TL;DR
- We estimate $17B was stolen in crypto scams and fraud in 2025 — as impersonation scams show massive 1400% year-over-year (YoY) growth. AI-enabled scams were 4.5 times more profitable than traditional scams.
- Major scam operations became increasingly industrialized, with sophisticated infrastructure, including phishing-as-a-service tools, AI-generated deepfakes, and professional money laundering networks.
- Strong connections to East and Southeast Asian crime networks were identified, particularly through forced labor compounds in Cambodia, Myanmar, and other regions, where trafficking victims are forced to operate scams.
- Law enforcement made record-breaking seizures, including a 61,000 bitcoin recovery in the UK and a $15 billion seizure linked to the Prince Group criminal organization, showing improved capability to combat crypto fraud.
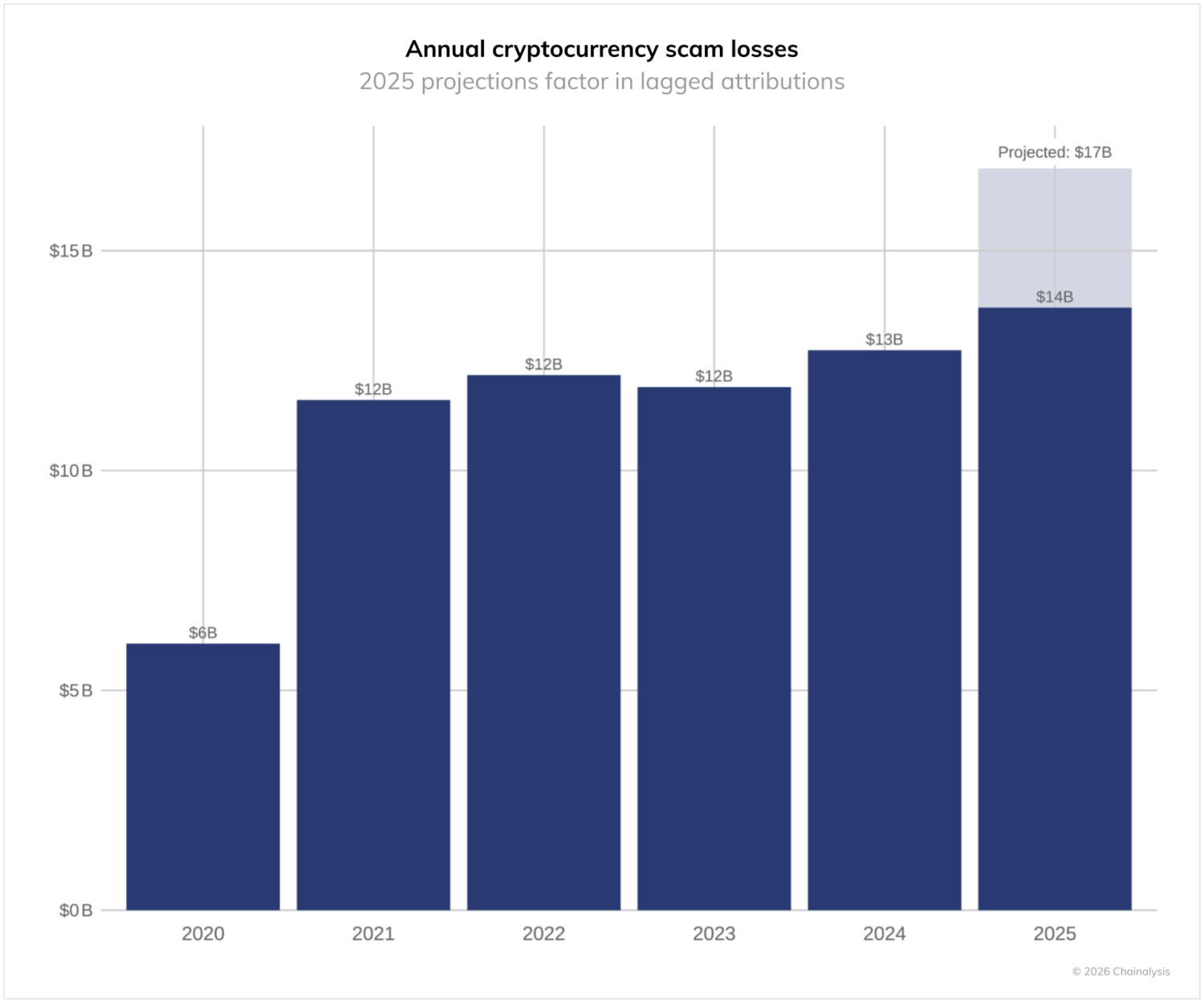
In 2025, cryptocurrency scams received at least $14 billion on-chain, a significant increase from the $9.9 billion we first reported in 2024, which reached $12 billion at our recalculation as of this writing – a number that was broadly in line with our projected $12.4B for the year. Based on historical trends, in which our annual estimates grow by an average of 24% between reporting periods, we project that the 2025 figure could exceed $17 billion as we identify more illicit wallet addresses in the coming months.
This year’s data show scammers continuing to adapt and innovate, with the average scam payment increasing from $782 in 2024 to $2,764 in 2025, a growth of 253% YoY. Overall scam inflows have also surged, particularly through impersonation tactics that saw a staggering 1400% year-over-year (YoY) growth. While high-yield investment programs (HYIP) and pig butchering remain dominant categories by volume, we’re seeing increasing convergence across scam types as fraudsters leverage AI, sophisticated SMS phishing services, and complex money laundering networks to target victims more effectively than ever before.
Traditional scam categorizations are becoming less distinct as fraudsters incorporate multiple tactics into their operations. For example, many pig butchering and investment scams incorporate elements of impersonation, social engineering, and even technical- or wallet-focused scams.
Impersonation scams see explosive growth
Impersonation scams have emerged as a particularly concerning trend, growing more than 1400% compared to 2024, with the average severity (i.e., amount) of payments made to these clusters increasing by over 600%. These scams involve fraudsters posing as legitimate organizations or authority figures to manipulate victims into transferring funds.
