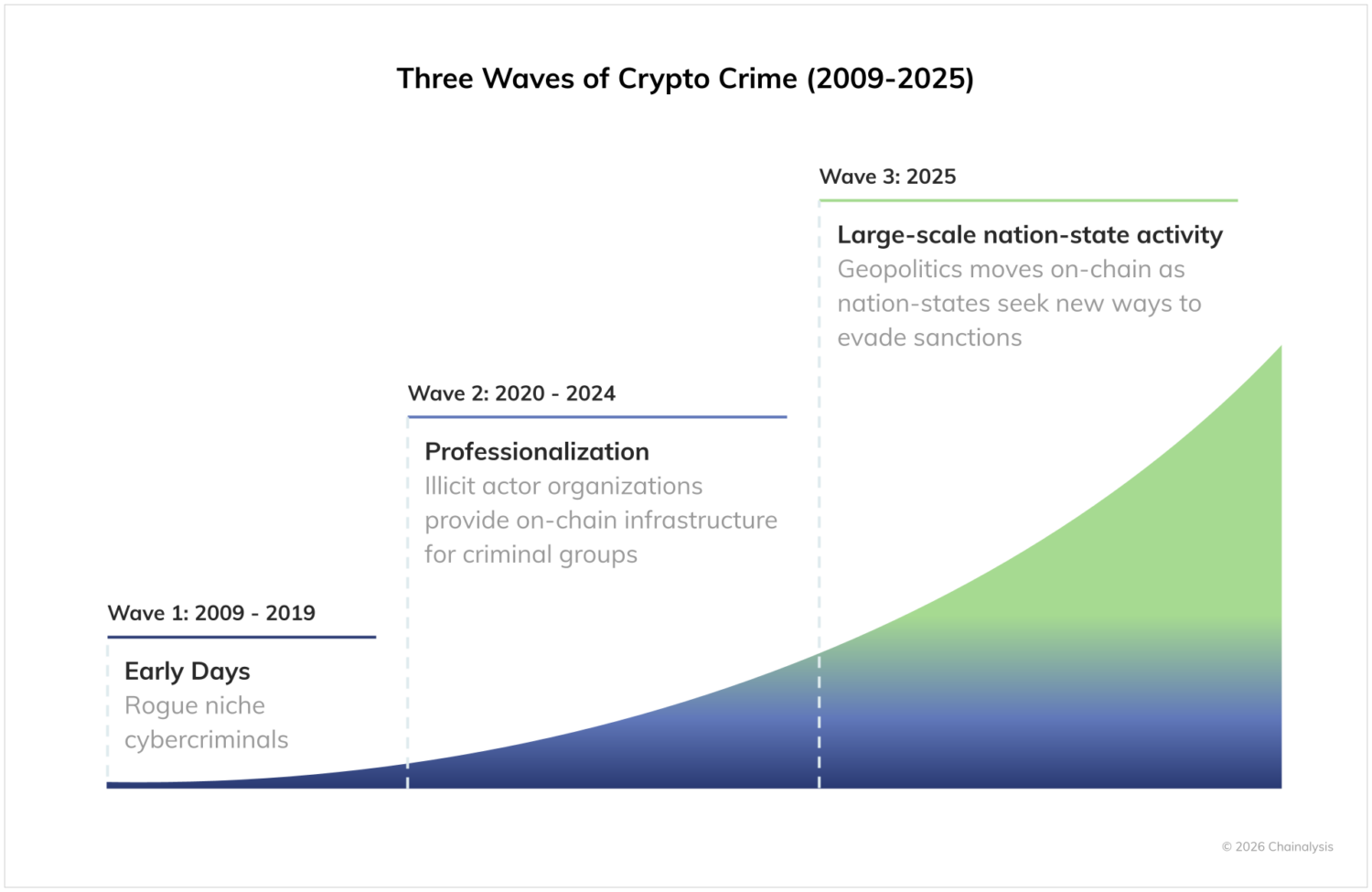
In 2025, we tracked a notable rise in nation-state activity in crypto, marking the latest phase in the maturation of the illicit on-chain ecosystem. Over the past few years, the crypto crime landscape has become increasingly professionalized; illicit organizations now operate large-scale on-chain infrastructure to help transnational criminal networks procure goods and services and launder their ill-gotten crypto. Against that backdrop, we have seen nation-states moving into this space, both by tapping into these same professionalized service providers and by standing up their own bespoke infrastructure to evade sanctions at scale. As nation-states plug into the illicit crypto supply chains originally built for cybercriminals and organized crime groups, government agencies and compliance and security teams now face significantly higher stakes on both the consumer protection and national security fronts.
