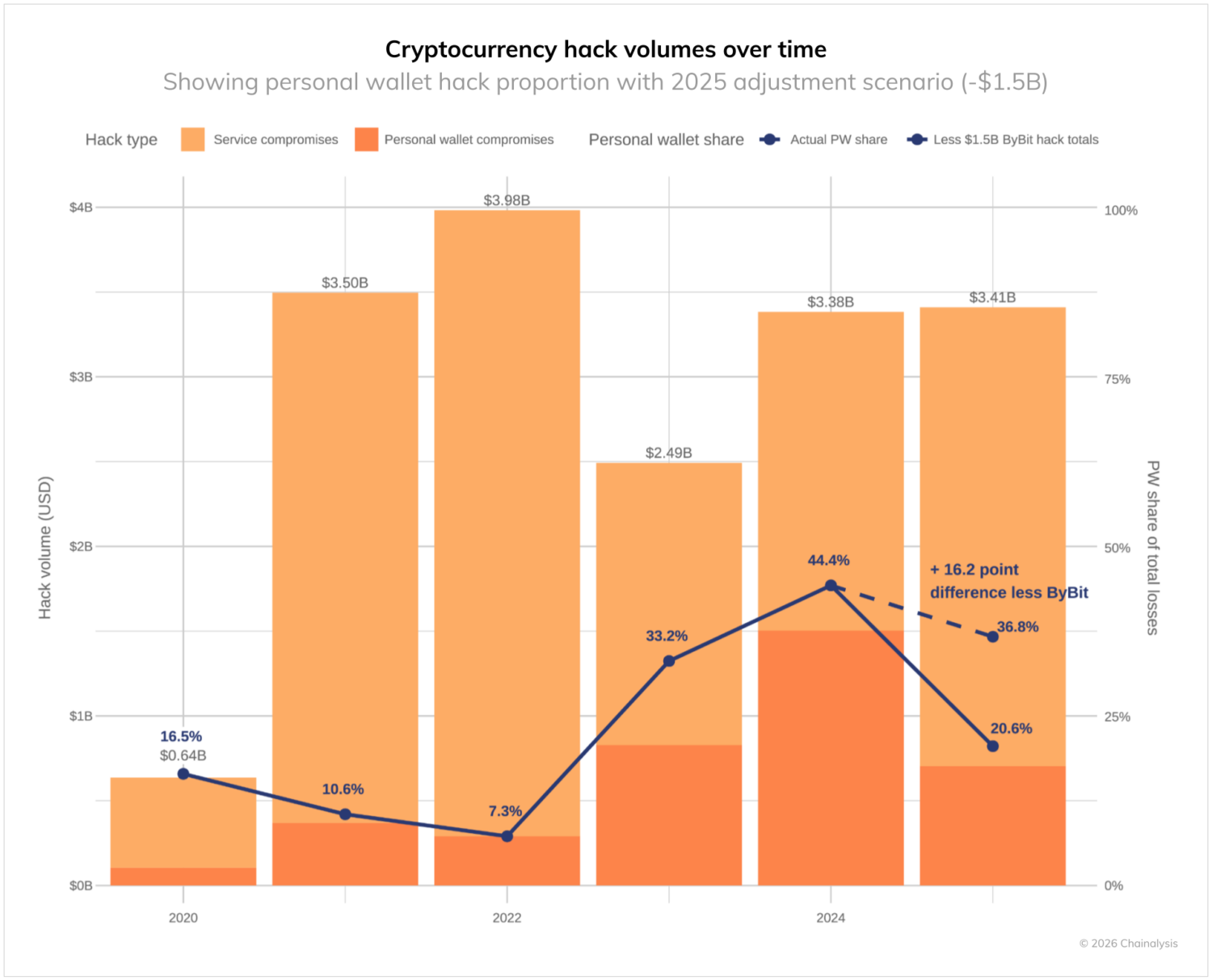
The cryptocurrency industry witnessed over $3.4 billion in theft from January through early December 2025, with the February compromise of Bybit alone accounting for $1.5 billion of that total.
Beyond the headline figure, the data reveal important shifts in the composition of these thefts. Personal wallet compromises have grown substantially, increasing from just 7.3% of total stolen value in 2022 to 44% in 2024. In 2025, the share would have been 37% if it weren’t for the outsized impact of the Bybit attack.
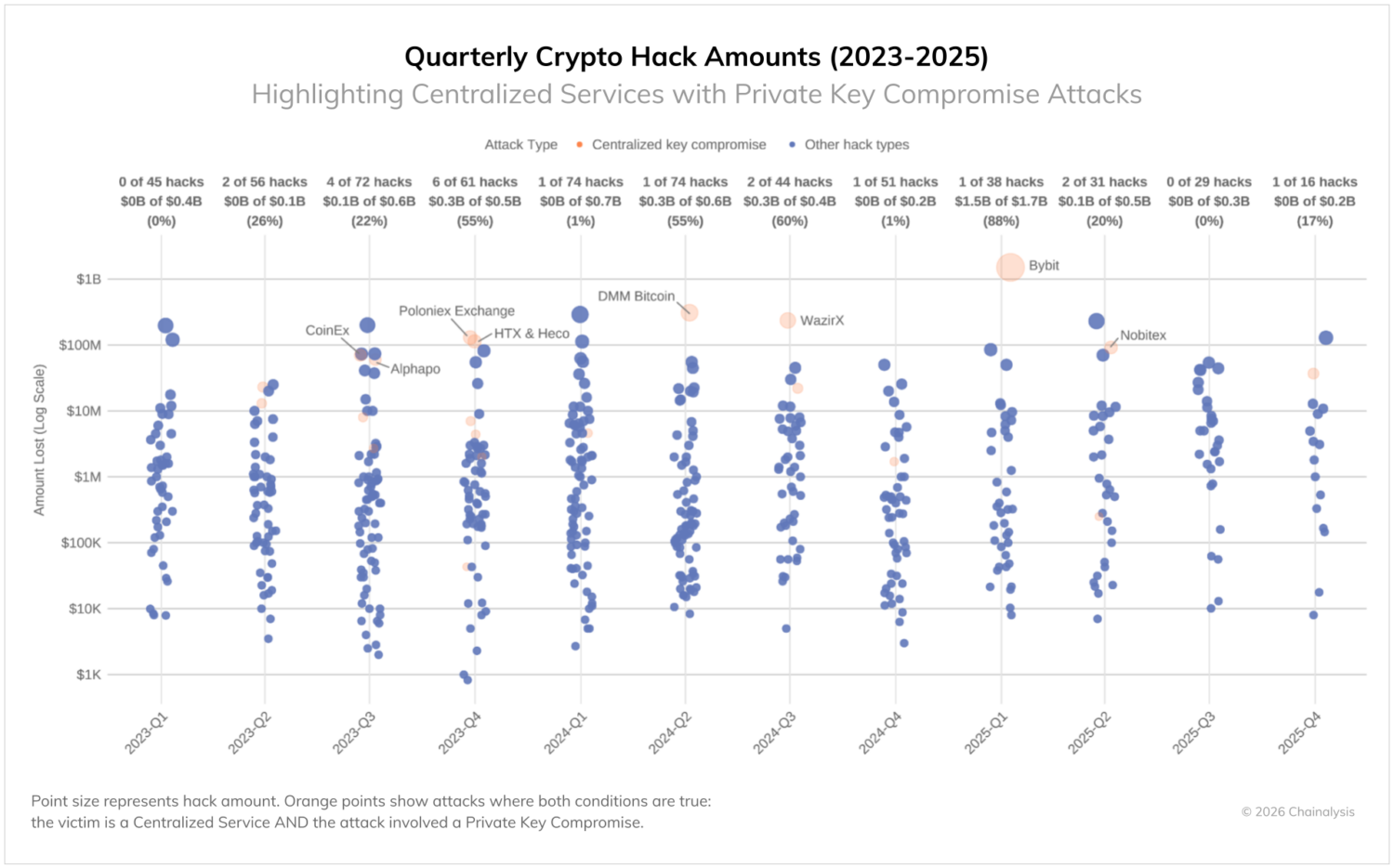
Meanwhile, centralized services are experiencing increasingly large losses due to sophisticated attacks on private key infrastructure and signing processes. Despite their institutional resources and professional security teams, these platforms remain vulnerable to advanced threats that can circumvent cold wallet controls. While such compromises are infrequent (as shown in the chart below), their scale still drives enormous shares of stolen volumes when they do occur, accounting for 88% of losses in Q1 2025. Many attackers have developed methods to exploit third-party wallet integrations and trick legitimate signers into authorizing malicious transactions.