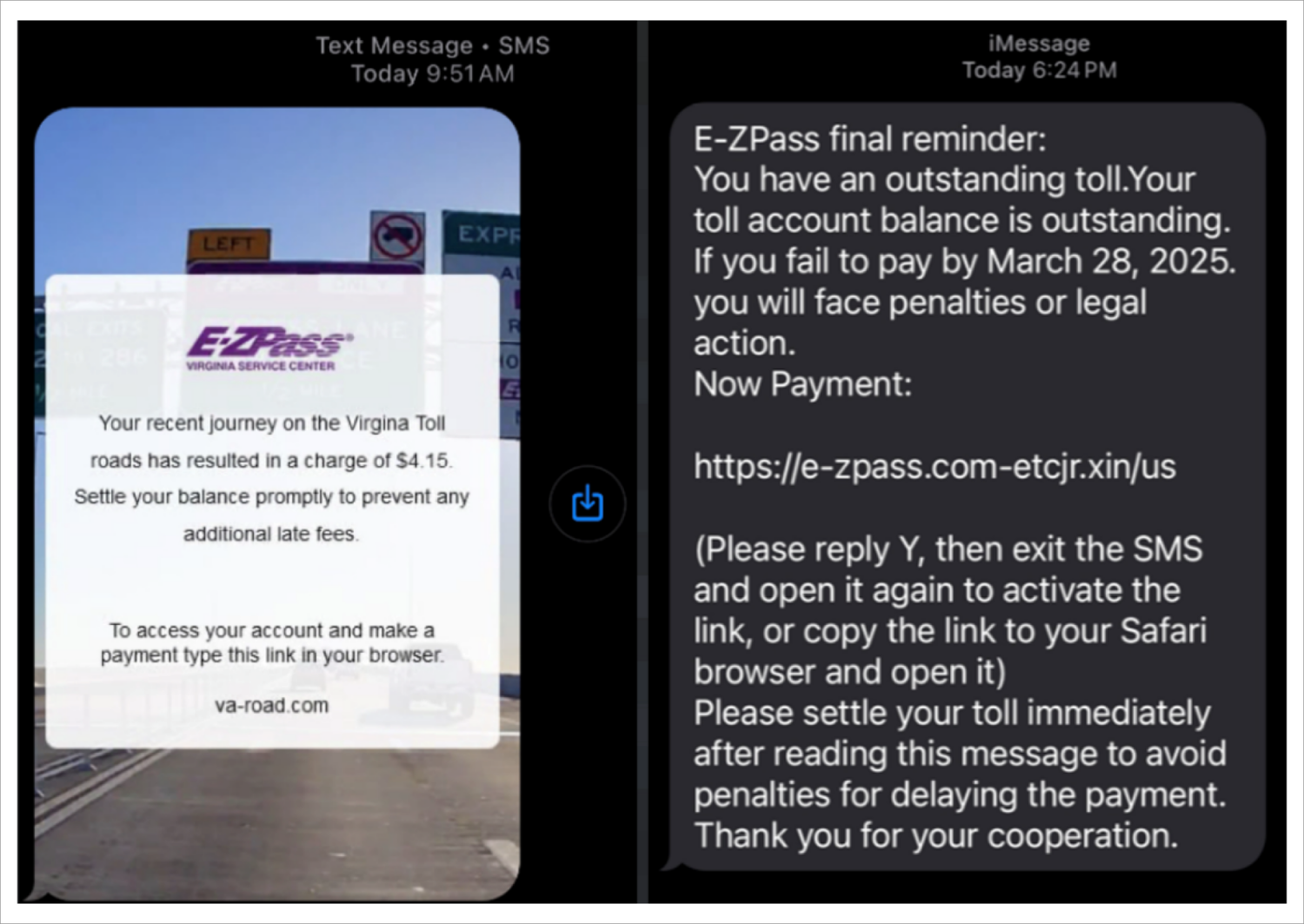
Government impersonation: The E-ZPass scam network
Government impersonation has become an effective tactic, with scammers leveraging the inherent trust people place in official communications. One of the most prolific examples was the widespread “E-ZPass” phishing campaign that targeted millions of Americans using the E-ZPass electronic road toll collection system in 2025.
This operation was attributed to a Chinese-speaking cybercriminal group known as “Darcula” also known as the “Smishing Triad.” This China-based cybercrime network used phishing-as-a-service tools to distribute SMS messages impersonating toll collection agencies, particularly targeting E-ZPass users across at least eight states. This group specializes in these tactics and has also impersonated the U.S. Postal Service.
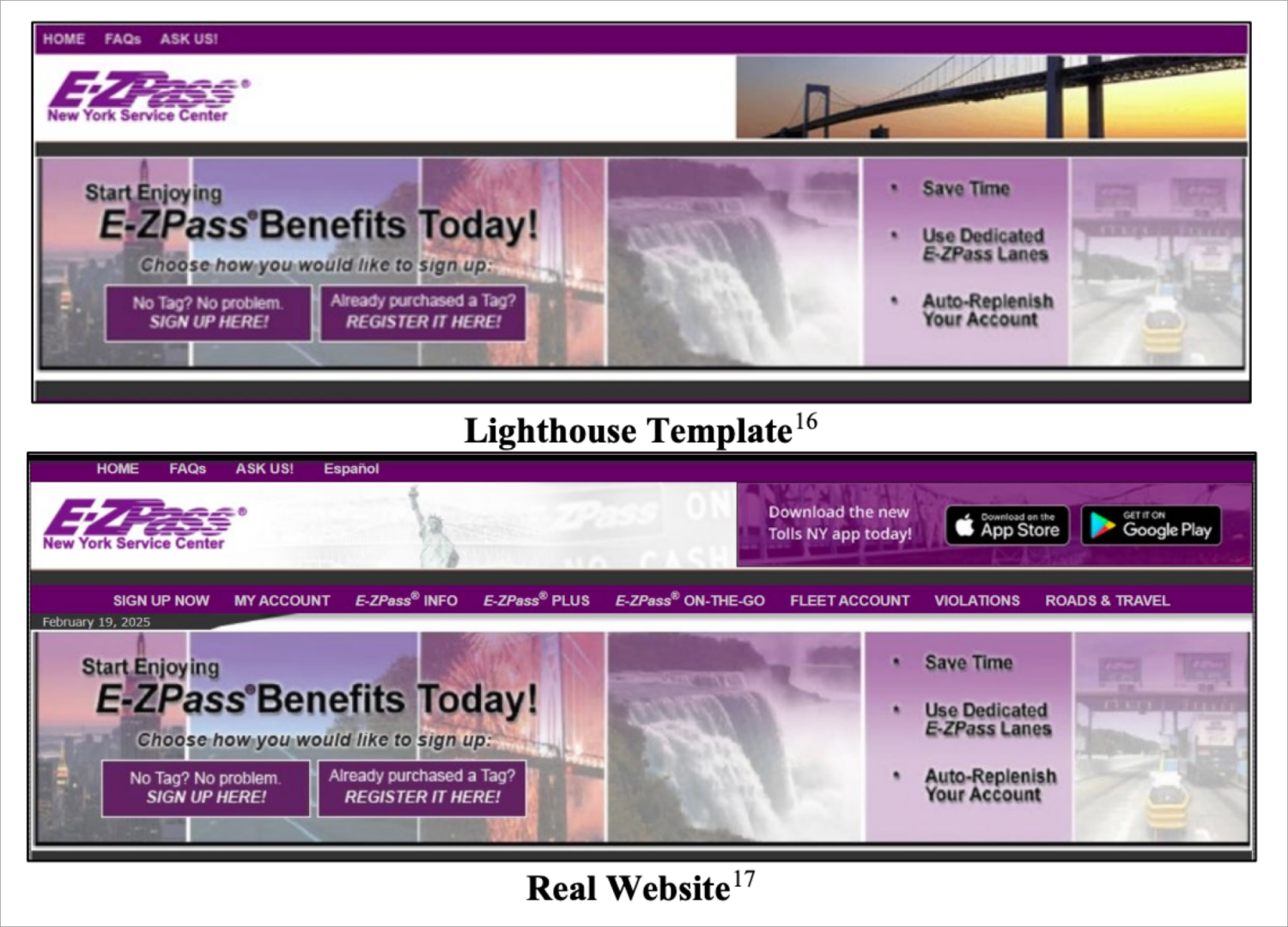
According to Google’s lawsuit, filed in November 2025, Smishing Triad leveraged software from “Lighthouse,” a Chinese-language vendor that offers cybercriminals “phishing for dummies,” with hundreds of templates for fake websites, domain setup tools, and features designed to evade detection.
The group created fraudulent websites mimicking government agencies, including the New York City government official website (nyc.gov) and New York E-ZPass (e-zpassny.com), designed to be indistinguishable from the legitimate websites they impersonated.
In addition to illustrating how cybercriminals leverage infrastructure purchased with cryptocurrency to carry out criminal activity, this case shows how the on-chain footprints left by cybercriminals generates actionable disruption opportunities. As depicted in the graph below, various Chinese criminal underground entities, such as the Taihe Gong scamming group, have purchased Lighthouse phishing kits and received payments from several Chinese-language money laundering networks (CMLNs) and fraud shops. Taihe Gong comprises Chinese-speaking operators suspected of engaging in fraudulent cybercriminal activities, including the sale of phishing kits. Its operational structure suggests established distribution channels for malicious tools designed to facilitate illicit activity, such as online scams and credential theft.
