On May 19, 2023, Tejay Fletcher, the administrator behind the fraud-enabling website iSpoof, was sentenced to more than 13 years in prison for stealing millions from victims in a banking scam. iSpoof was a service that helped scammers mask their phone numbers and impersonate legitimate companies. Criminals using iSpoof stole more than £100 million from victims worldwide and made approximately 10 million fraudulent phone calls between June 2021 and July 2022. At that point, a group of international agencies including the United Kingdom’s Metropolitan Police Service (MPS), Federal Bureau of Investigation (FBI), the United States Secret Service (USSS), and the Dutch National Police shut iSpoof down in a coordinated law enforcement effort called Operation Elaborate.

Operation Elaborate marks MPS’ “largest ever proactive fraud investigation” according to a press release from the department, and underlines the varied roles of cryptocurrency in scamming activity. In this case, while victims of the related scams weren’t paying fraudsters in crypto, the iSpoof service itself relied on crypto payments from its criminal user base. The case is an important reminder that in this day and age, law enforcement must be on the lookout for crypto nexuses even in cases where the role of cryptocurrency isn’t readily apparent. We’ll break the case down further below.
What was iSpoof?
iSpoof was a fraudulent website that enabled illicit actors to generate “spoofed” caller IDs to impersonate legitimate services and deceive victims. The below image was taken from an instructional video in iSpoof’s Telegram chat, where iSpoof representatives often communicated with users:

Criminals used iSpoof to convince victims that they were representatives from banks or government organizations, and warn victims of suspicious account activities. After these criminals gained confidence from their victims, they would request personal information, such as passwords, which they used to directly access financial accounts.