How are these and other developments manifesting on-chain? Let’s examine the data and high-level trends.
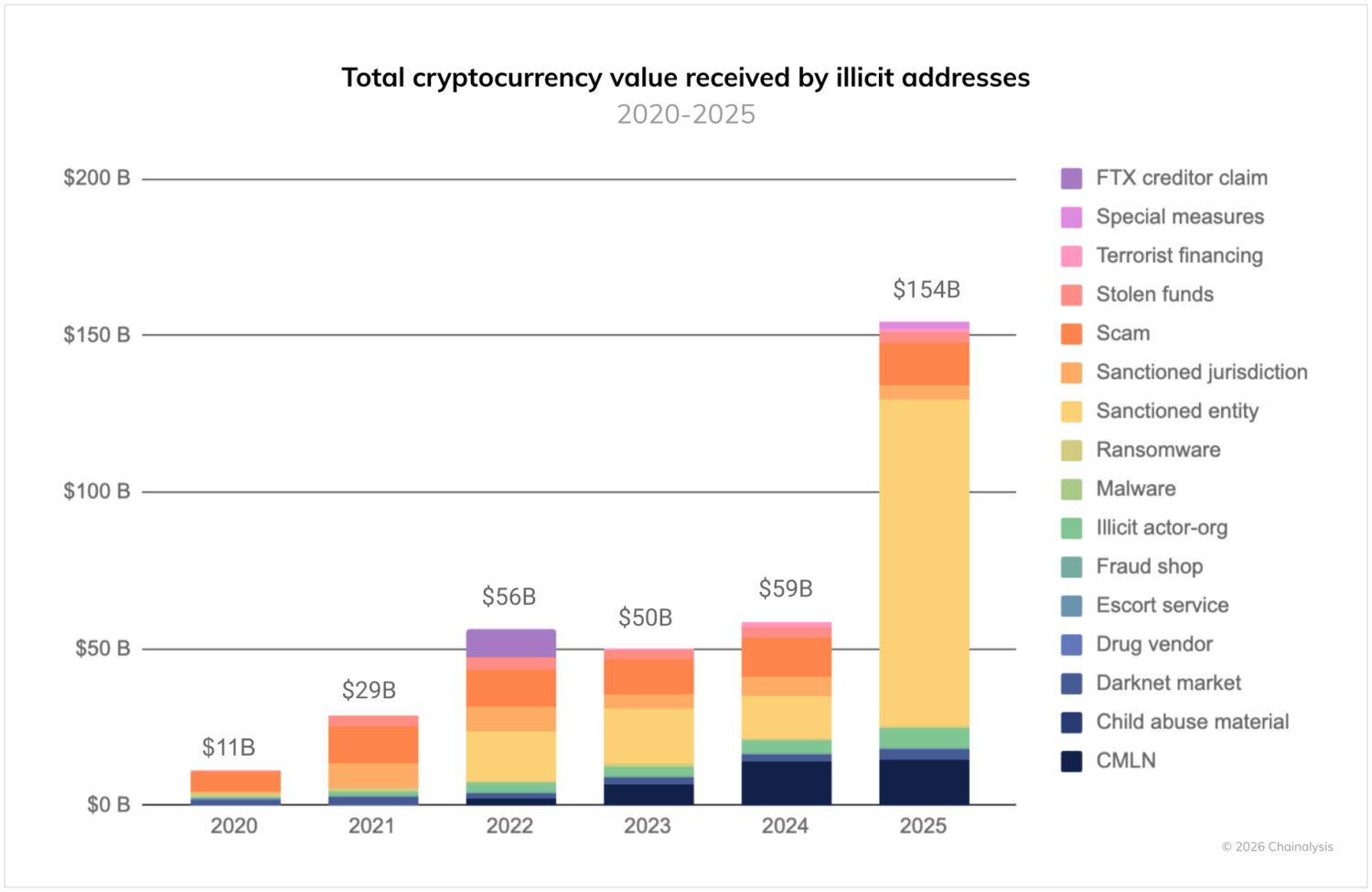
According to our data, illicit cryptocurrency addresses received at least $154 billion in 2025. This represents a 162% increase year-over-year (YoY), primarily driven by a dramatic 694% increase in the value received by sanctioned entities. But even if the value received by sanctioned entities were flat YoY, 2025 would still mark a record year for crypto crime, as activity increased across most illicit categories. As always, we must caveat that this figure represents a lower-bound estimate based on illicit addresses we’ve identified to date. [1]