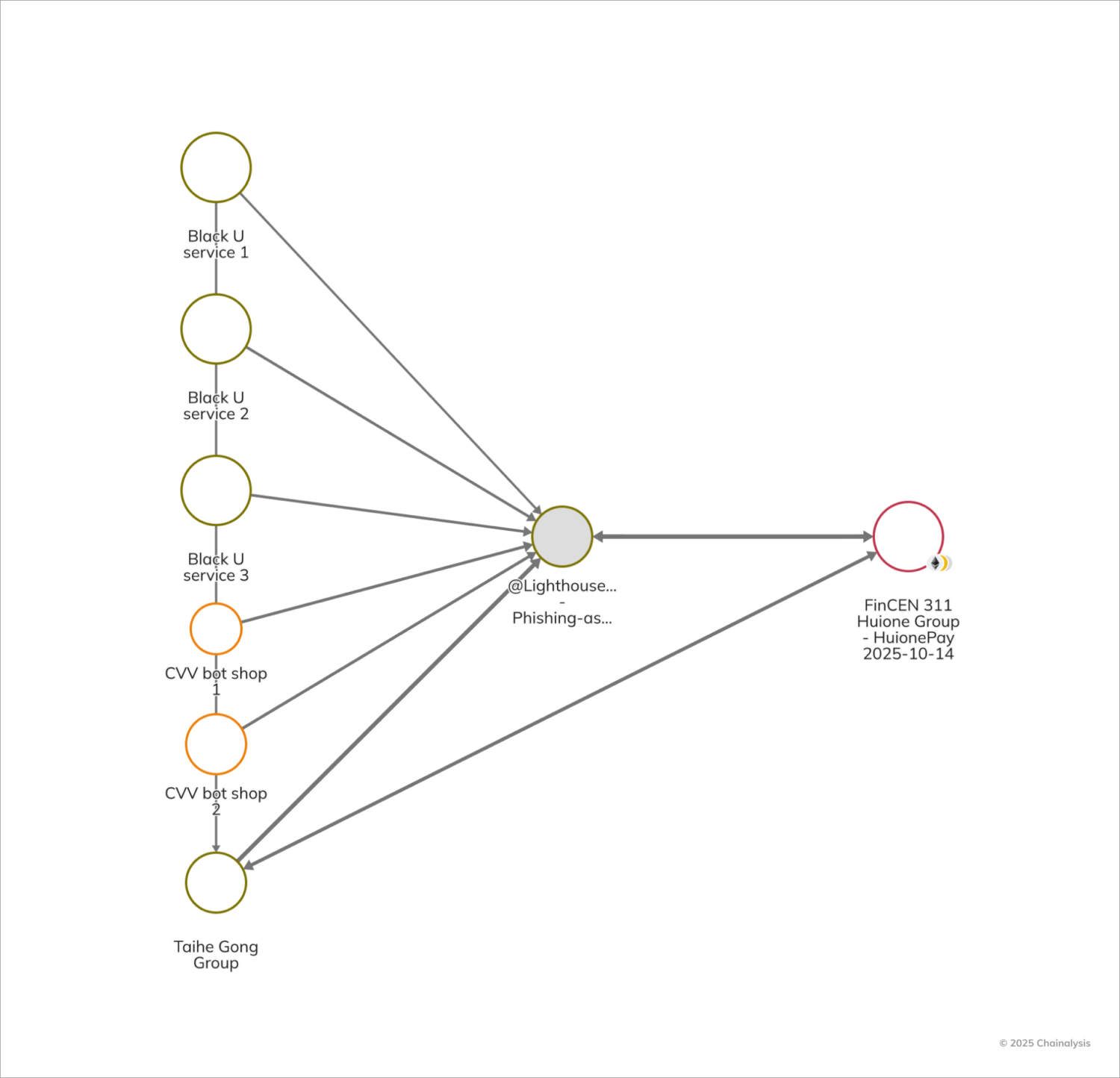
The E-ZPass case demonstrates how cheap the scamming infrastructure is, with some phishing kits likely purchased for under $500. But a relatively inexpensive scam at scale can still have a massive impact: the E-ZPass scheme allegedly reached 330,000 texts in a single day as part of a separate toll fee scam campaign, amassing $1 billion over three years and duping over 1 million people in at least 121 countries, according to Google’s lawsuit. According to Cisco Talos, the phishing kits had different pricing tiers, including $50 in cryptocurrency for a “full-feature development,” $30 for proxy development, and $20 for version updates and support. Lighthouse received over 7,000 deposits and amassed over $1.5 million in cryptocurrency in three years.
Unfortunately, Lighthouse is not the only vendor. Gary Warner, Director of Intelligence at DarkTower, is tracking eight major Chinese-language “Crime-as-a-Service” groups on Telegram, each of which has multiple vendors offering iMessage and RCS phishing services. The goal of these phish, according to Warner, is to load credit cards onto mobile wallets, then deploy to a network of shoppers around the world who facilitate trade-based money laundering by purchasing luxury goods and electronics for resale, often using “remote Tap-to-Pay” services. Everything from phishing design, hosting, and spamming, to shopping, cash-pickup, and goods purchasing is available in these Chinese criminal Telegram groups, some of which have more than 300,000 members. All buying, selling, and advertising are done using stablecoins as the currency of choice. Warner adds that much of the overseas money laundering also aims to convert goods or cash into stablecoins for easy transmission back overseas.
Private sector impersonation: Coinbase impersonation campaign
In December 2025, the Brooklyn District Attorney’s office indicted Ronald Spektor, a 23-year-old Brooklyn resident, for orchestrating a sophisticated cryptocurrency scam that defrauded victims of nearly $16 million. Spektor and his conspirators impersonated Coinbase customer service representatives, contacting users – whose information they had stolen in a bribery scheme – with alarming claims about unauthorized access to their accounts and convincing them to transfer their cryptocurrency to “secure” wallets controlled by the scammers. The recent arrest in India of a former Coinbase customer service agent who allegedly accepted $250,000 in bribes as part of this scam underscores how human trust remains among the most exploitable vulnerabilities in security infrastructures, as this insider breach compromised nearly 70,000 customers’ data and enabled credible impersonation attacks despite robust technical safeguards.
The scheme specifically targeted cryptocurrency exchange users by exploiting their trust in what appeared to be legitimate customer service communications, demonstrating how impersonation scams have evolved to leverage users’ anxieties about account security. This case exemplifies the growing sophistication of exchange impersonation tactics and their devastating impact on victims who believed they were protecting their digital assets. As Brooklyn District Attorney Gonzalez said, “My office…will continue to root out every instance of cryptocurrency fraud, which is a serious problem that’s been exploding throughout the country. We will investigate offenders using the latest technology, freeze their assets whenever possible, and assist the victims.”