The persistence of high theft volumes indicates that while some areas of crypto security may be improving, attackers continue to find success across multiple vectors.
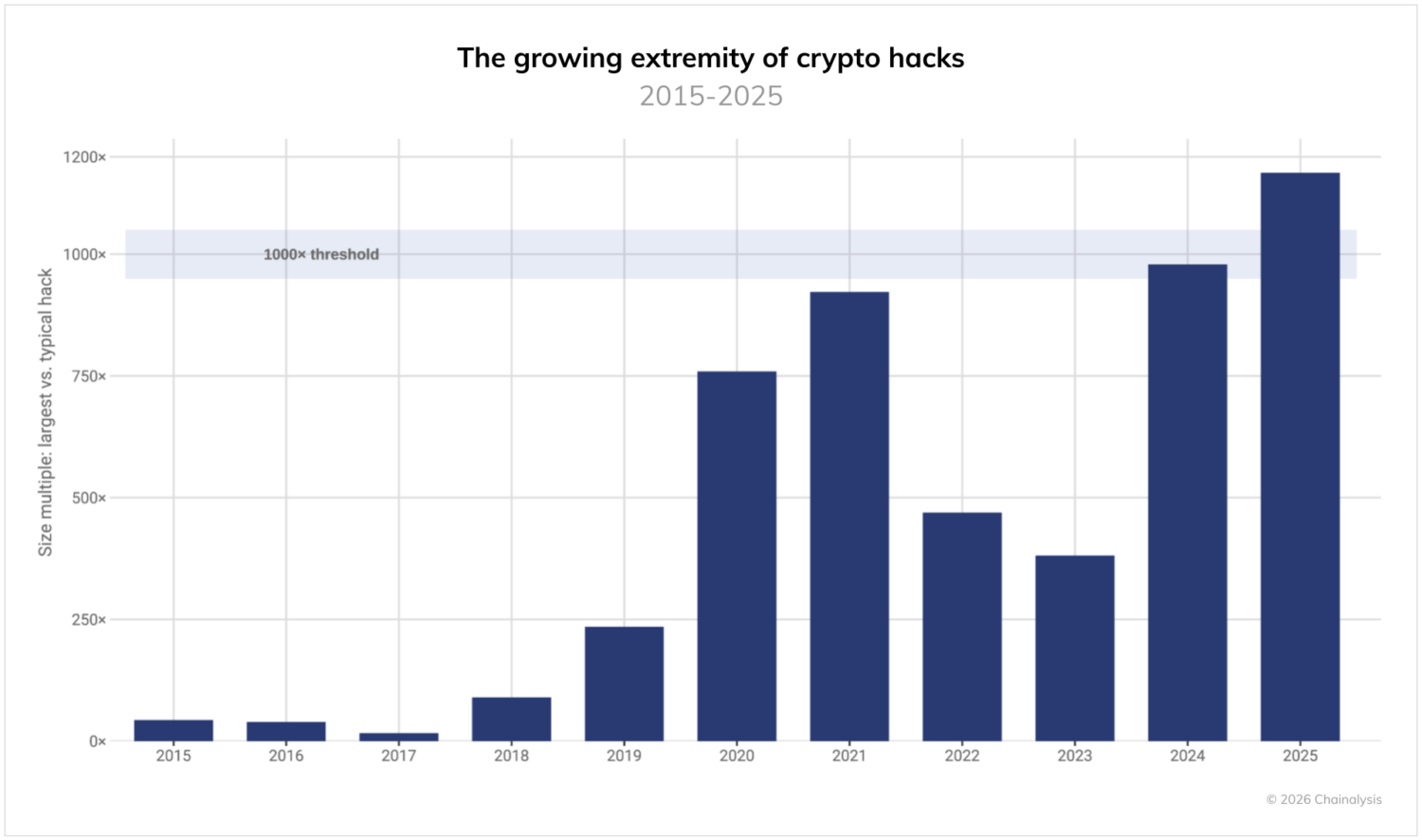
Top three hacks account for 69% of losses as outliers reach 1,000 times the median
Stolen fund activity has always been outlier-driven, with most hacks relatively small and some immense. But 2025 reveals a striking escalation: the ratio between the largest hack and median of all incidents has crossed the 1,000x threshold for the first time. Funds stolen in the largest attacks are now 1,000 times larger than those stolen in the typical incident, surpassing even the 2021 bull market peak. These calculations are based on the USD values of funds stolen at the time of their theft.
This growing discrepancy has concentrated losses dramatically. The top three hacks in 2025 account for 69% of all service losses, creating a landscape where individual incidents have an outsized impact on yearly totals. While the number of incidents may fluctuate and median losses grow with asset prices, the potential for catastrophic individual breaches is escalating faster still.
