The goal of money laundering is to obscure the criminal origins of funds so that they can be accessed and spent. In the context of cryptocurrency-based crime, that generally means moving funds to services where they can be converted into cash, while often taking extra steps to conceal where the funds came from. Our on-chain analysis of crypto money laundering therefore focuses on two distinct groups of services and on-chain entities:
- Intermediary services and wallets. This category includes personal wallets, mixers, instant exchangers, various types of DeFi protocols, and other services both legitimate and illicit. Crypto criminals generally use services in this category to hold funds, or to obfuscate their criminal origins, often by obscuring the on-chain link between their source address and their current address.
- Fiat off-ramping services. This category includes any service where cryptocurrency can be converted into fiat currency, the most common being centralized exchanges. However, it can also include P2P exchanges, gambling services, and crypto ATMs. It’s also important to consider nested services that operate using the infrastructure of centralized exchanges and allow for fiat off-ramping, such as many OTC trade desks.
It’s important to remember that all of these services have different capabilities and options when it comes to addressing money laundering. Centralized exchanges, for instance, have much more control in that they can freeze funds coming from suspicious or illicit sources. DeFi protocols, however, generally don’t have this option, as they run autonomously and don’t take custody of users’ funds. Of course, DeFi protocols’ decentralized nature also means that blockchain analysts can generally trace funds moving through DeFi protocols to their next stop, which isn’t the case with centralized services. And of course, illicit services purposely facilitating money laundering can generally be stopped only through law enforcement operations or other legal processes. It’s also important to keep in mind that token issuers can play a positive role as well. Stablecoins like USDT and USDC, for instance, have functionalities allowing them to freeze assets held by addresses associated with crime.
With that in mind, let’s look at the key crypto money laundering trends of 2023.
2023 crypto money laundering: Key trends
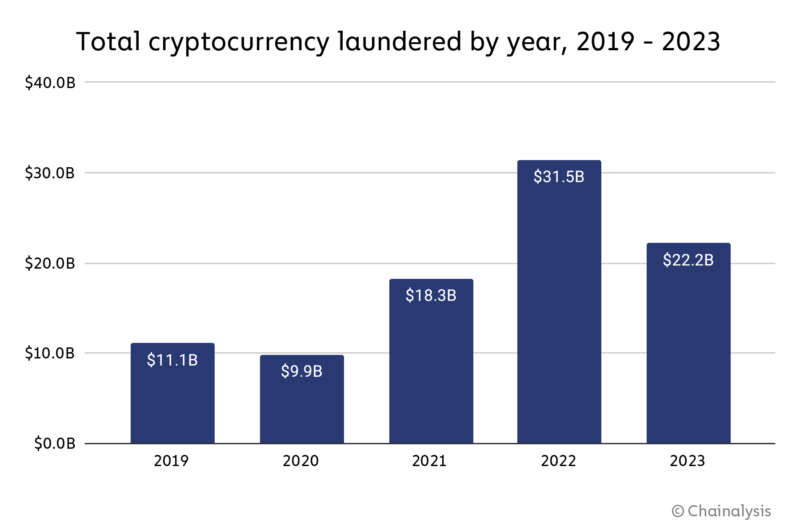
In 2023, illicit addresses sent $22.2 billion worth of cryptocurrency to services, which is a significant decrease from the $31.5 billion sent in 2022. Some of this drop may be attributed to an overall decrease in crypto transaction volume, both legitimate and illicit. However, the drop in money laundering activity was steeper, at 29.5%, compared to the 14.9% drop in total transaction volume.
