TL;DR
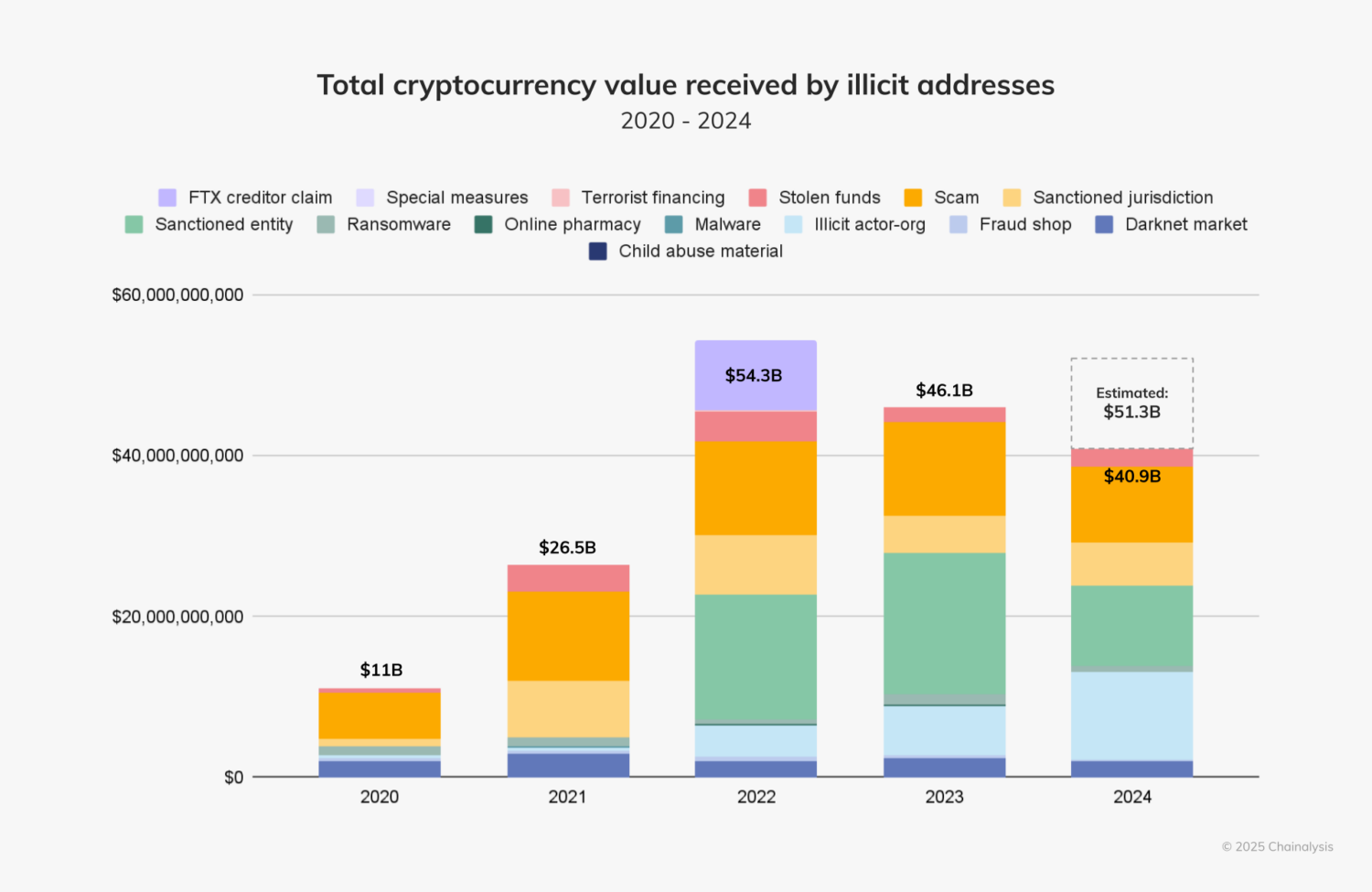
- Illicit cryptocurrency addresses received approximately $40.9 billion in 2024, highlighting the urgent need for stronger blockchain security.
- Key threats to the ecosystem include smart contract exploits, oracle manipulation, bridge attacks, phishing, and social engineering.