Following funds from impersonation scams demonstrates evolving DeFi laundering tactics
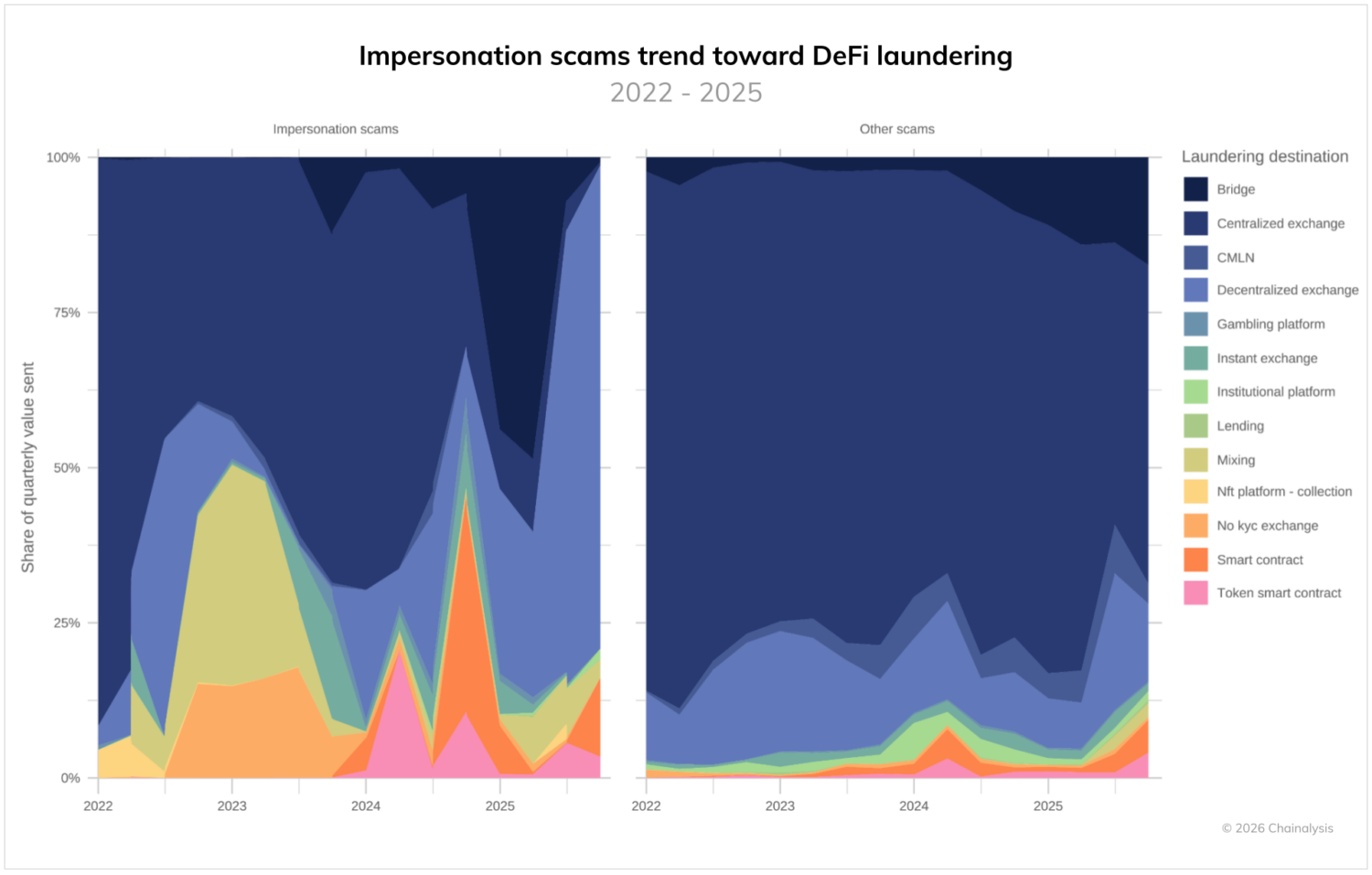
Impersonation scams also have distinctive laundering patterns that rely heavily on the DeFi ecosystem. This trend contrasts sharply with other scams, which continue to rely heavily on centralized exchanges to launder funds (a trend we will refer to later when discussing pig butchering scams). Interestingly, impersonation scams seem to have moved in distinctive waves when leveraging DeFi to layer funds. In 2024, these scams saw spikes associated with laundering via smart contracts and token smart contracts. In 2025, these pronounced volumes subsided in lieu of alternating waves associated with bridge use (early-to-mid 2025) and DEX use (second half of 2025). These patterns show the constantly adapting nature of scam operations, which vary in terms of primary laundering points and the types of services used.
AI and advanced tools are supercharging scam effectiveness
We are moving toward a future in which virtually all scams will incorporate AI into their operations to some degree. While many scammers buy AI tools through traditional payment channels, a subset buys these tools on-chain, making their transactions visible. Exploring the differences between scams with visible on-chain associations to Chinese AI vendors lets us estimate the scale and efficiency of AI.
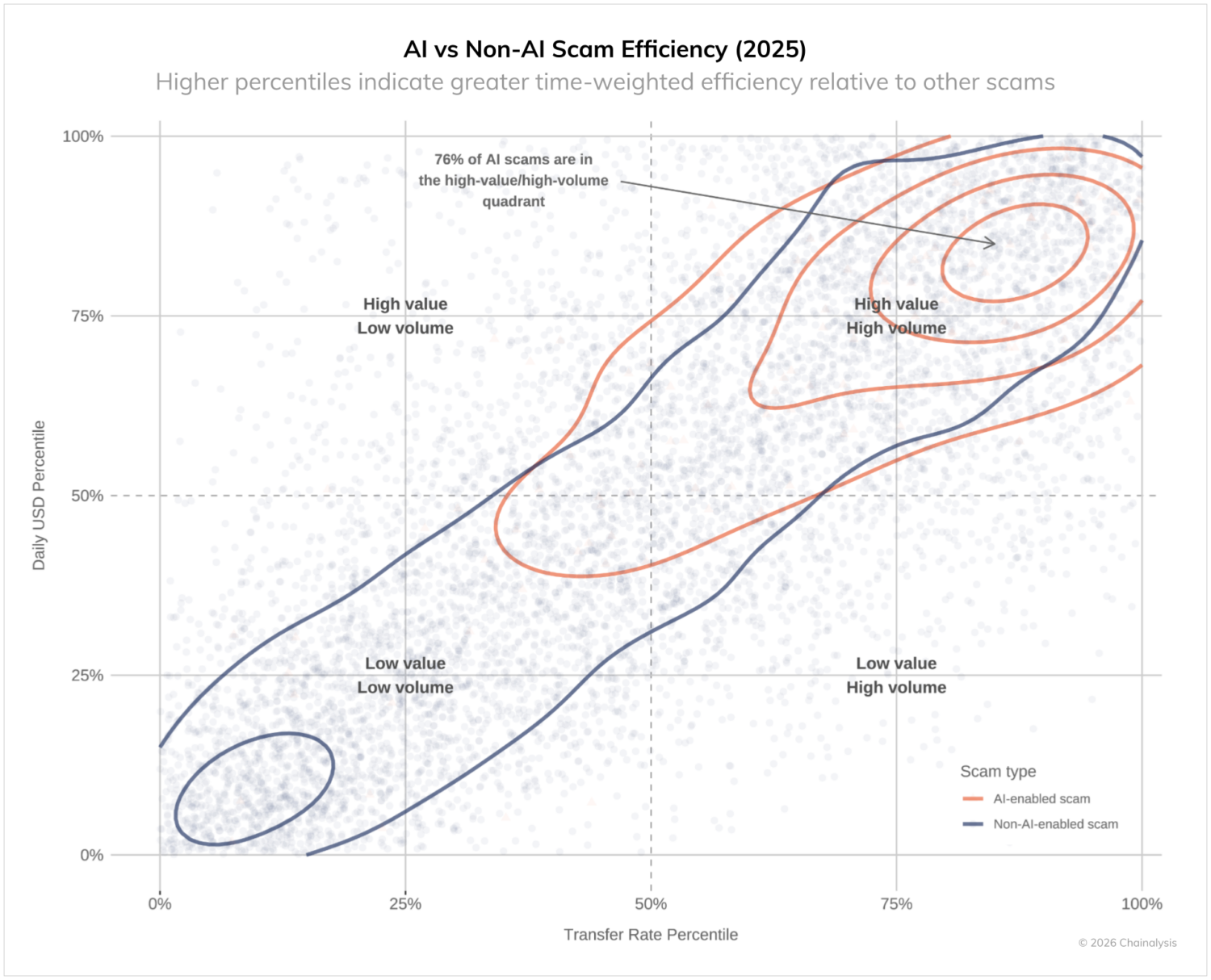
As depicted below, 76% of AI-enabled scams are in the time-weighted high-value/high-volume quadrant. This means that a large majority of scams with demonstrable on-chain links to often Telegram-based Chinese AI vendors selling face-swap software, deepfake technologies, and LLMs tend to (1) scale more quickly (i.e., higher incoming transfer rates) and (2) be more severe (i.e., higher daily USD volumes) than scams without these clear on-chain links to AI vendors.
AI-enabled scams extract 4.5 times more money
According to a report published by J.P. Morgan in July 2025, scammers are increasingly leveraging deepfake technology and AI-generated content to create convincing impersonations in romance and investment scams. Our analysis reveals that, on average, scams with on-chain links to AI vendors extract $3.2 million per operation compared to $719,000 for those without an on-chain link — 4.5 times more revenue per scam. These AI-related operations also demonstrate significantly greater time-weighed efficiency:
- Higher daily revenue: $4,838 vs $518 median daily revenue
- Increased transaction volume: 35.1 vs 3.89 average transfers per day (9x more transaction activity)
These metrics suggest both higher operational efficiency and potentially broader victim reach. The increased transaction volume indicates that AI is enabling scammers to reach and manage more victims simultaneously, a trend consistent with the industrialization of fraud we’ve been tracking. In contrast, the increased scam volume suggests that AI is likewise making scams more persuasive.