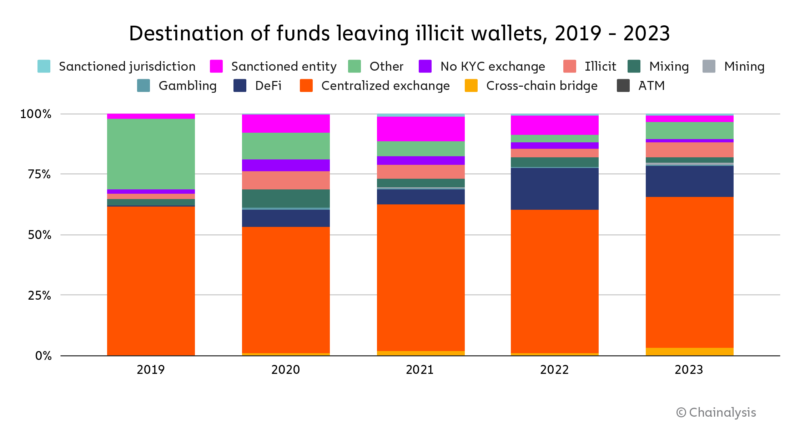
Overall, centralized exchanges remain the primary destination for funds sent from illicit addresses, at a rate that has remained relatively stable over the last five years. Over time, the role of illicit services has shrunk, while the share of illicit funds going to DeFi protocols has grown. We attribute this primarily to the overall growth of DeFi generally during the time period, but must also note that DeFi’s inherent transparency generally makes it a poor choice for obfuscating the movement of funds.
2023 mostly resembled 2022 in terms of the breakdown of service types used for money laundering, but we did see a slight decrease in the share of illicit funds moving to illicit service types, and an increase in funds moving to gambling services and bridge protocols.
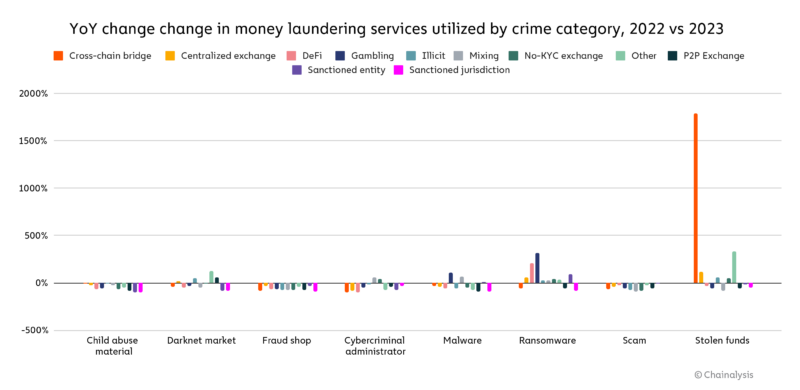
However, if we zoom in to look at how specific types of crypto criminals laundered money, we can see that there was in fact significant change in some areas. Most notably, we saw a huge increase in the volume of funds sent to cross-chain bridges from addresses associated with stolen funds, a trend we’ll examine in greater detail later. We also observed a substantial increase in funds sent from ransomware to gambling platforms, and in funds sent to bridges from ransomware wallets.
Money laundering concentration at fiat off-ramps
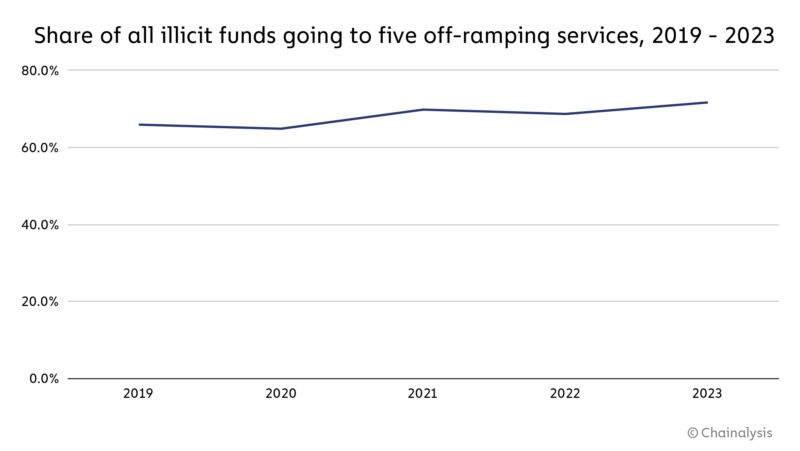
Fiat off-ramping services are important because they’re where criminals can convert their crypto into cash — the culmination of the money laundering process. While there are thousands of off-ramping services in operation, most money laundering activity is concentrated to a select few services. Of all illicit funds sent to off-ramping services in 2023, 71.7% went to just five services, up slightly from 68.7% in 2022.