North Korea remains dominant crypto threat actor, despite fewer confirmed incidents
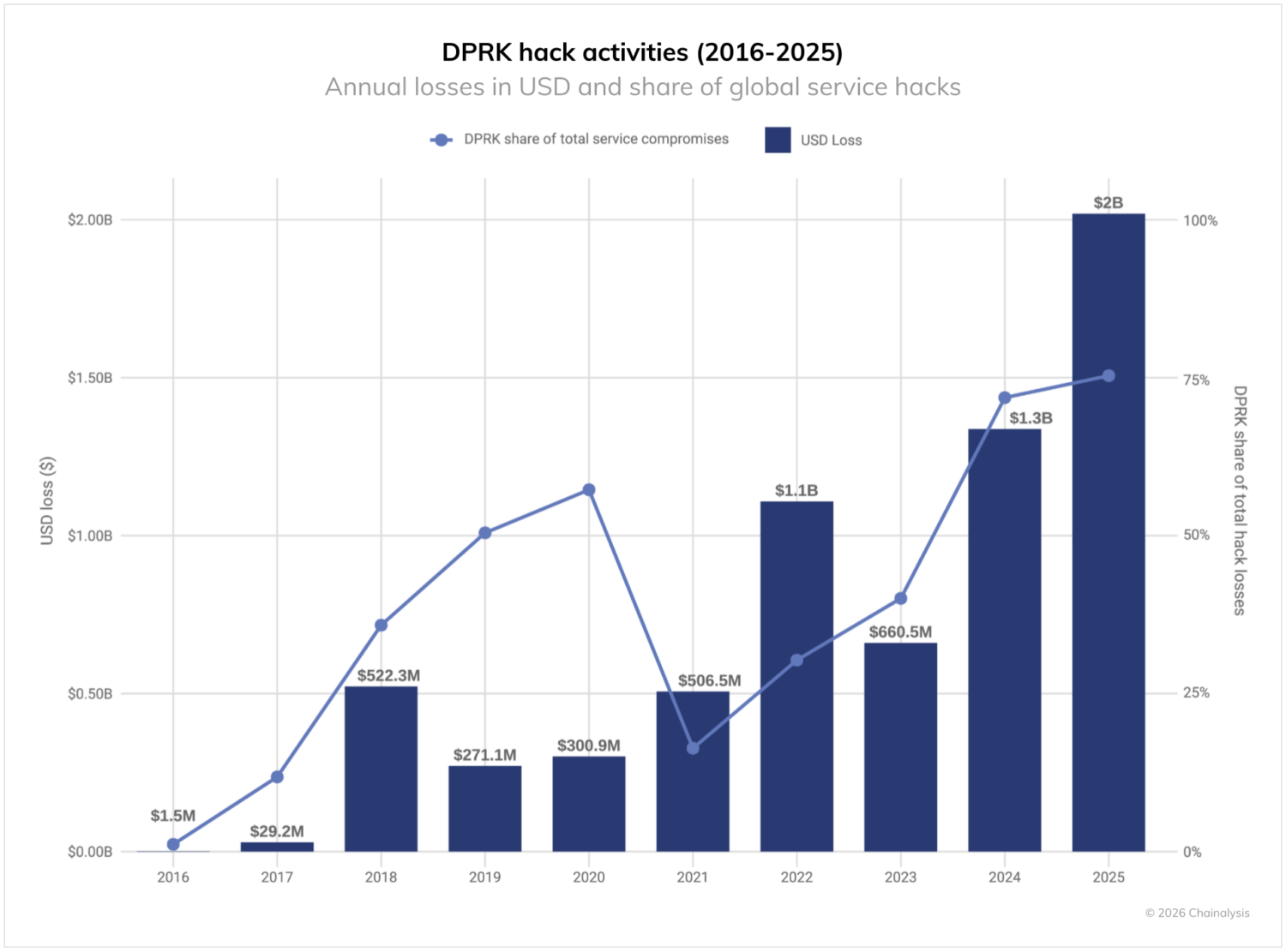
The Democratic People’s Republic of Korea (DPRK) continues to pose the most significant nation-state threat to cryptocurrency security, achieving a record-breaking year for stolen funds despite an assessed dramatic reduction in attack frequency. In 2025, North Korean hackers stole at least $2.02 billion in cryptocurrency ($681 million more than 2024), representing a 51% increase year-over-year. This marks the most severe year on record for DPRK crypto theft in terms of value stolen, with DPRK attacks also accounting for a record 76% of all service compromises. Overall, 2025’s numbers bring the lower-bound cumulative estimate for cryptocurrency funds stolen by the DPRK to $6.75 billion.
North Korean threat actors are increasingly achieving these outsized results often by embedding IT workers – one of DPRK’s principal attack vectors – inside crypto services to gain privileged access and enable high‑impact compromises. Part of this record year likely reflects an expanded reliance on IT worker infiltration at exchanges, custodians, and web3 firms, which can accelerate initial access and lateral movement ahead of large‑scale theft.
More recently, however, DPRK-linked operators have flipped this IT worker model on its head. Instead of merely applying for roles and embedding themselves as employees, they are increasingly impersonating recruiters for prominent web3 and AI firms, orchestrating fake hiring processes that culminate in “technical screens” designed to harvest credentials, source code, and VPN or SSO access to the victim’s current employer. At the executive level, a similar social‑engineering playbook appears in the form of bogus outreach from purported strategic investors or acquirers, who use pitch meetings and pseudo–due diligence to probe for sensitive systems information and potential access paths into high‑value infrastructure — an evolution that builds directly on the DPRK’s IT worker fraud operations and their focus on strategically important AI and blockchain companies.
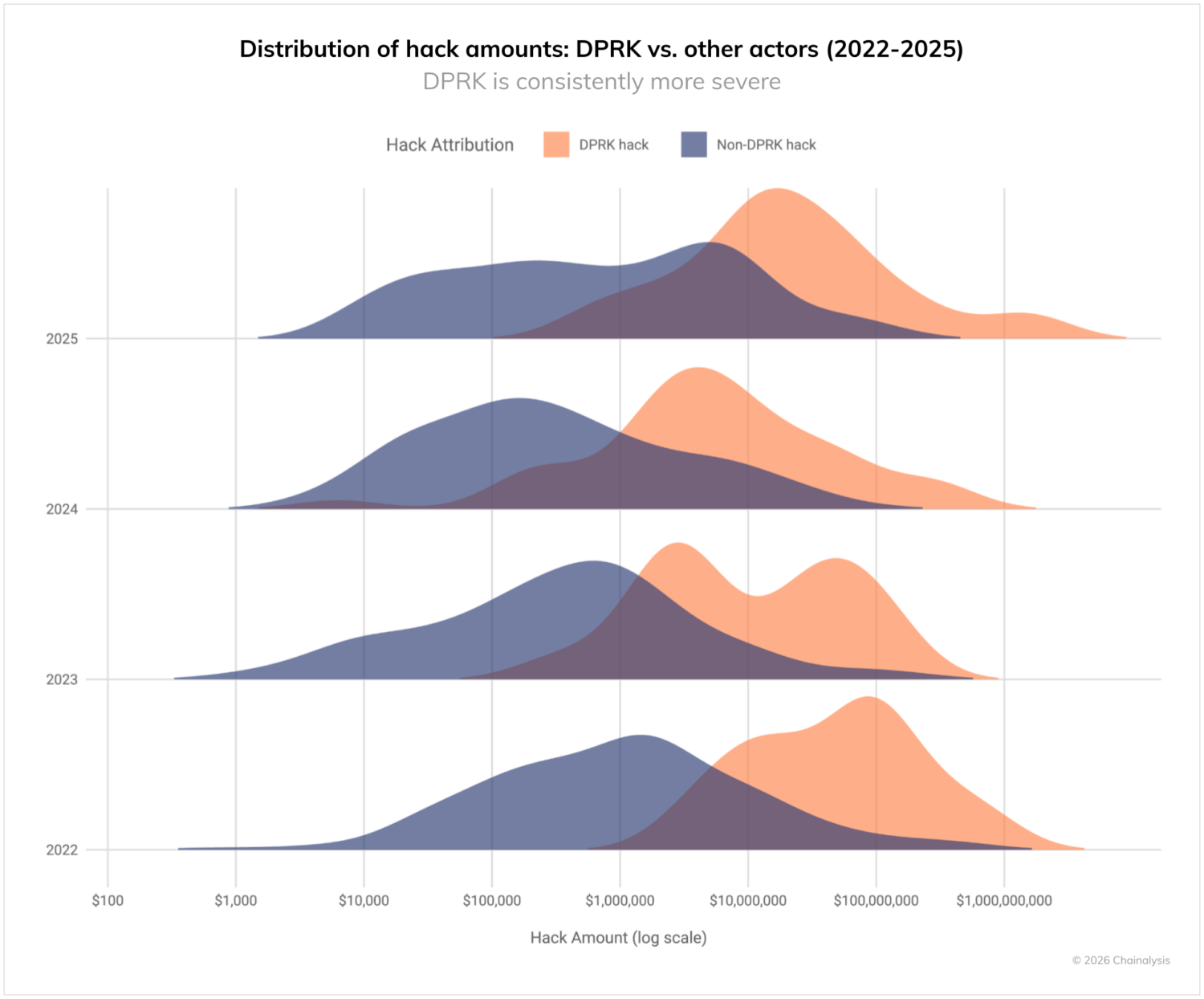
As we have seen in years past, the DPRK continues to undertake significantly higher-value attacks than other threat actors. As shown in the chart below, from 2022-2025, DPRK-attributed hacks occupy the highest value ranges, while non-DPRK hacks show more normal distributions across all theft sizes. This pattern reinforces that when North Korean hackers strike, they target large services and aim for maximum impact.