In some cases, these criminals were able to bypass multi-factor authentication methods by obtaining necessary security information directly from the victims. These activities led to victims in the U.K. losing more than £43 million and one victim losing as much as £2.5 million.
Using iSpoof’s services was unfortunately relatively easy. Criminals could purchase access to the site using Bitcoin for as little as £150 per month, with some “power users” paying as much as £5000 per month to access additional features.
Analyzing iSpoof’s on-chain transaction activity
Over the course of its lifetime, iSpoof received millions of pounds worth of Bitcoin. Most of these funds came from personal wallets belonging to criminals, but a significant portion also came from mainstream exchanges and crypto ATMs.
To launder its received Bitcoin, the iSpoof administrator sent funds directly to mainstream exchanges. The Chainalysis Reactor graph below shows some of this activity.
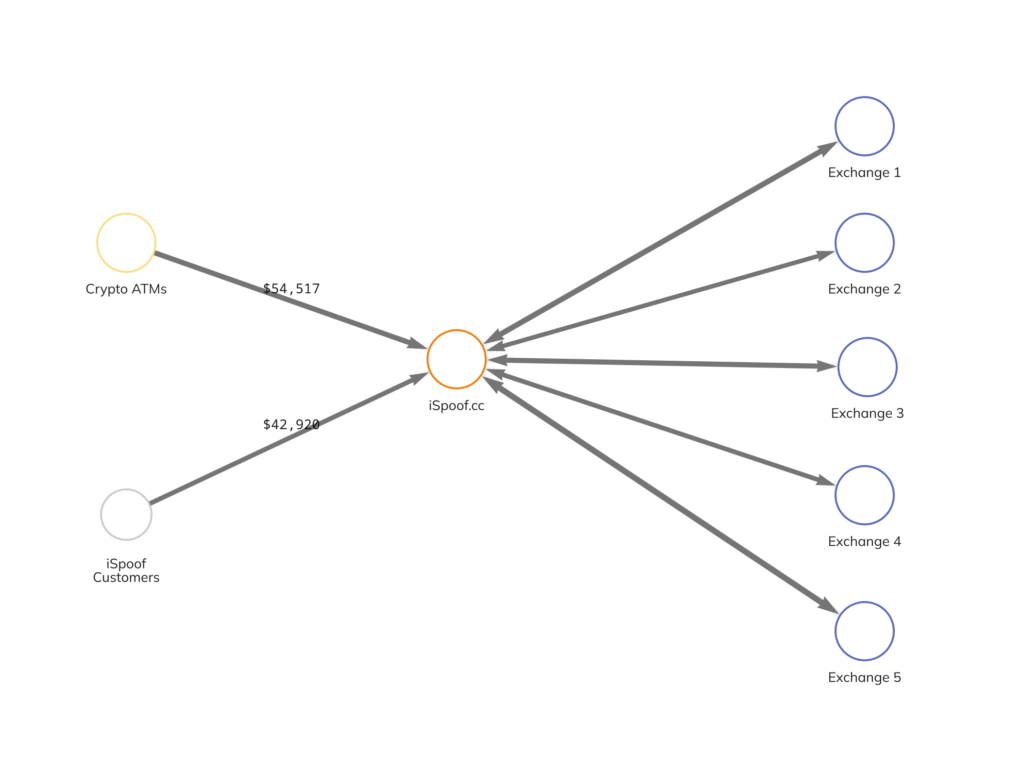
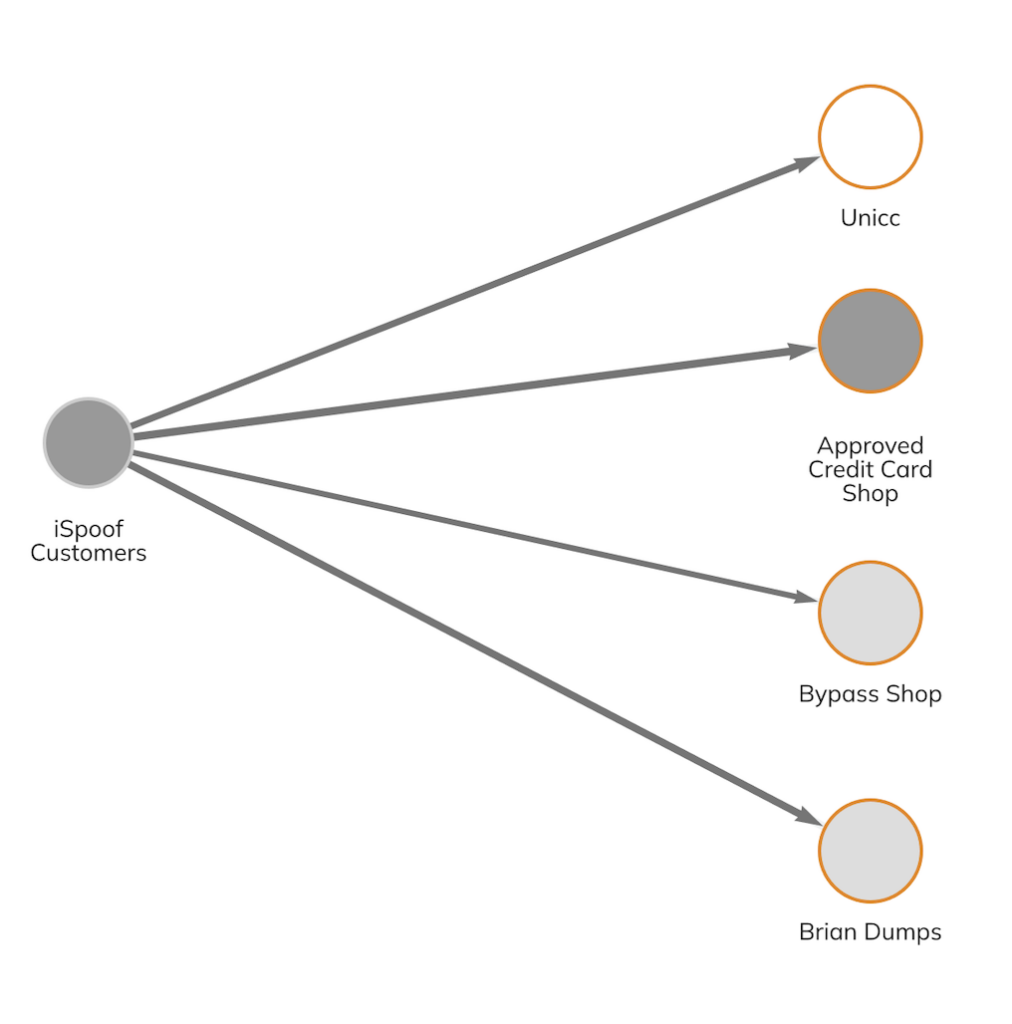
Upon further analysis, we discovered that criminals using iSpoof also sent funds to numerous high profile fraud shops, which are engaged in the sale of personal and sensitive information commonly used to commit fraud.
Using on-chain analysis to prevent malicious activities
The victory against iSpoof demonstrates law enforcement’s ability to reduce financial crime and track illicit transactions — especially if activity is conducted using cryptocurrency like Bitcoin. Analysis tools such as Chainalysis Reactor and KYT further empower law enforcement to identify criminals using cryptocurrency and take appropriate action. Additionally, the increasing role of cryptocurrency in illicit activities hints at a need for further investigation of on-chain activity in any criminal case.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