- Real-time blockchain analytics and tools like Chainalysis Hexagate are helping teams detect and stop attacks before they occur.
- Proactive, data-driven security strategies are essential for protecting user trust and enabling safe blockchain adoption at scale.
In our 2025 Crypto Crime Report, we estimated that illicit cryptocurrency addresses received $40.9 billion in 2024. At first glance, this appears to mark a decline from the previous year’s $46.1 billion. However, our 2024 figures reflect-lower bound estimates based on identified illicit addresses — when accounting for likely undiscovered activity, the true number is closer to $51.3 billion. In other words, crypto crime intensified.
As blockchain adoption accelerates and decentralized infrastructure expands, so does the attack surface. With every new protocol, smart contract, and wallet user added to the ecosystem, the need for robust blockchain security grows more urgent. Innovation has opened the doors to remarkable possibilities, but also to a new era of sophisticated threats.
From smart contract exploits and cross-chain bridge hacks, to phishing campaigns that drain users wallets, the risks facing blockchain technology are evolving in real time. However, with the right tools, many attacks can be stopped before they strike. In this blog, we’ll explore the most pressing blockchain security challenges and the steps participants can take now to build more resilient infrastructure.
Keep reading to learn more about the following topics:
- What is blockchain security?
- How are blockchain secured?
- Challenges in securing blockchains
- Common types of blockchain threats
- The role of blockchain analytics in preventing attacks
- Blockchain threat prevention with Chainalysis Hexagate
- Why blockchain security is critical for adoption
What is blockchain security?
Blockchain security refers to the combination of cybersecurity principles, tools, and best practices aimed at mitigating risk, avoiding malicious attacks, and preventing unauthorized access while operating on blockchain networks.
While all blockchains run on distributed ledger technology (DLT), not all blockchains are functionally the same or equally secure. Both public and private blockchains have their own sets of advantages and disadvantages, and their security models are fundamentally different due to the open versus closed nature of their networks.
Public blockchain security
Public blockchains like Bitcoin and Ethereum are open, permissionless networks where anyone can join and participate in validating transactions. The codebase of public blockchains is open source — publicly available and continually vetted by developers who review the code for bugs, vulnerabilities, and other issues. By leveraging the expertise of open-source communities, the security, features, and efficiency of these blockchains are continuously examined and improved. At the same time, hackers and malicious entities also examine code to search for vulnerabilities to exploit.
Private blockchain security
In contrast, private blockchains are exclusive, permissioned networks with limited access, making them more centralized. Securing a private blockchain is the sole responsibility of the operating entity. The centralized nature of these blockchains means that there is a single point of failure, making it crucial for the institution to implement strong security measures.
Although private blockchains may not benefit as much from the decentralized and security-by-numbers approach of public blockchains, they are generally faster and more efficient due to less computational work required for consensus algorithms. However, because the entity granting permission also has authority over the network, there is a theoretical risk of the network being shut down or manipulated.
How are blockchains secured?
Blockchain technology runs on a distributed digital ledger system. A blockchain network is made up of a worldwide network of computers, known as nodes, validating and recording transactions. Every participant maintains a copy of the ledger, so there is no centralized authority or point of failure. Each time a transaction occurs — such as sending or receiving cryptocurrency — it is recorded on a block.
Before a block (made up of a group of transactions that occurred during a given time frame) is added to the chain, it must first be verified by consensus. That’s where consensus mechanisms, such as Proof-of-Work and Proof-of-Stake, come into play. In a Proof-of-Work system, miners compete to solve computationally intensive algorithms to validate transactions. In a Proof-of-Stake system, network participants lock up a certain quantity of tokens to run a node to validate transactions. Miners and stakers are incentivized with rewards to secure the network. This process ensures everyone agrees (or reaches consensus) on the validity of each transaction. Once a block is full, it is sealed and linked to the previous block using a cryptographic code, forming a chain. By linking each block using cryptography and distributing the ledger across numerous computers, any attempt to tamper with a block would disrupt the entire chain.
How are transactions on a blockchain secured?
Unlike traditional finance — which operates on permissions to pull funds — a crypto transaction is a push transaction, initiated peer-to-peer without the need for an intermediary. Participants in blockchain networks control their digital assets on the blockchain with a private key — a cryptographically secured method of authentication and access.