These illicit volumes are still dwarfed by the broader crypto economy, which largely consists of legitimate transaction volumes. Our estimate for the illicit share of all attributed crypto transaction volume increased slightly from 2024 but remains below 1%. [2]
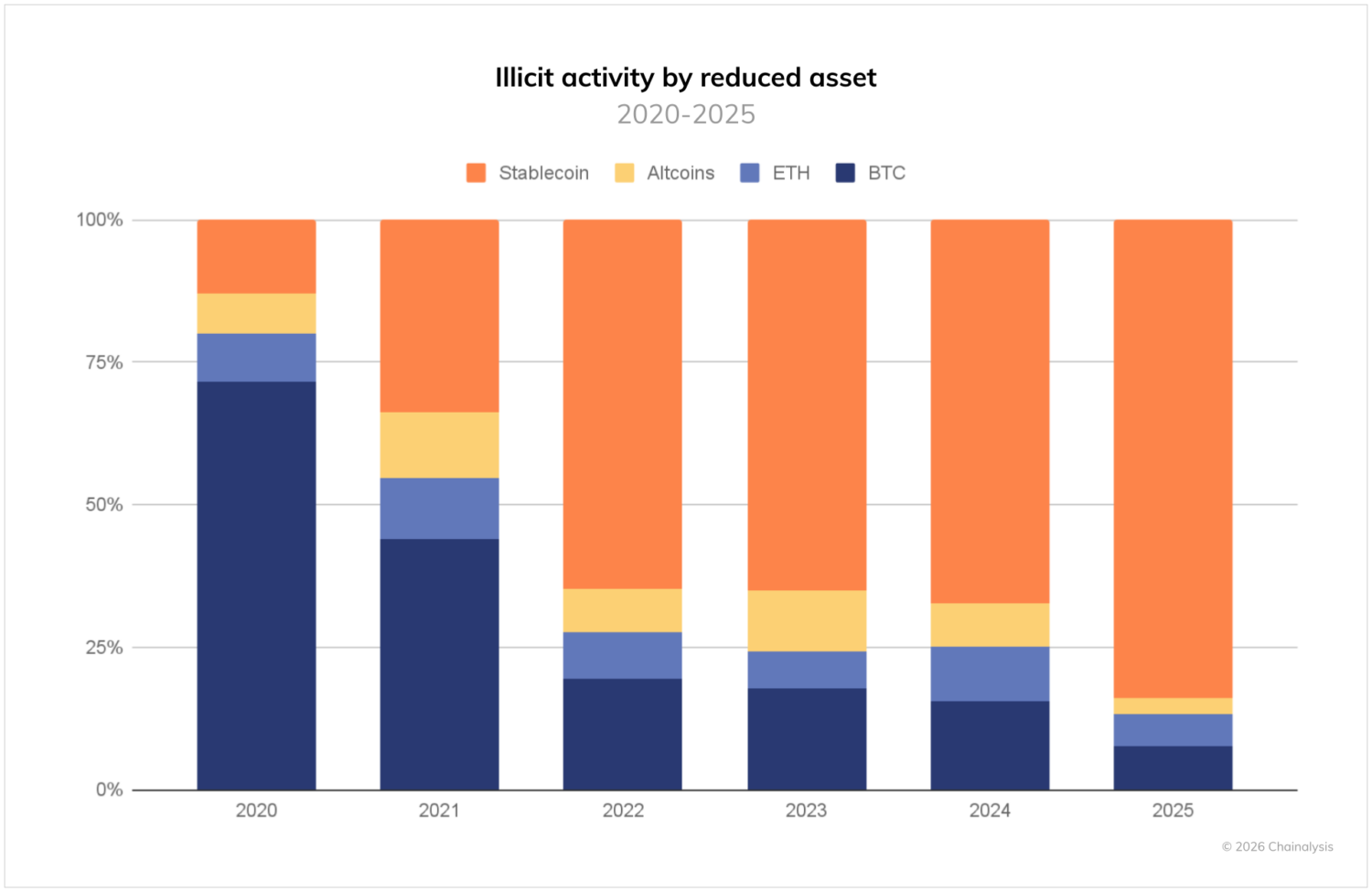
We are also observing a continued shift in the types of assets involved in crypto crime, as shown in the chart below.
For the past few years, stablecoins have come to dominate the landscape of illicit transactions, and now account for 84% of all illicit transaction volume. This mirrors broader ecosystem trends where stablecoins occupy a sizable and growing percentage of all crypto activity due to their practical benefits: easy cross-border transferability, lower volatility, and broader utility.