We can also go one level deeper and examine money laundering concentration at the deposit address level. Deposit addresses are addresses at centralized services associated with individual users — you can think of them as akin to bank accounts. Examining money laundering activity at the deposit address level therefore lets us get a better sense of the individuals or nested services most directly responsible for the majority of crypto money laundering activity. Looking at things through this lens, we can see that money laundering actually became less concentrated at the deposit address level in 2023, even as it became slightly more concentrated at the service level.
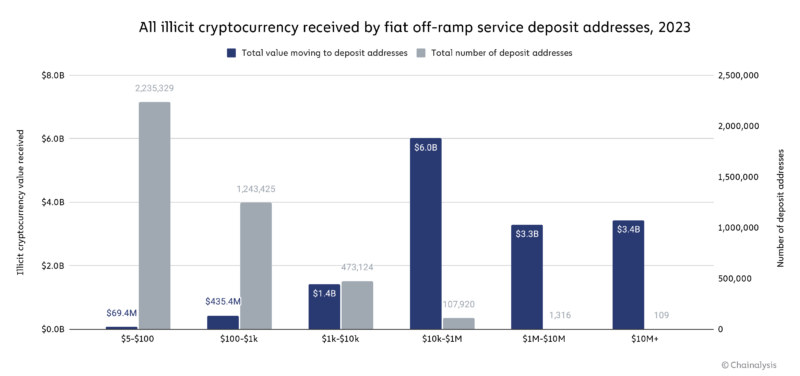
In 2023, 109 exchange deposit addresses received over $10 million worth of illicit cryptocurrency each, and collectively, they received $3.4 billion in illicit cryptocurrency. While that still represents significant concentration, in 2022, only 40 addresses received over $10 million in illicit crypto, for a collective total of just under $2.0 billion. In 2022, just 542 deposit addresses received over $1 million in illicit cryptocurrency, for a total of $6.3 billion, which was over half of all illicit value received by centralized exchanges that year. In 2023, 1,425 deposit addresses received over $1 million in illicit cryptocurrency, for a total of $6.7 billion, which accounts for just 46% of all illicit value received by exchanges for the year.
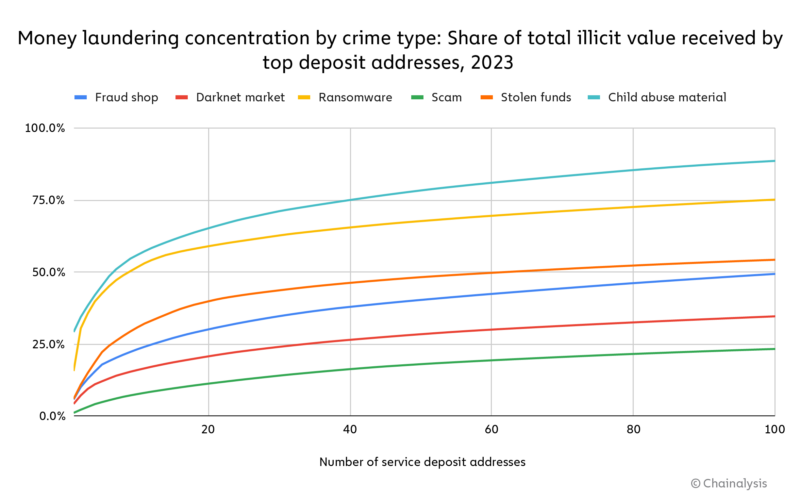
However, it’s also worth noting that money laundering concentration differs by criminal type. For instance, CSAM vendors and ransomware operators show a high degree of concentration — just seven deposit addresses account for 51.0% of all value received from CSAM vendors by exchanges, while for ransomware, just nine addresses account for 50.3%. On the other side of the spectrum, scams and darknet markets show much less concentration. Forms of crypto crime displaying higher concentration may be more vulnerable to law enforcement, as their money laundering activity relies on comparatively fewer services that can be disrupted.