Crypto requires you to be deliberate. Because no intermediary is required, personal responsibility becomes much more important when transferring value on-chain. Once transactions are confirmed on the blockchain, they are irreversible. This makes it notoriously difficult to recover funds that are lost or stolen.
Are blockchains vulnerable to security threats?
The notion that blockchain technology is inherently immune to security threats is somewhat misleading, but several of its unique structural features bolster its intrinsic security:
- Cryptography: Every transaction on the blockchain is secured with cryptographic principles, ensuring data integrity and authentication. Public key infrastructure (PKI) grants users a public key to receive assets and a private key to safeguard them.
- Decentralization: Instead of a centralized server or authority, blockchains operate across a network of computers (nodes). This distributed nature means that even if a node or a group of nodes are compromised, the entire system remains largely unaffected.
- Consensus: These algorithms ensure that all nodes in the network agree on the validity of a transaction. Common consensus algorithms include Proof-of-Work (PoW) and Proof-of-Stake (PoS). Features like PoW or PoS make it computationally non-viable for a single attacker to control the majority of nodes, known as a Sybil Attack.
- Immutability: Once a block is added to the blockchain, its content becomes immutable, meaning it cannot be changed or altered. This ensures that transaction records are permanently kept intact.
- Transparency: Since many blockchains are public ledgers, any change or transaction can be viewed by anyone, making malicious activity easily detectable.
While these defining characteristics are the reason blockchain technology is considered so revolutionary, there are still vulnerabilities that can be exploited. Paradoxically, some of the traits of blockchain (e.g. immutability) can introduce unique complexities if the system itself is compromised. Next, we’ll look at challenges in securing blockchains and some of the most common threats currently shaping the landscape.
Challenges in securing blockchains
A major challenge in securing blockchain systems is that the pace of innovation continues to outstrip the development of security tools. New protocols, features, and use cases emerge faster than they can be thoroughly vetted, leaving gaps that attackers are quick to exploit.
The permissionless nature of blockchain adds another layer of complexity. Anyone can deploy a contract, launch a token, or interact with protocols, creating low barriers for malicious actors to operate at scale. Scams can proliferate with little friction, often faster than detection systems can respond.
Cross-chain activity only compounds the problem. As users move assets across multiple blockchains, visibility into transactions can become fragmented. Monitoring and securing these flows requires coordination across protocols — something the current infrastructure isn’t fully equipped to handle.
Finally, one of the most persistent challenges is real-time detection. On-chain behavior can look similar, whether it’s part of a legitimate arbitrage strategy or a coordinated exploit. This ambiguity makes it increasingly difficult to distinguish between malicious and benign actions before damage is done.
Common types of blockchain threats
The following threats target applications operating on-chain — such as DeFi protocols, bridges, and phishing tokens — rather than the underlying blockchain infrastructure itself.
Smart contract exploits
Smart contracts are self-executing code that power everything from decentralized finance (DeFi) protocols to non-fungible tokens (NFTs). But once deployed, a single bug can expose millions in locked assets. Attackers often exploit logical flaws, reentrancy vulnerabilities, or unchecked access controls to drain funds or manipulate protocol behavior. Without code audits, even well-intentioned projects can become exposed.
Between January and November 2024, approximately 8.5% of funds stolen were due to smart contract vulnerabilities and code exploits.
Oracle manipulation
Oracles feed real-world data into smart contracts. If attackers influence or corrupt these inputs, they can trigger faulty contract logic. For instance, manipulating the reported price of an asset could allow an attacker to buy it at a discount or trigger a liquidation cascade. In DeFi, where value is algorithmically tied to oracle data, the consequences can be immediate and catastrophic.
Bridge attacks
Cross-chain bridges allow assets to move between blockchains, but they’ve also become prime targets for attackers. Many bridge architectures rely on complex smart contracts and custodial mechanisms, creating large honeypots of funds. A single vulnerability can be exploited to mint or release wrapped tokens without backing, leading to massive losses.
Rug pull schemes
Not all threats in blockchain are technical. Some of the most damaging attacks are social in nature. Rug pulls occur when developers abruptly withdraw liquidity or abandon a project after attracting user investment, leaving holders with worthless tokens. These schemes often masquerade as legitimate startups, leveraging hype, influencer marketing, and anonymous teams to build trust before vanishing with user funds.