This year’s record haul came from significantly fewer known incidents. This shift — fewer incidents yielding far greater returns — reflects the impact of the massive Bybit hack in February 2025.
The DPRK’s distinctive laundering patterns
The massive influx of stolen funds in early 2025 provides unprecedented visibility into how DPRK-linked actors launder cryptocurrency at scale. Their patterns differ markedly from those of other cybercriminals and evolve over time, revealing current operational preferences and potential vulnerabilities.
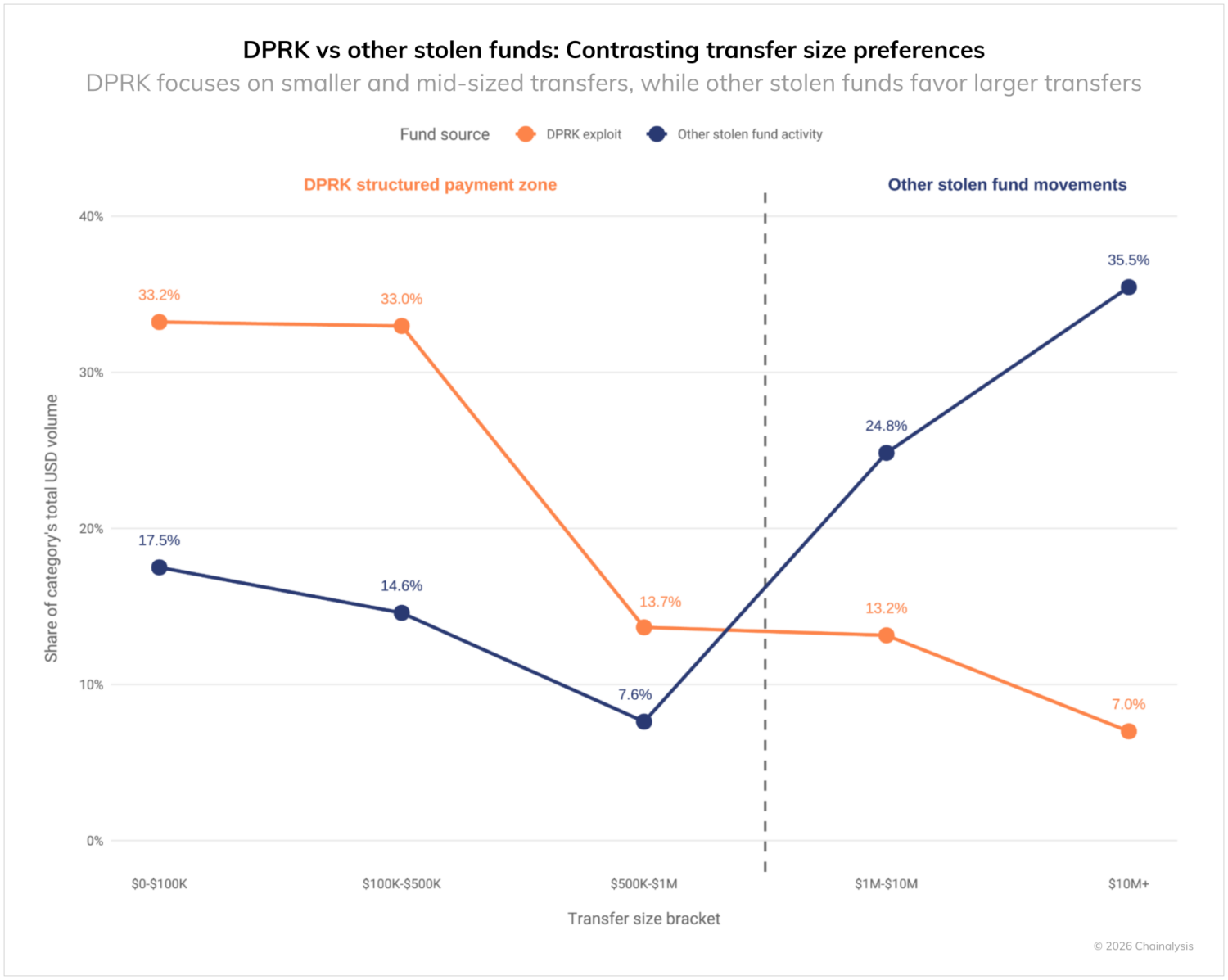
DPRK laundering shows distinctive bracketing patterns, with slightly over 60% of volume concentrated below a $500,000 transfer value. In contrast, other stolen fund actors send over 60% of their funds on-chain in tranches in the $1M to $10M+ range. Even while the DPRK consistently steals larger amounts than other stolen fund threat actors, they structure on-chain payments in smaller tranches, speaking to the sophistication of their laundering.