According to Will Lyne, Head of Economic & Cybercrime at the Metropolitan Police, “Fraud linked to cryptocurrency continues to grow in scale and sophistication, with organised crime groups increasingly using impersonation tactics, online infrastructure, and AI-enabled tools to target victims at pace and scale. However, we are also seeing a step change in law enforcement’s ability to respond. Through specialist capabilities, international cooperation, and the effective use of financial and digital intelligence, we are better equipped to identify criminal networks, seize illicit assets, and disrupt activity that causes harm in our communities.”
The industrialization of fraud
The Lighthouse case exemplifies another key trend: the professionalization and commercialization of the tools needed by scammers to execute sophisticated, industrial-scale scams. The Lighthouse Enterprise operated a complex business model where different actors specialized in distinct parts of the scams and fraud supply chain:
- Developer Group: Supplied phishing software and templates
- Data Broker Group: Provided targeted lists of potential victims
- Spammer Group: Offered tools to send fraudulent text messages at scale
- Theft Group: Specialized in monetizing stolen sensitive information
- Administrative Group: Ran online recruitment and collaboration forums
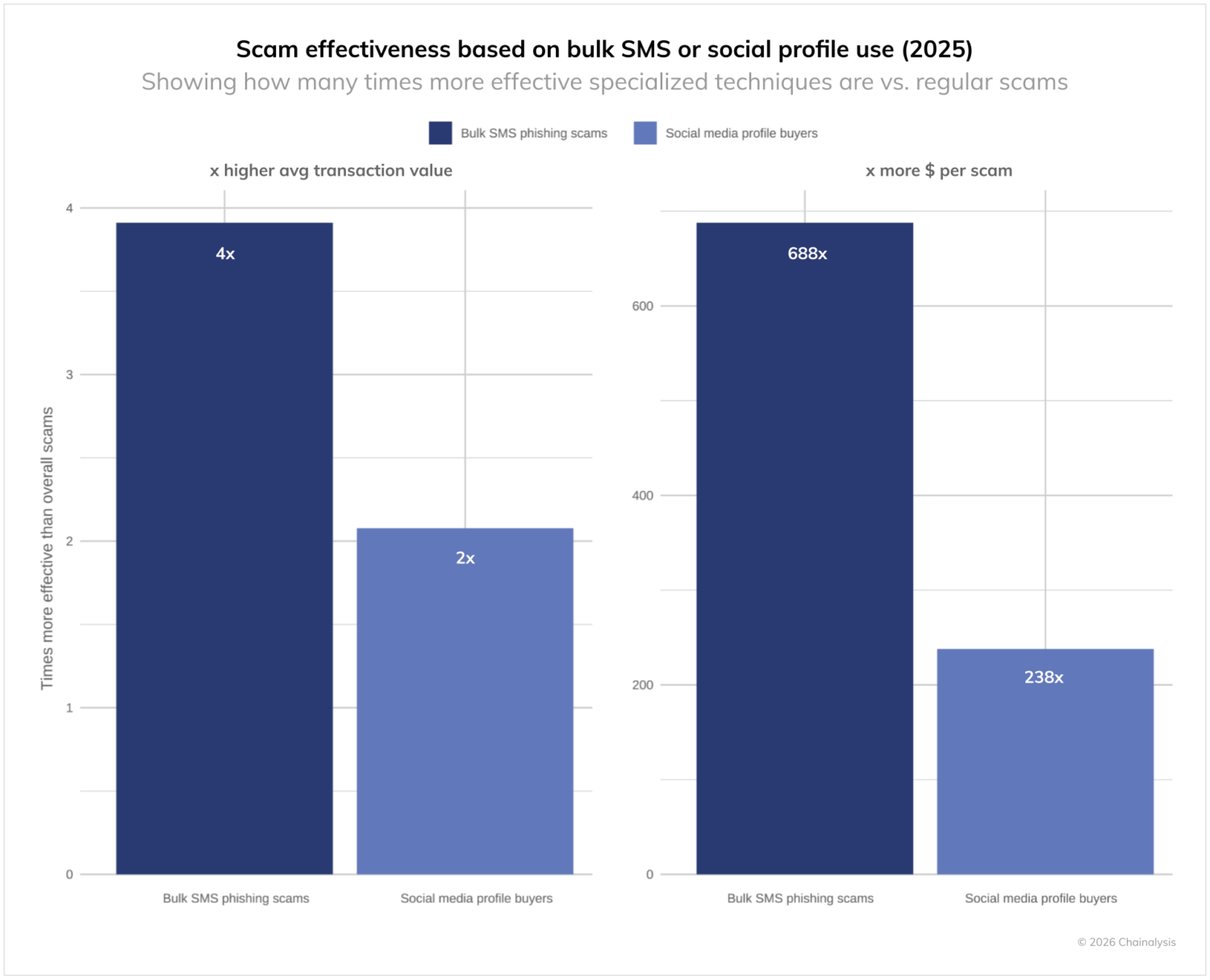
This modular, service-based approach is a force multiplier and allows even technically unsophisticated criminals to execute sophisticated phishing campaigns, substantially lowering the barrier to entry for cryptocurrency fraud. Many of these campaigns have a social media angle, given that such platforms provide access to millions of users, and are thus prime targets for sending automated messages. In such cases, scammers may buy bulk social media profiles and use SMS and phishing kits to communicate.
The material impact of this large-scale industrialization cannot be understated. Scams leveraging these phishing kits are 688 times more effective in dollar terms and four times more effective in average transaction size than regular scams. Scams that buy bulk social media accounts are likewise 238 times more effective in dollar terms and two times more effective in average transaction value compared to regular scams.
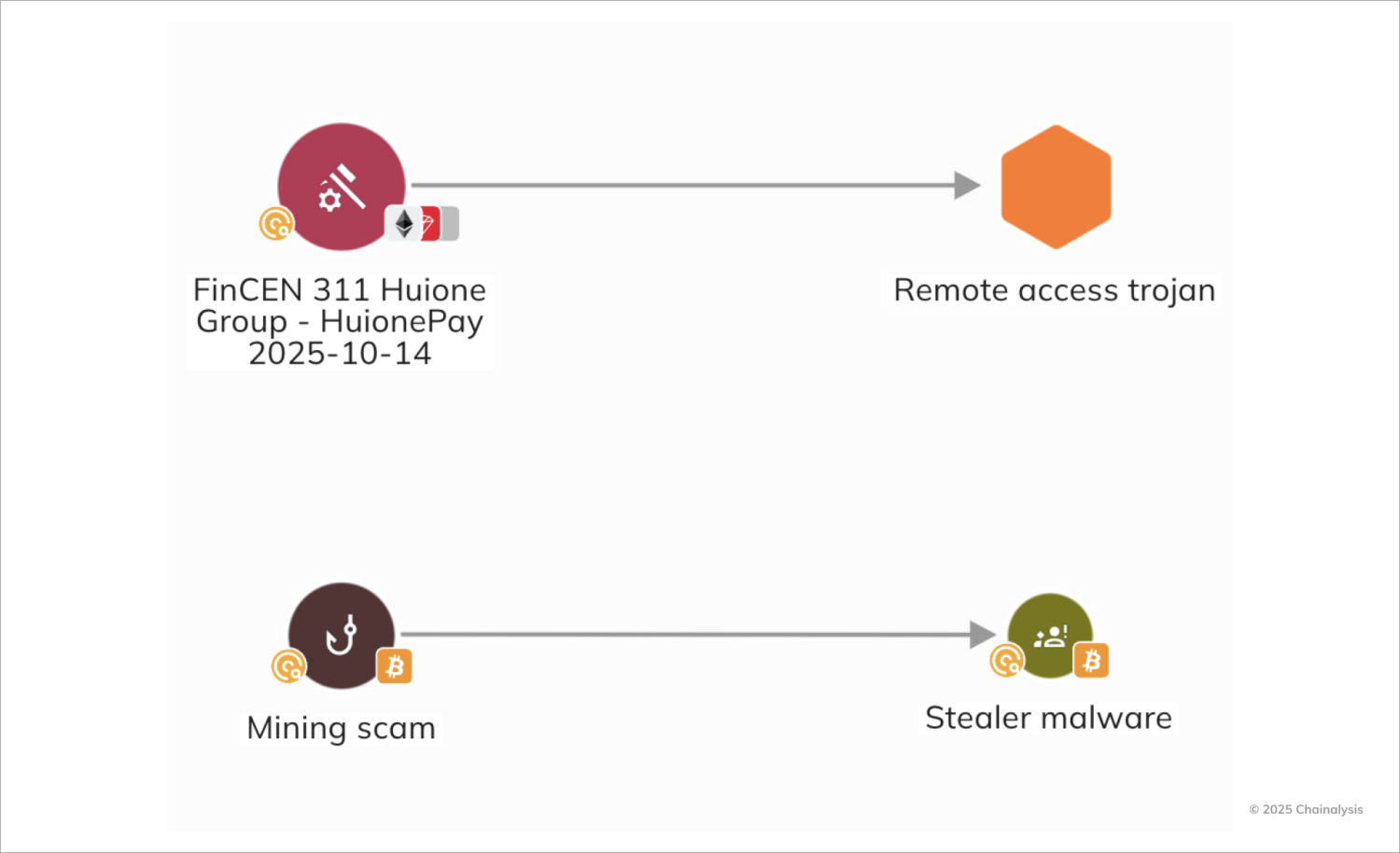
The UNODC has previously warned about scam campaigns’ use of malware, a phenomenon we are increasingly seeing on-chain. Chinese scammers, in particular, regularly lace scams with Stealer Malware or Remote Access Trojans (RATs) that can drain accounts without interacting with victims. The bar for success is then much more achievable for scammers, who only need one click from a victim rather than developing a relationship with them.