Overall, it’s possible that crypto criminals are diversifying their money laundering activity across more nested services or deposit addresses in order to better conceal it from law enforcement and exchange compliance teams. Spreading the activity across more addresses may also be a strategy to lessen the impact of any one deposit address being frozen for suspicious activity. As a result, fighting crypto crime via the targeting of money laundering infrastructure may require greater diligence and understanding of interconnectedness through on-chain activity than in the past, as the activity is more diffuse.
Money laundering tactics changing: Most sophisticated crypto criminals utilizing bridges and mixers
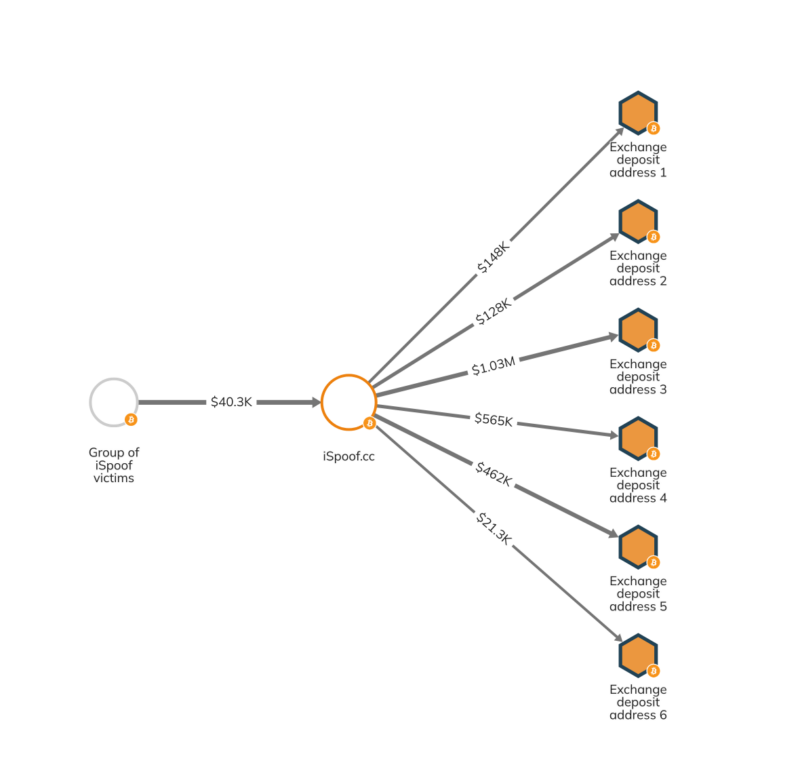
A big share of crypto money laundering activity is relatively unsophisticated, and consists of bad actors simply sending funds directly to exchanges. We can see this on the Chainalysis Reactor graph below, which shows the now-defunct phone number spoofing service iSpoof — which facilitated over £100 million in scamming activity before being shut down by law enforcement — sending millions in Bitcoin directly to a group of deposit addresses at a centralized exchange.
However, crypto criminals with more sophisticated on-chain laundering skill sets —such as the notorious North Korean cybercriminals associated with hacking gangs like Lazarus Group — tend to utilize a greater variety of crypto services and protocols. Below, we’ll look at two important ways sophisticated bad actors adjusted their money laundering strategy, illustrated through examples from Lazarus Group:
- Use of a new mixer following Sinbad’s takedown and OFAC designation
- Chain hopping via cross-chain bridges
Let’s look at both below.
New mixer: YoMix takes over for Sinbad
Overall, 2023 saw a decline in funds sent to mixers from illicit addresses, from $1.0 billion in 2022 to $504.3 million in 2023.