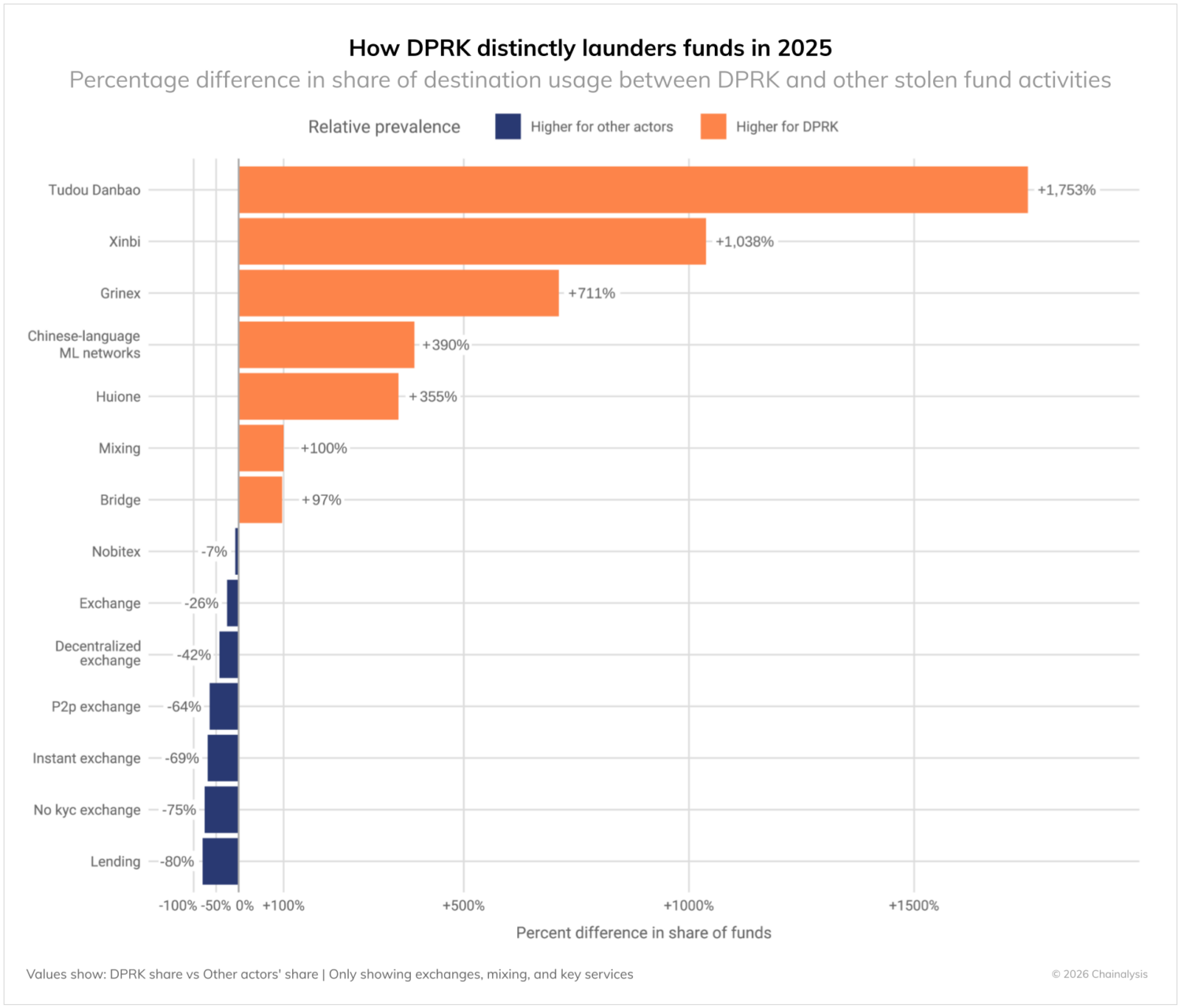
Compared to other stolen fund actors, the DPRK shows clear preferences for certain laundering touchpoints:
DPRK hackers tend to strongly prefer:
- Chinese-language money movement and guarantee services (+355% to +1000%+): Their most distinctive characteristic, showing heavy reliance on Chinese-language guarantee services and money laundering networks comprised of many different laundering operators that may have weaker compliance controls
- Bridge services (+97% difference): Heavy reliance on cross-chain bridges to move assets between blockchains and attempt to complicate tracing
- Mixing services (+100% difference): Greater use of mixing services to attempt to obscure the flow of funds
- Specialized services like Huione (+356%): Strategic use of specific services that facilitate their laundering operations
Other stolen fund actors tend to strongly prefer:
- Lending protocols (-80% difference): DPRK avoids these DeFi services, showing limited integration with the broader DeFi ecosystem
- No KYC exchanges (-75% difference): Surprisingly, other threat actors use KYC-free exchanges more than DPRK
- P2P exchanges (-64% difference): DPRK shows limited interest in peer-to-peer platforms
- Centralized exchanges (-25% difference): Other criminals display more direct interactions with conventional exchange platforms
- Decentralized exchanges (DEXs) (-42% difference): Other threat actors strongly prefer DEXs for their liquidity and pseudonymity
These patterns suggest that the DPRK operates under different constraints and objectives than those of non-state-backed cybercriminals. Their heavy use of professional Chinese-language money laundering services and over-the-counter (OTC) traders suggests that DPRK threat actors are tightly integrated with illicit actors across the Asia-Pacific region, and is consistent with Pyongyang’s historical use of China-based networks to gain access to the international financial system.