We identified that 3.59% of all launched tokens in 2024 displayed patterns that may have been linked to rug pull schemes. Moreover, approximately 94% of DEX pools involved in suspected pump-and-dump schemes appear to be rugged by the address that created the DEX pool. The other 6% appear to be rugged by the addresses that were funded by the pool or token deployer.
Phishing attacks and social engineering
Phishing remains one of the most effective attack vectors in crypto. As we recently revealed in our 2025 Crypto Crime Report, nearly $10 billion worth of crypto was lost in 2024 due to fraud and scams, although we estimate this number is likely closer to $12.4 billion, which would be a slight increase from amounts stolen in 2023.
Whether through fake wallet apps, malicious airdrops, or impersonated support accounts, attackers trick users into revealing private keys or signing malicious transactions. These scams are growing more targeted and convincing, often exploiting community trust and platform UX loopholes.
The role of blockchain analytics in preventing attacks
Preventing cyberattacks before they happen starts with visibility. On-chain data provides an invaluable window into blockchain activity, helping security teams identify red flags early — whether that’s unusual transaction patterns, interactions with known malicious contracts, or sudden liquidity movements. Real-time monitoring and transaction analysis are essential for catching threats in motion.
Key components of blockchain analytics include:
- Address labeling: Tagging wallets with known associations, such as scams and mixers, helps teams assess security risk at a glance.
- Attribution databases: Building and maintaining attribution data allows for faster, more accurate tracing of funds and behavioral patterns.
- Protocol audits: Regular code reviews can help catch vulnerabilities before deployment.
- Smart contract testing: Simulations and fuzz testing expose edge cases that may lead to exploits.
- Incident response: Fast, data-driven investigation capabilities support containment and recovery during active attacks.
- Cross-chain visibility: Analytics platforms that track activity across chains are essential for detecting exploits that span multiple ecosystems.
Chainalysis plays a critical role in blockchain analytics by connecting activity across chains and platforms, enabling faster detection, deeper investigations, and more coordinated responses. As threats grow more complex, this kind of integrated, data-driven approach is key to building safer blockchain infrastructure.
Blockchain threat prevention with Chainalysis Hexagate
Chainalysis Hexagate brings proactive defense to the forefront of blockchain security. Designed for real-time monitoring and threat detection, Chainalysis Hexagate empowers protocols, bridges, decentralized applications (dApps), and exchanges to identify and block malicious transactions before damage occurs. By analyzing transaction intent and on-chain behavior as it happens, it allows security teams to act before potential exploits.
Here are some benefits of Chainalysis Hexagate:
- Preemptive attack prevention: Detects malicious transactions before execution, stopping exploits in real time.
- Tailored Web3 security: Built specifically for decentralized finance (DeFi) protocols, cross-chain bridges, decentralized exchanges (DEXs), and Web3 apps.
- Real-time alerts: Warns teams of threats early enough to prevent financial loss or protocol compromise.
- Seamless integration: Easily fits into existing security workflows and infrastructure.
Use cases and who it’s for
Chainalysis Hexagate is built for a range of security-focused teams operating across the blockchain ecosystem:
- Protocol and dApp developers: Monitor on-chain risk, defend against contract exploits, and maintain protocol integrity.
- Security teams: Identify threats targeting smart contracts, oracles, and governance mechanisms before they strike.
- Bridge operators: Detect cross-chain anomalies and suspicious activity to safeguard token flows.
- Incident response and fraud units: Leverage attribution data to respond quickly, trace funds, and contain active threats.
Why blockchain security is critical for adoption
The cost of a major blockchain attack goes far beyond lost funds — it can shatter user trust, damage reputations, and set back entire ecosystems. For institutional and enterprise adoption to accelerate, trust must be earned and maintained through strong, visible security practices.
The industry is shifting from reactive cleanup to proactive prevention, recognizing that real-time intelligence and early detection are essential to staying ahead of threats. But this requires continuous investment in data security infrastructure, tooling, and collaboration across the ecosystem.
At Chainalysis, we’re committed to enabling safe, scalable blockchain adoption. By equipping teams with the data and tools they need to prevent attacks before they happen, we’re helping build a future where innovation and security grow together.
Book a demo of Chainalysis Hexagate’s fraud prevention and security solution here.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.