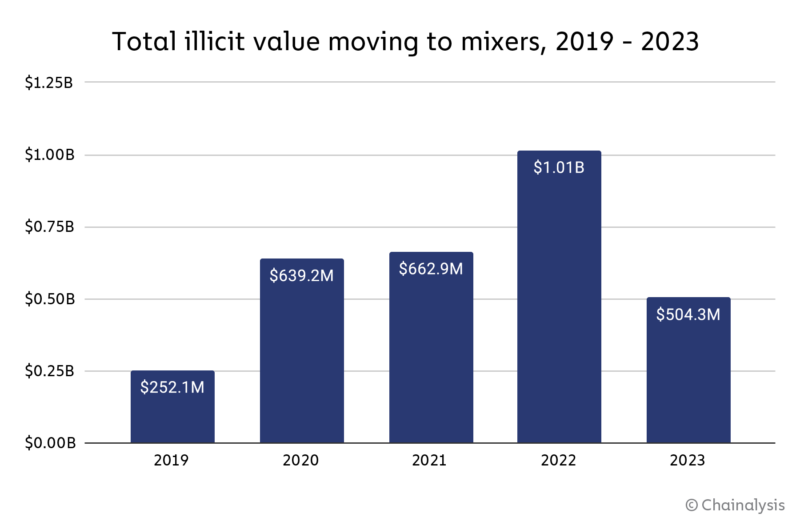
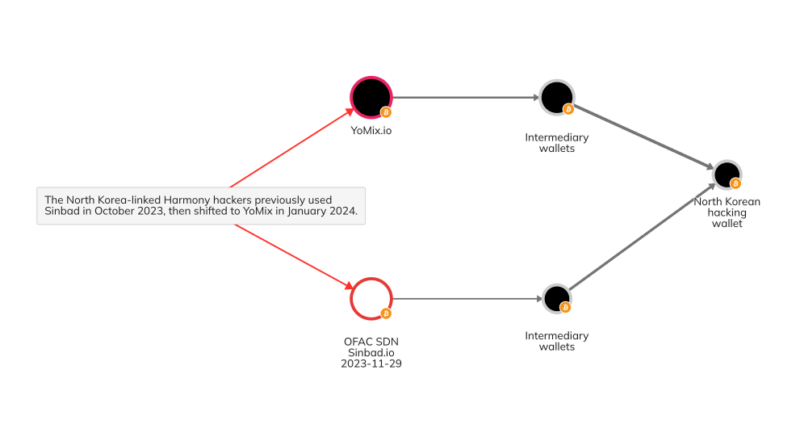
Much of this is likely due to law enforcement and regulatory efforts, such as the sanctioning and shutdown of mixer Sinbad in November 2023. But sophisticated cybercriminal groups like Lazarus Group have adapted their mixer usage. As we covered in last year’s Crypto Crime Report, Sinbad became a preferred mixer for North Korea-affiliated hackers in 2022, soon after the sanctioning of Tornado Cash, which had previously been the go-to for these sophisticated cybercriminals. With Sinbad out of the picture, Bitcoin-based mixer YoMix has acted as a replacement. We can see an example of this on the Reactor graph below, which shows a wallet associated with North Korean hacking activity receiving funds from YoMix, whereas it had previously received funds from Sinbad.
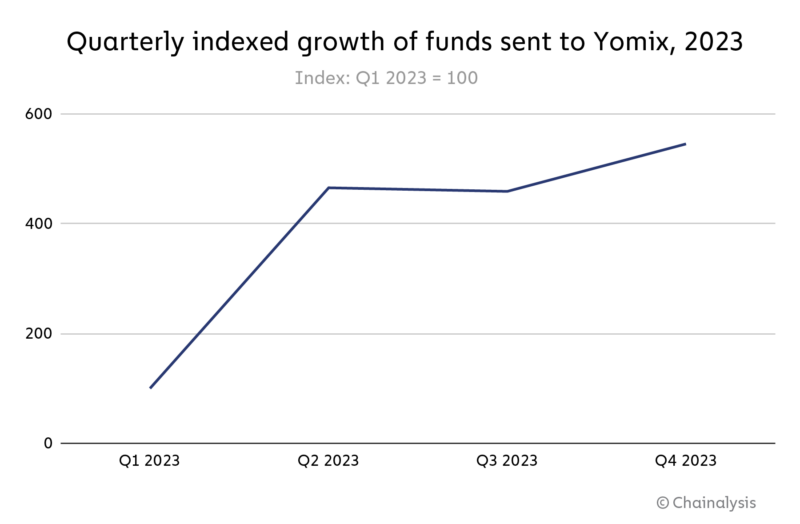
Overall, YoMix saw huge growth in 2023, with inflows growing by more than 5x over the course of the year.