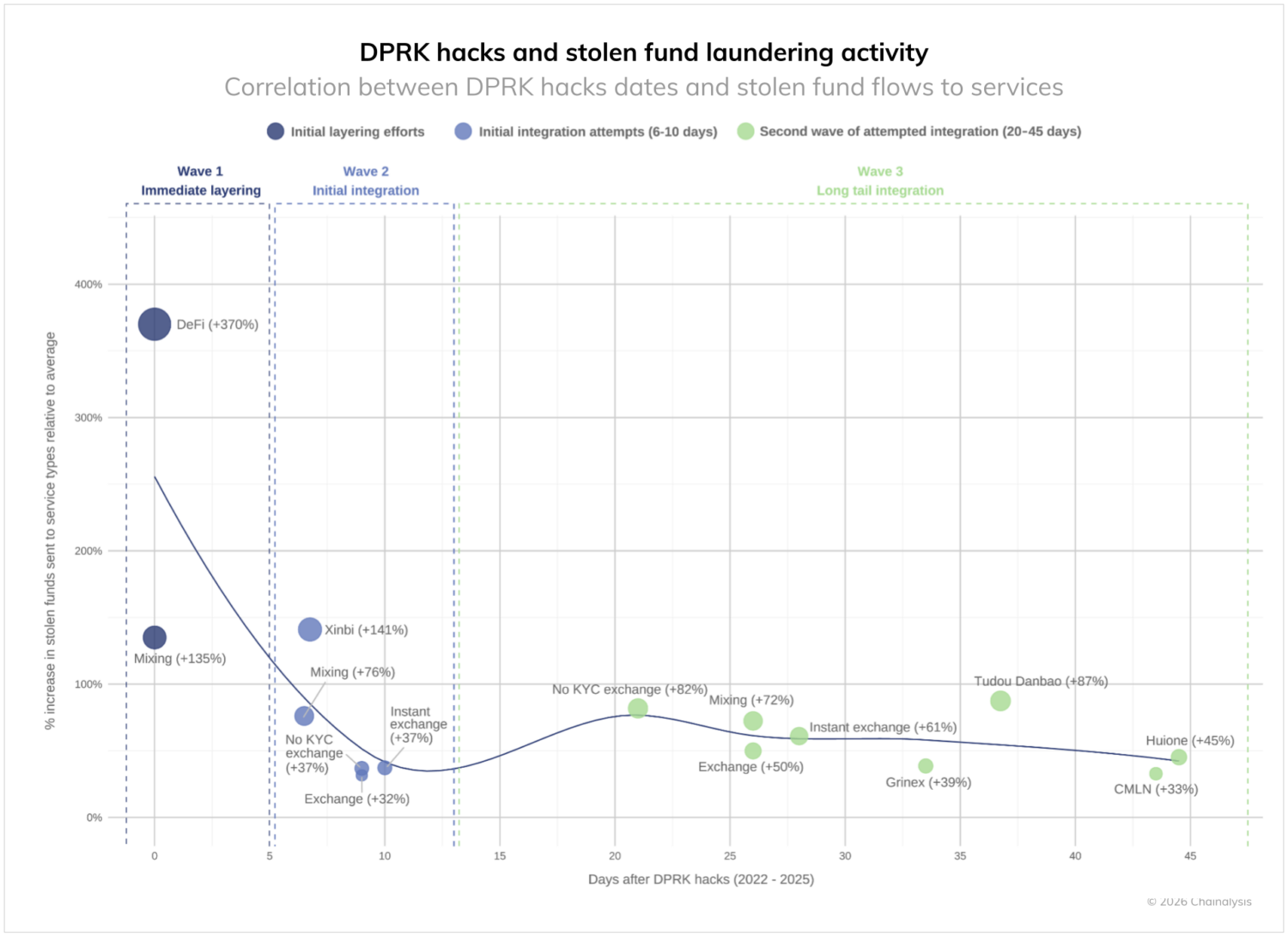
The timeline of stolen fund laundering post-DPRK hacks
Our analysis of on-chain activity following DPRK-attributed hacks reveals a consistent pattern in how these events are associated with the movement of stolen funds throughout the cryptocurrency ecosystem. Following major theft events between 2022-2025, stolen funds follow a structured, multi-wave laundering pathway that unfolds over approximately 45 days:
Wave 1: Immediate layering (days 0-5)
During the initial days after a hack, we observe an extraordinary spike in activity focused on immediate distancing of funds from the theft source:
- DeFi protocols see the most dramatic increase (+370%) in stolen fund flows, serving as the primary entry point
- Mixing services experience substantial volume increases (+135-150%), creating the first layer of obfuscation
- This phase represents urgent “first-move” efforts to establish distance from the original theft
Wave 2: Initial integration (days 6-10)
As the second week begins, the strategy shifts toward services that can help integrate funds into the broader ecosystem:
- Exchanges with limited KYC (+37%) and centralized exchanges (+32%) begin receiving flows
- Second-tier mixing services (+76%) continue the laundering process at reduced intensity
- Cross-chain bridges like XMRt (+141%) help fragment and obscure fund movement across blockchains
- This phase represents the critical transitional period where funds begin moving toward potential off-ramps
Wave 3: Long tail integration (days 20-45)
The final phase shows clear preference for services that can facilitate ultimate conversion to fiat or other assets:
- No-KYC exchanges (+82%) and guarantee services like Tudou Danbao (+87%) see significant increases
- Instant exchanges (+61%) and Chinese-language platforms like Huione (+45%) serve as final conversion points
- Centralized exchanges (+50%) also receive funds, suggesting sophisticated attempts to mix with legitimate flows
- Less regulated jurisdictions represented by platforms such as Chinese-language money laundering networks (+33%) and Grinex (+39%) complete the pattern
This general 45-day window for laundering operations provides crucial intelligence for law enforcement and compliance teams. The pattern’s persistence across multiple years indicates operational constraints facing DPRK-linked actors, likely related to their limited access to financial infrastructure and need to coordinate with specific facilitators.
While these actors don’t always follow this exact timeline—some stolen funds remain dormant for months or years—this pattern represents their typical on-chain behavior when actively laundering proceeds. It’s also important to acknowledge potential blind spots in this analysis, as certain activities like private key transfers or OTC crypto-for-fiat sales wouldn’t be visible on-chain without corroborative intelligence.
Personal wallet compromises: The escalating threat to individual users
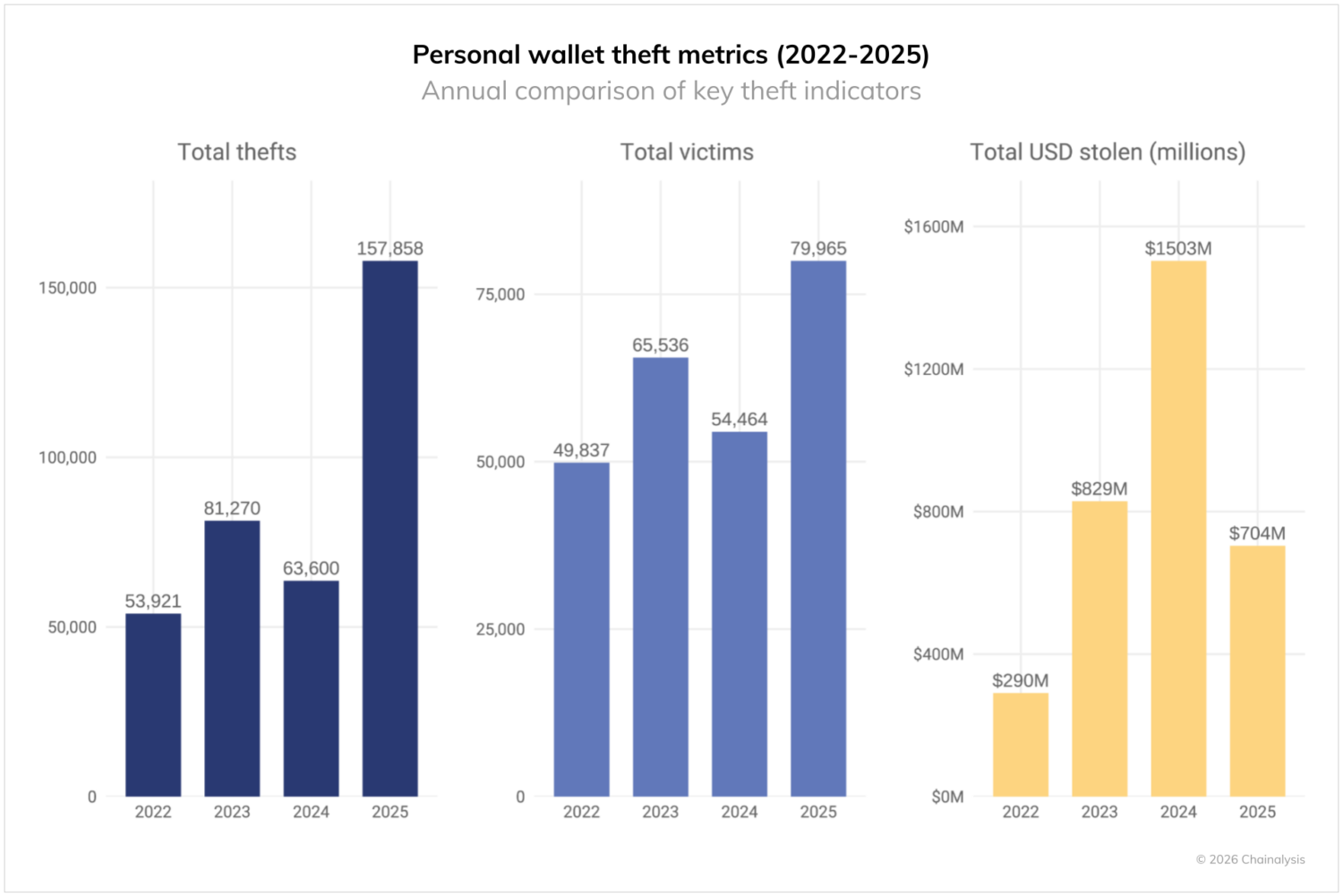
Through analysis of on-chain patterns, in addition to reporting from victims and industry partners, we can gain an understanding of the magnitude of personal wallet compromises, although the true number of compromises is likely far greater. Based on our lower bound estimates, personal wallet compromises now account for 20% of all value stolen in 2025, down from 44% of the total in 2024, representing an evolution in both scale and pattern. Total theft incidents surged to 158,000 in 2025, nearly triple the 54,000 recorded in 2022. Unique victims increased from 40,000 in 2022 to at least 80,000 in 2025. These dramatic increases are likely due to greater crypto adoption. For example, Solana, one of the blockchains with the greatest number of active personal wallets, had by far the largest number of incidents (~26,500 victims).
