On September 2, 2025, a Venus Protocol user was targeted, putting approximately $13 million at risk. The attack was rooted in social engineering: malicious actors used a compromised Zoom client to gain system access. After infiltrating the victim’s machine, the attackers manipulated the user into submitting a blockchain transaction, which granted them delegate status over the account. This gave them direct control to borrow and redeem assets on behalf of the victim, effectively draining funds.
Decentralized finance often makes headlines for its innovation, but this incident shines a spotlight on what modern security best practices can achieve against even the most sophisticated attackers. Below, we’ll look at how Chainalysis Hexagate and the community of investigative experts not only stopped the hack but also enabled a swift recovery.
Early detection: Where Hexagate comes in
A month before the attack, Venus Protocol onboarded as a new Hexagate customer. This made all the difference. As a result, Hexagate’s platform surfaced suspicious, protocol-level activity early and before the funds were irreversibly lost. This rapid alerting enabled the Venus team to act with urgency. How this worked:
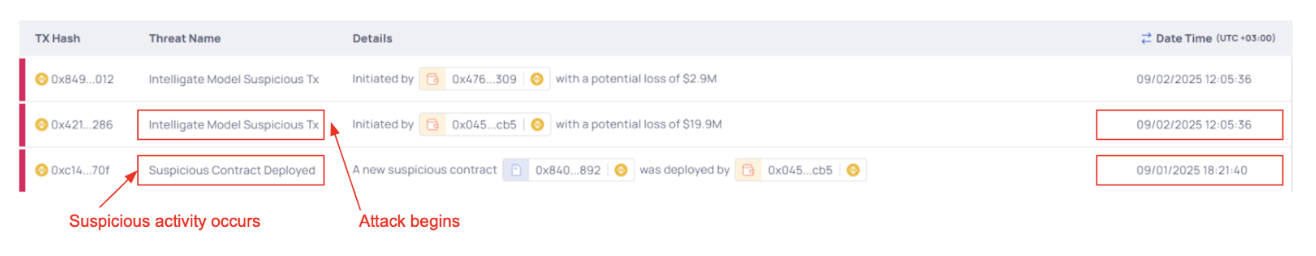
- The Hexagate platform picked up something suspicious related to Venus 18 hours before the actual incident and generated an alert.
- As soon as the attack began, Hexagate generated another alert which prompted the Hexagate team to contact Venus and advise them to immediately pause all markets.
- Within 20 minutes of the malicious transaction, Venus paused its protocol.
- This swift action safeguarded the user’s assets so that illicit actors could not move any funds and minimized broader market risk.
By distinguishing between real threats and normal market dynamics, Hexagate enabled the team to focus on critical events without being overwhelmed by misleading alerts.
Rapid recovery: Coordinated response and asset preservation
Once paused, Venus executed a multi-phase recovery plan:
- Security checks confirmed that their core dApp and front-end were uncompromised.
- Within five hours, partial functionality was restored where safe.
- Within seven hours, they force-liquidated the attacker’s wallet, further mitigating losses.
- Within 12 hours, stolen funds were fully recovered and full service resumed.
This was made possible by combining the real-time security monitoring and response from Hexagate, which detected the suspicious activity before it happened. The Venus Protocol team used these insights to communicate, coordinate, and execute lightning governance actions under time-critical, high-pressure conditions.
Governance as a security tool: Turning the tables
Perhaps the most impressive move, though, came after recovery.
Venus passed a governance proposal to freeze $3 million in assets still controlled by the attacker. Not only did the attacker fail to profit; they actually lost $3 million as a result of the community’s decisive action.
What this means for DeFi platforms and their users
The Venus Protocol case is more than a win; it’s a proof point for the future of DeFi security. Hexagate provided early warning, actionable intelligence, and continuous monitoring throughout the incident. Their monitoring and alerting transformed Venus’ incident response from “reactive” to “proactive” and as a result was able to keep one of their most valued customer’s funds from being stolen. This approach to security goes a long way in reinforcing confidence that DeFi platforms can protect their users when it matters most. After all, security isn’t just about stopping attacks, but about preserving trust in the entire ecosystem.
To do this, Hexagate actively scans a spectrum of threats across phishing, suspicious on-chain activity, and contract manipulation. With real-time monitors, Hexagate detects risky behavior 98% of the time before a hack happens. Additionally, Hexagate’s real-time alerts and notifications trigger fast-acting response workflows (such as pausing services or locking funds), enabling security teams to contain incidents within minutes.
This shows the transformative power of integrated real-time monitoring, on-chain analytics, and a detection-and-response approach built on collaborative action. It’s a blueprint for other DeFi protocols: attack prevention isn’t enough; rapid response, transparent investigation, and decisive governance are essential.
To see how Chainalysis’ Hexagate security solution can prevent potential attacks on your organization, book a demo here.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