Based on Chainalysis data, roughly one third of all YoMix inflows have come from wallets associated with crypto hacks. The growth of YoMix and its embrace by Lazarus Group is a prime example of sophisticated actors’ ability to adapt and find replacement obfuscation services when previously popular ones are shut down.
Use of cross-chain bridges
Cross-chain bridges allow users to move funds from one blockchain to another. Generally, anyone can access these smart contracts, although in theory a bridge could implement a blacklist. All of this activity happens on-chain, which means that blockchain analysts can trace funds through bridges, as no centralized entity ever takes custody of the funds that move to bridges.
As discussed previously, illicit actors’ use of bridge protocols for money laundering purposes grew substantially in 2023, particularly amongst crypto thieves.
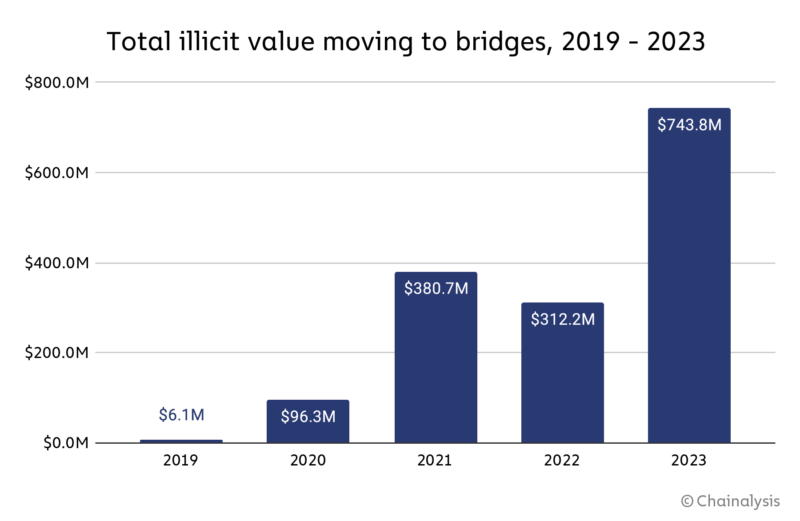
Overall, bridge protocols received $743.8 million in crypto from illicit addresses in 2023, up from just $312.2 million in 2022.
North Korea-affiliated hackers have been among those to utilize bridges for money laundering the most, and we can see an example of this activity on the Reactor graph below.
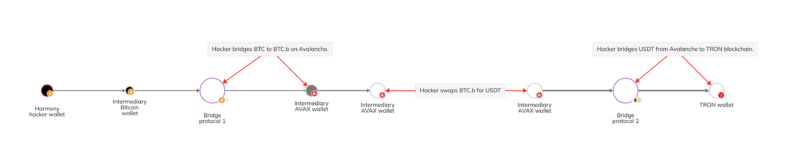
In this case, funds associated with the 2022 Harmony hack moved to a popular bridge protocol in May 2023, where they were moved from the Bitcoin blockchain to the Avalanche blockchain. The funds were then swapped for a stablecoin, and then bridged again using a different protocol, this time from the Avalanche blockchain to the TRON blockchain.
Sophisticated bad actors adapt frequently
The changes in money laundering strategy we’ve seen from crypto criminals like Lazarus Group serve as an important reminder that the most sophisticated illicit actors are always adapting their money laundering strategy and exploiting new kinds of crypto services. Law enforcement and compliance teams can be more effective by studying these new laundering methods and becoming familiar with the on-chain patterns associated with them.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.