Yet despite more incidents and victims, the total USD value stolen from individual victims actually declined from 2024’s peak of $1.5 billion to $713 million in 2025. This suggests that attackers are targeting more users, but stealing smaller amounts per victim.
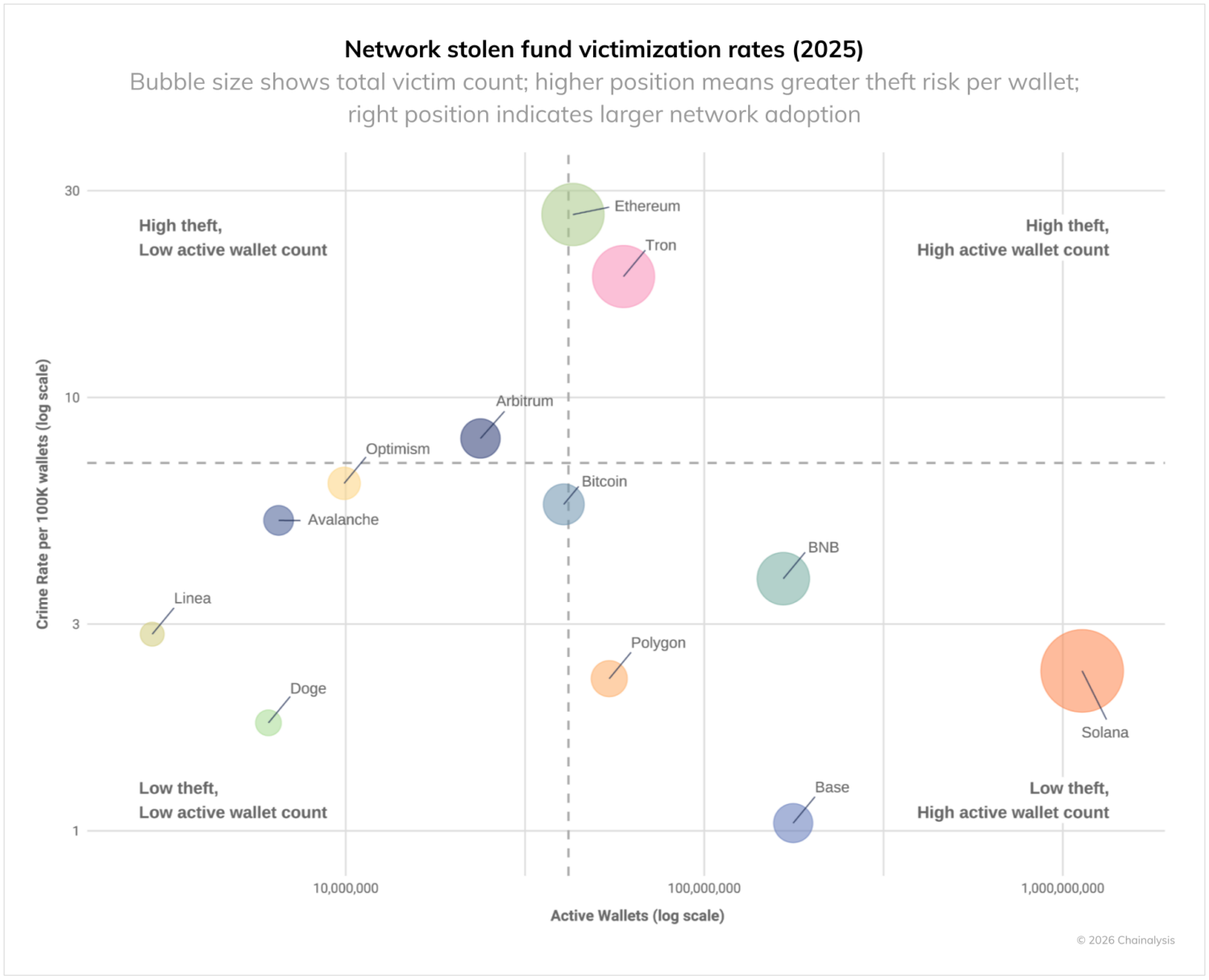
Network-specific victimization data provides additional insight into which domains present the greatest risk to crypto users. The chart below presents victimization data adjusted for active personal wallets across networks. When measuring crime rates per 100K wallets in 2025, Ethereum and Tron show the highest rates of theft. Ethereum’s large size indicates both high rates of theft and high victim count, while Tron’s position shows elevated rate of theft despite a smaller active wallet base. In contrast, Base and Solana show lower victimization rates despite significant user bases.
These measurable differences highlight that personal wallet security risks are not uniform across the crypto ecosystem. The variation in victimization rates across chains with similar technical architectures suggests that factors beyond technology — such as user demographics, popular applications, and criminal infrastructure — play important roles in determining theft rates.