Law enforcement on the offensive, with record seizures targeting scam operations
The growing scale and sophistication of scam activity prompted unprecedented law enforcement action in 2025, culminating in two of the largest-ever crypto-related law enforcement actions directly connected to scam operations.
Jian Wen and Yadi Zhang
In November 2025, the UK’s Metropolitan Police secured convictions in a landmark crypto money laundering case that led to the world’s largest confirmed cryptocurrency seizure, recovering over 61,000 Bitcoin — currently valued at around £5 billion — from Chinese national Zhimin Qian (also known as Yadi Zhang), who orchestrated a multibillion-pound investment fraud in China that victimized more than 128,000 people between 2014 and 2017. Qian was sentenced to 11 years and eight months’ imprisonment for possessing and transferring criminal property, while her accomplice Seng Hok Ling received a nearly five-year term for his role in laundering the cryptocurrency. This case not only underscores the scale and sophistication of crypto-linked money laundering networks spanning jurisdictions, but also highlights the persistent threat posed by criminals attempting to convert illicit crypto proceeds into real-world assets through complex international schemes.
“This was a long, complex, and unprecedented investigation into the laundering of criminal proceeds through cryptocurrency. Over a number of years, significant efforts were made to move and disguise the funds and convert them into assets in the UK,” said Detective Sergeant Isabella Grotto, the lead investigating officer on the case. “By working closely with partners in the UK and overseas, with support from Chainalysis, we were able to trace the movement of the cryptocurrency, identify assets linked to the offending, and ultimately recover more than 61,000 bitcoin. That work was central to building the case and securing this outcome.”
The investigation, built on information dating back to 2018, revealed that Qian had fled to the UK under a false identity after amassing illicit funds and had attempted to launder them via luxury property purchases and other high-value assets, a pattern seen in many large-scale fraud operations. The record-setting seizure and subsequent prison sentences demonstrate law enforcement’s growing capability to trace and disrupt sophisticated fraud-to-crypto money laundering globally, reinforcing the value of blockchain transparency in dismantling even deeply entrenched criminal networks.
The Prince Group
In a major disruption of the global scam ecosystem, the U.S. Department of Justice (DOJ) unsealed charges against Prince Group chairman Chen Zhi for allegedly overseeing Cambodian forced-labor scam compounds that powered large-scale cryptocurrency fraud targeting victims worldwide. According to prosecutors, these compounds operated as vertically integrated fraud factories: trafficked individuals were coerced into running pig butchering investment scams and romance fraud schemes, laundering proceeds through cryptocurrency to obscure attribution and scale operations globally. The case underscores how modern scam networks have professionalized, integrating human trafficking, money laundering, and crypto-enabled fraud into a single, industrialized business model.
Critically, U.S. authorities paired these indictments with large-scale financial disruption, including arrests across transnational money laundering networks and actions to seize and forfeit more than $15 billion in illicit proceeds linked to scam activity. In October, working in close coordination with the UK’s Foreign Commonwealth and Development Office (FCDO), the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) jointly designated 146 targets within the Prince Group Transnational Criminal Organisation. The designation cited a “laundry list of transnational crimes, including the construction, operation, and management of scam compounds reliant on human trafficking and modern-day slavery where industrial-scale cyberfraud operations target victims around the world, including U.S. citizens.” In a development that demonstrates the complex geopolitical dimensions of prosecuting transnational crypto crime, Chen was arrested in Cambodia in January 2026 after his Cambodian citizenship was revoked in December, and was subsequently extradited to China for investigation rather than to the United States where he faces indictment, highlighting the jurisdictional challenges in dismantling global scam networks.
These actions mark a shift from reactive victim recovery to systematic dismantling, targeting not just front-line scammers, but also the executives, infrastructure, shell companies, and financial rails that sustain them. Together, the Prince Group case and related DOJ, OFAC, and FCDO actions illustrate a new, more integrated phase in scam enforcement: one focused on breaking the economic backbone of crypto-enabled fraud at scale and across borders, rather than treating scams as local, isolated, or purely digital crimes.
Tickmilleas
The U.S. government is pursuing a forfeiture of tickmilleas[dot]com, a scam domain that served as core infrastructure for a transnational crypto investment fraud network operating out of the Tai Chang scam compound along the Myanmar-Thailand border. Registered in November 2025 via a Singapore-based registrar, the site impersonated a legitimate financial services firm to deceive primarily U.S.-based victims into sending BTC, ETH, USDT, and USDC to crypto wallets controlled by overseas scammers. Blockchain analysis shows victims were funnelled through U.S. crypto exchanges before funds were rapidly moved through multiple wallets and consolidation addresses – hallmark tactics of professional on-chain money laundering – explicitly linking the domain to cross-border professional money laundering. Tickmilleas’s operators are tied to Chinese organized crime syndicates embedded in Southeast Asia’s scam compound ecosystem, with on-the-ground protection from the DKBA, an armed group sanctioned by OFAC for supporting cyber scam centers.
These cases demonstrate the scale of modern cryptocurrency scam operations and their increasing integration with traditional organized crime. They also reveal the human cost of these schemes, which exploit both financial victims and the trafficked individuals forced to operate them, itself an unspeakable crime. These prosecutions’ success also underscores the growing capability of international law enforcement to trace cryptocurrency flows and dismantle complex criminal enterprises. However, the industrial scale of global scam operations suggests the challenge remains considerable.
Strong regional nexus to East and Southeast Asia persists
Our on-chain analysis continues to show persistent connections between cryptocurrency scams and operations based in East and Southeast Asia. While the Huione Guarantee platform identified in our 2025 report was effectively shut down following FinCEN’s 311 designation — which severed its access to the U.S. financial system — we’ve observed expansion of similar operations across the region.