Below, we’ll take a closer look at four key trends that defined crypto crime in 2025 and will be important to watch going forward.
Nation-state threats drive record volumes: North Korea steals more than ever, and Russia’s A7A5 token facilitates large-scale sanctions evasion
Stolen funds remained a major threat to the ecosystem in 2025, with DPRK‑linked hackers alone stealing $2 billion. Devastating mega-hacks drive that total, most notably the February Bybit exploit, the largest digital heist in crypto history, at nearly $1.5 billion. Although North Korean hackers have long been a fixture of the threat landscape, the past year has been their most destructive yet, both in value stolen and in the sophistication of their intrusion and laundering tactics.
Perhaps most significantly, 2025 saw unprecedented volumes associated with nation-states’ on-chain behavior. While Russia introduced legislation in 2024 to facilitate sanctions evasion via crypto, these efforts came to fruition in February 2025, when the country launched its ruble-backed A7A5 token, transacting over $93.3 billion in less than one year.
Meanwhile, over the past several years Iran‘s proxy networks have continued to facilitate money laundering, illicit oil sales, and procurement of arms and commodities on-chain to the tune of $2+ billion through confirmed wallets identified in sanctions designations. Iran-aligned terrorist organizations, including Lebanese Hezbollah, Hamas, and the Houthis, are using cryptocurrency at scales never before observed, in spite of various military setbacks.
Chinese money laundering networks dominate the landscape
2025 has seen the emergence of Chinese money laundering networks (CMLNs) as a dominant force in the illicit on-chain ecosystem. These sophisticated operations have dramatically expanded the trend of crypto crime’s diversification and professionalization, offering a wide variety of specialized services including laundering-as-a-service and other criminal infrastructure. Building on the framework established by operations like Huione Guarantee, these networks have created full-service criminal enterprises that support everything from fraud and scams to North Korean hack proceeds, sanctions evasion, and terrorist financing.
Full-stack illicit infrastructure providers facilitate malicious cyber activity
While nation‑state use of crypto is rising, more “traditional” cybercrime remains very much alive: ransomware operators, CSAM platforms, malware distributors, scammers, and illicit marketplaces still depend on a dense layer of enablers to stay effective. Illicit actors and nation‑states alike are increasingly reliant on infrastructure providers that offer a full stack of services and are themselves visible on‑chain, including domain registrars, bulletproof hosting services, and other technical infrastructure that can be leveraged for malicious cyber activity.
These infrastructure providers have evolved from niche hosting resellers into integrated infrastructure platforms designed to withstand takedowns, abuse complaints, and sanctions enforcement. As these offerings continue to scale, they are likely to play a key role in supporting financially motivated criminals and state-aligned actors alike to amplify the reach of malicious cyber activity.
The rising intersection of crypto and violent crime
Many people still picture crypto crime as something purely virtual — faceless bad actors behind keyboards rather than threats that manifest in the physical world. In reality, we’re seeing growing connections between on-chain activity and violent crime. Human trafficking operations have increasingly leveraged cryptocurrency, while there has also been a particularly disturbing rise in physical coercion attacks, in which criminals use violence to force victims to transfer assets, often timing these assaults to coincide with cryptocurrency price peaks.
As we move forward, cooperation among law enforcement, regulatory bodies, and crypto businesses will be crucial in combating these evolving and converging threats. While the overall percentage of illicit activity remains small relative to legitimate crypto usage, the stakes have never been higher for maintaining the integrity and security of the cryptocurrency ecosystem.
[1] A year from now, these totals will be higher as we continue to identify more illicit addresses and incorporate their historical activity into our estimates. For perspective, when we published last year’s Crypto Crime Report, we reported $40.9 billion for 2024. One year later, our updated estimate for 2024 is substantially higher at $57.2 billion, with much of that growth coming from various types of illicit actor organizations providing on-chain infrastructure and laundering services for high-risk and illicit actors. In general, our totals exclude revenue from non-crypto-native crime, such as traditional drug trafficking and other crimes in which crypto may be used as a means of payment or laundering. Such transactions are virtually indistinguishable from licit transactions in on-chain data, although law enforcement with off-chain information can still investigate these crimes using Chainalysis solutions. In cases where we’re able to confirm such information, we count the transactions as illicit in our data.
[2] To calculate the illicit share of attributed transaction volumes, we determine the denominator by calculating all inflows to known services across all the assets that we track, excluding internal transfers within services. We then divide the illicit value received by the total value received by all services.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.