DeFi hacks: A diverging pattern signals market shift
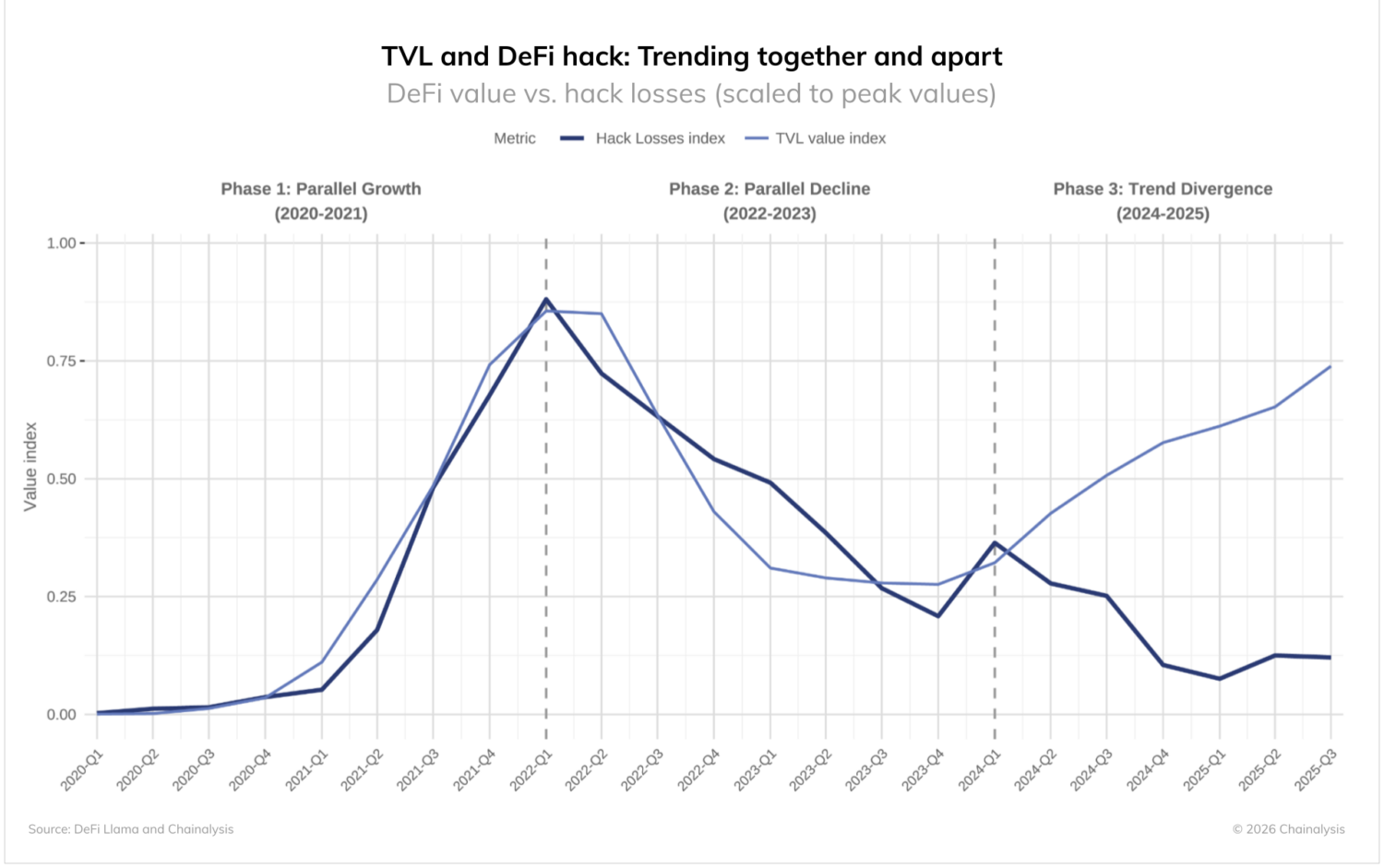
The DeFi sector presents a unique pattern in 2025’s crime data, showing a clear divergence from historical trends.
The data reveal three distinct phases:
- Phase 1 (2020-2021): DeFi total value locked (TVL) and hack losses grew in parallel
- Phase 2 (2022-2023): Both metrics declined together
- Phase 3 (2024-2025): TVL recovered while hack losses remained suppressed
The first two phases follow an intuitive pattern: greater value at risk means both more value to steal and greater criminal effort targeting high-value protocols. As the infamous bank robber Willie Sutton supposedly said: “Because that’s where the money is.”
This makes Phase 3’s divergence from historical precedent all the more notable. DeFi TVL has recovered significantly from its 2023 lows, yet hack losses have not followed suit. The sustained lower level of DeFi hacks even as billions of dollars have returned to these protocols represents a meaningful change.
Two factors may explain this divergence:
- Improved security: Consistently lower hack rates despite growing TVL suggest that DeFi protocols may be implementing more effective security measures compared to the 2020-2021 period.
- Target substitution: The concurrent rise in personal wallet thefts and centralized service compromises suggests that attacker attention may be shifting to alternative targets.
Case study: Venus Protocol’s security response
The Venus Protocol incident of September 2025 exemplifies how improved security practices are making a tangible difference. When attackers used a compromised Zoom client to gain system access and manipulate a user into granting delegate status over a $13 million account, the outcome could have been catastrophic. However, Venus had onboarded Hexagate‘s security monitoring platform just one month prior.
The platform detected suspicious activity 18 hours before the attack and generated another alert as soon as the malicious transaction occurred. Within 20 minutes, Venus had paused its protocol, preventing any fund movements. The coordinated response demonstrated the evolution of DeFi security:
- Within 5 hours: Partial functionality restored after security checks
- Within 7 hours: Force-liquidation of the attacker’s wallet
- Within 12 hours: Full recovery of stolen funds and service resumption
Most remarkably, Venus passed a governance proposal to freeze $3 million in assets still controlled by the attacker; the attacker not only failed to profit, but actually lost money, as well.
This incident illustrates tangible improvements in DeFi security infrastructure. The combination of proactive monitoring, rapid response capabilities, and governance mechanisms that can act decisively has made the ecosystem more agile and resilient. While attacks still occur, the ability to detect, respond, and even reverse them represents a fundamental shift from the early DeFi era when successful hacks often meant permanent losses.
Implications for 2026 and beyond
The 2025 data present a complex picture of DPRK’s evolution as a crypto threat actor. The nation state’s ability to execute fewer but far more damaging attacks demonstrates increasing sophistication and patience. The Bybit incident’s impact on its yearly activity patterns suggests that when DPRK successfully executes a major theft, it reduces operational tempo to focus on laundering the proceeds.
For the cryptocurrency industry, this evolution demands enhanced vigilance around high-value targets and improved detection of DPRK’s specific laundering patterns. Their consistent preferences for certain service types and transfer amounts provide detection opportunities, distinguish them from other criminals, and can help investigators identify their on-chain behavioral footprint.
As North Korea continues to use cryptocurrency theft to fund state priorities and circumvent international sanctions, the industry must recognize that this threat actor operates by different rules than typical cybercriminals. The country’s record-breaking 2025 performance — achieved with 74% fewer known attacks — suggests we may be seeing only the most visible portion of its activities. The challenge for 2026 will be detecting and preventing these high-impact operations before DPRK-affiliated actors inflict another Bybit-scale incident.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.