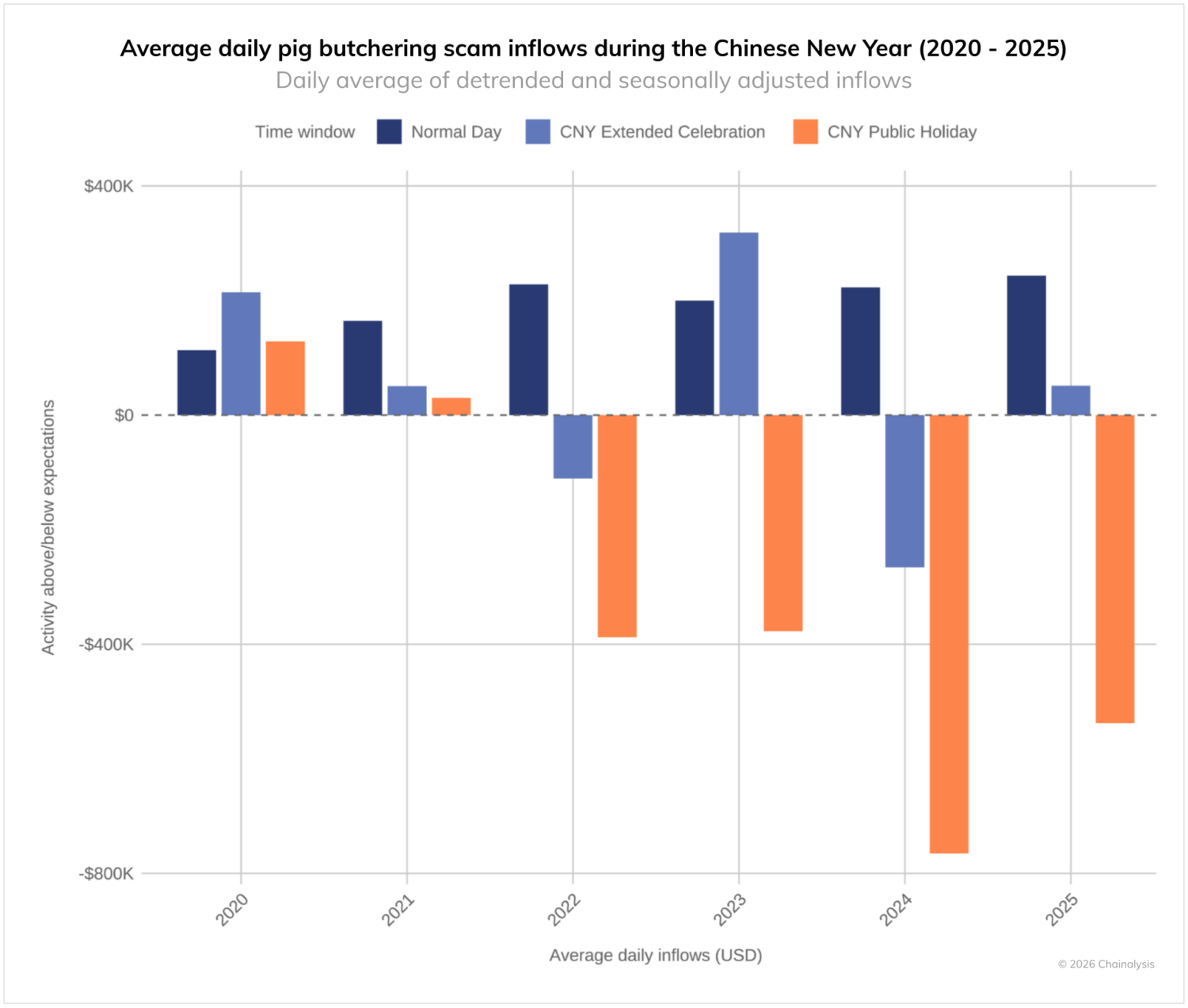
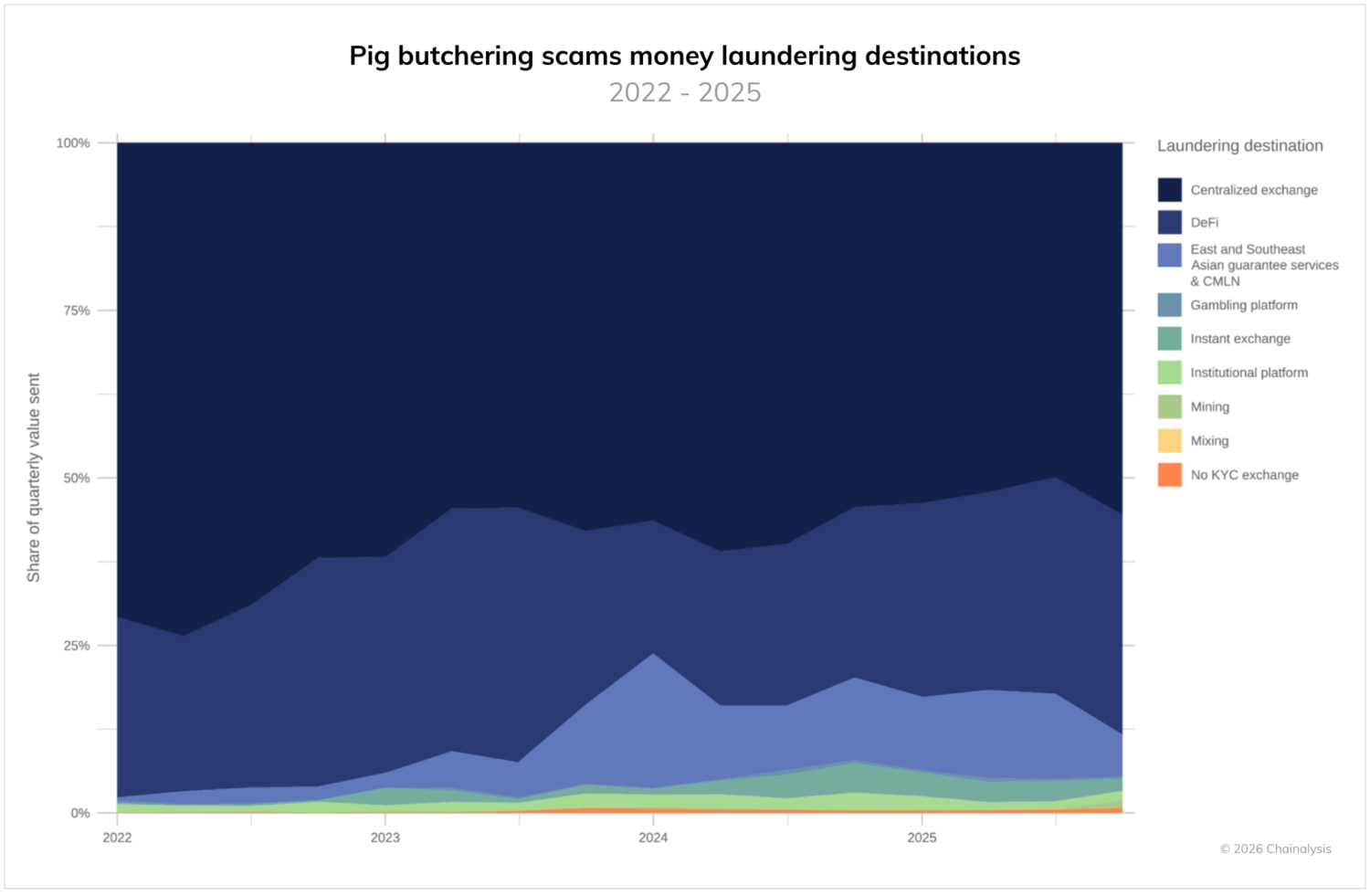
The centrality of the region to pig butchering is a defining characteristic of the scam ecosystem. The chart below shows the ‘holiday effect’ associated with the Chinese New Year public holiday (7 days at the start of the 15-day new year celebration). Starting around 2022, roughly when Huione began to play a central role in laundering funds from scam compounds such as KK Park, there was a notable reduction in pig butchering scam activity during the 7-day public holiday associated with the Chinese New Year. After the data have been detrended and seasonally adjusted, average daily pig butchering activity drops notably during these short windows. This pattern suggests that the Chinese holiday is associated with a reduction in inflows to pig butchering scams, indicating that actors in East and Southeast Asia play an important role in this scam ecosystem.
Our research shows that pig-butchering networks across Southeast Asia, drawing heavily on CMLNs, generate billions of dollars annually and rely on layered wallet structures, exchanges, shell companies, and informal banking channels to launder funds and convert crypto into real-world assets, including real estate and luxury goods. The Prince Group case study reflects this model, underscoring how scam operators and underground laundering networks form a resilient ecosystem that rapidly adapts to enforcement pressure, shifts infrastructure, and continues to scale globally.
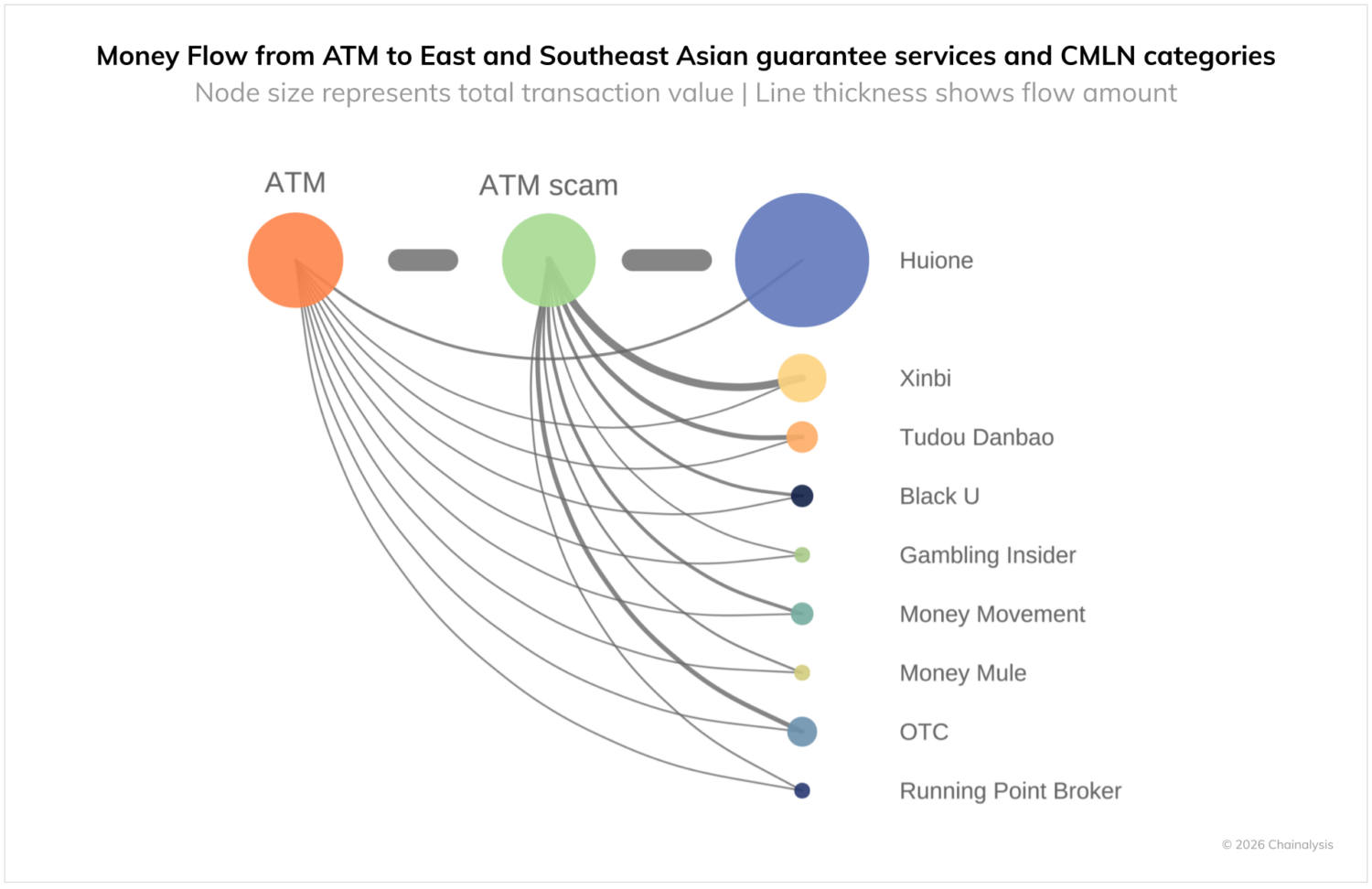
ATM scams targeting the elderly launder funds via guarantee services and CMLNs
Scams targeting older adults represent some of the most financially devastating frauds reported in the US, with recent estimates indicating that Americans aged 60 and older lose billions of dollars annually to financial exploitation and fraud, including nearly $4.9 billion in reported losses in 2024 alone, more than any other age group, according to AARP and FBI data. The FBI’s Internet Crime Complaint Center (IC3) further underscores this trend: in 2024, individuals aged 60 and older reported $2.8 billion in losses from crypto-related scams, reflecting both the scale and the growing role of digital assets in modern fraud. While elder fraud encompasses a broad range of schemes, cryptocurrency ATMs have emerged as a notable on-ramp for scams. Reported losses from Bitcoin ATM fraud have risen sharply in recent years, and older victims are disproportionately affected by these kiosk-based conversions. The elderly, who often have significant retirement savings yet limited familiarity with irreversible digital payment methods, remain particularly vulnerable to such tactics.
Our on-chain analysis reveals that funds originating at U.S. crypto ATMs frequently flow into wallets associated with Southeast Asia-based CMLNs and guarantee services, which serve as key intermediaries in the broader global scam infrastructure. While not all on-chain flows from scams to CMLNs can be traced directly to ATM on-ramps, crypto ATMs remain a critical input for scammers targeting older adults, who are often instructed to convert cash into cryptocurrency at these kiosks before funds are quickly transferred. In this context, actors leveraging crypto ATMs as both payment conduits and loci of fraud increasingly depend on CMLNs to launder and integrate stolen funds into the wider financial system, illustrating how traditional elder fraud has evolved into a transnational, crypto-enabled ecosystem.
Regional infrastructure beyond KK Park and Huione compounds
The regional connection is further evidenced by the off-ramping patterns we observe, with a significant portion of pig butchering scam proceeds flowing to CMLNs. In Q1 2022, less than 1% of pig butchering scam laundering flows went to CMLNs. By Q1 of 2024, these services processed slightly over 20% of pig butchering scam laundering flows for the quarter, and these networks consistently laundered over 10% of scam funds in 2025. Interestingly, the growth in CMLN activity related to pig butchering scams has coincided with a steady decline in the use of centralized exchanges to launder or offramp funds, potentially because exchanges can freeze funds. Broadly, this rapid and sustained growth of CMLNs showcases the persistent, multi-year interconnection between pig butchering scams targeting individuals in the U.S., Canada, Europe, and elsewhere, and Chinese-language laundering services based in Southeast Asia.
The industrialization of cryptocurrency scams demands a proactive, multidisciplinary approach
The 2025 data reveal the extent to which cryptocurrency-enabled scams are becoming more sophisticated, organized, and efficient. Increasingly accessible AI tools, phishing-as-a-service platforms, and the convergence of different scam methodologies have reduced barriers to entry and enabled scamming at scale. While high-profile enforcement successes in 2025 are encouraging, the criminal networks orchestrating scams remain of persistent concern. These transnational groups have taken advantage of governance weaknesses in low-capacity jurisdictions, and have demonstrated flexibility and resilience, moving to new locations within and beyond Southeast Asia and adapting their operating models as necessary.
There are no silver bullets to tackling such entrenched, industrial-scale scamming activity and to be effective, a multi-pronged response is required, including:
- A stronger emphasis on preventing victim harm, including greater adoption of real-time fraud and mule detection systems such as Chainalysis Alterya by financial institutions and cryptocurrency businesses, and enhanced detection tools that can help victims protect themselves;
- Enhanced cross-border law enforcement coordination to facilitate rapid fund tracing and freezing, to disrupt financial flows and make it harder to cash out illicit proceeds; and
- International support for capacity building and technical assistance, to strengthen institutions and enforcement in low-capacity jurisdictions.
As we move into 2026, we expect further convergence of scam methodologies as scammers adopt multiple tactics and technologies simultaneously.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.