The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) announced today that it has imposed sanctions on cryptocurrency mixer Sinbad.io (Sinbad). The U.S. Federal Bureau of Investigation (FBI), together with the Netherlands’ Fiscal Information and Investigation Service (FIOD) and other multilateral agencies, also seized Sinbad.io, effectively taking it offline. Sinbad was a key money laundering tool used by Lazarus Group — a sanctioned, state-sponsored group of cyber hackers of the Democratic People’s Republic of North Korea (DPRK).
Today’s OFAC action is a direct response to Sinbad’s role in laundering millions of dollars in stolen cryptocurrency, including funds stolen in the Harmony Horizon Bridge and Axie Infinity hacks.
What is Sinbad.io?
Operating on the Bitcoin blockchain, Sinbad is a mixing service that obscures transaction details in order to hide the flow of funds on-chain. Cryptocurrency mixing services, while potentially useful for legitimate privacy purposes, have become a prime instrument in the toolkit of cybercriminals, including North Korean-linked attackers.
Crypto mixers work by taking cryptocurrencies from various users, pooling them together, and then redistributing the funds to the designated recipients. This process is designed to obscure the otherwise transparent trail of transactions on a public blockchain. To date, crypto mixers have helped launder billions in illicit funds.
According to OFAC’s press release, experts believe that Sinbad emerged as a replacement for Blender.io, a mixing service sanctioned by OFAC in 2022. Overall, more than one third of funds sent to Sinbad during its lifetime have come from crypto hacks.
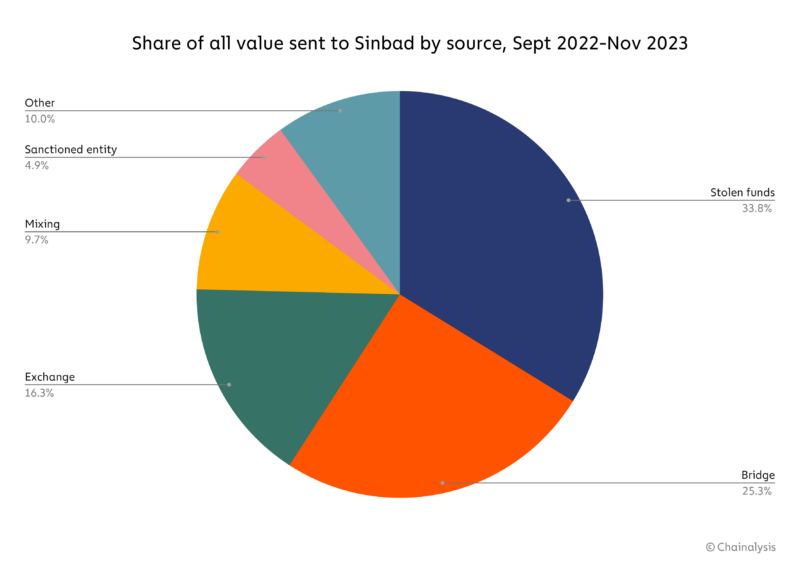
In addition to laundering stolen funds from Axie Infinity and Harmony Horizon Bridge, Sinbad was also used to launder portions of the $100 million stolen from Atomic Wallet users. All of these attacks have been attributed to the Lazarus Group.
Sanctioned by OFAC in 2019, Lazarus Group has been implicated in stealing over $3 billion worth of cryptocurrency. Cryptocurrency stolen by DPRK sponsored groups has been used to ultimately fund North Korea’s weapons programs.
Tracking Sinbad.io on-chain
Following the takedown of Tornado Cash and Blender.io last year, Sinbad emerged as the mixer of choice for DPRK-based hacking activities.
As we reported in February, North Korean hackers transferred approximately 1,429.6 bitcoin, valued around $24.2 million, to the mixer between December 2022 and January 2023. This includes funds converted from ETH to BTC, part of stolen funds from the Axie Infinity hack.
Additionally, Sinbad has been known to mix funds associated with other nefarious activities, including drug trafficking, the purchase of child sex abuse materials (CSAM), illicit sales on darknet marketplaces, and sanctions evasion.
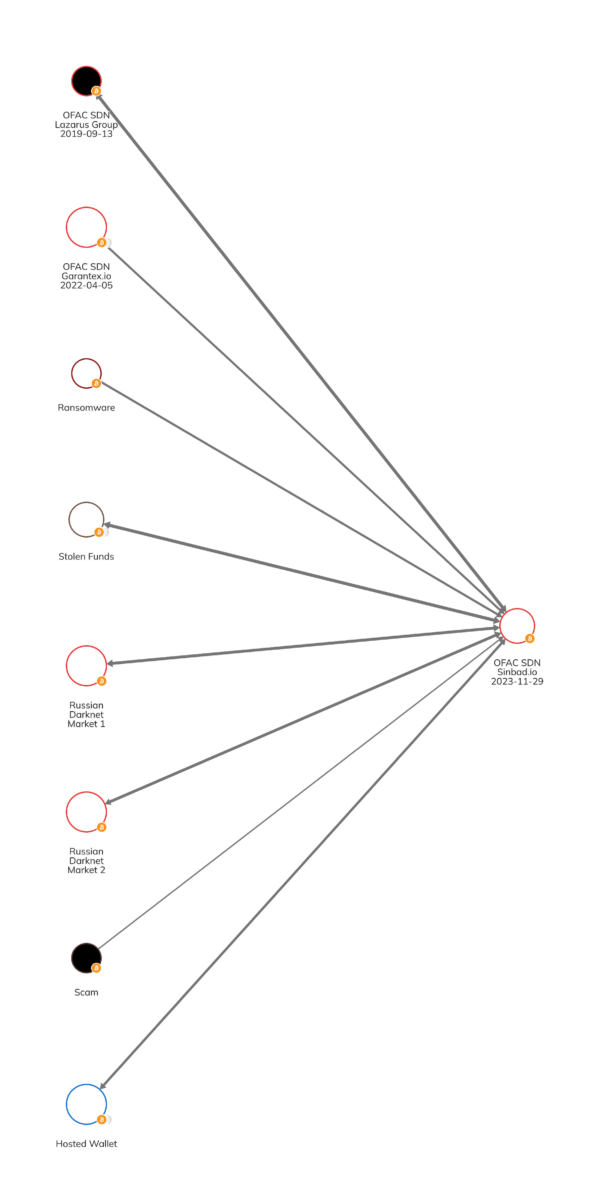
Below we can observe some of the illicit services that have sent funds to and received funds from Sinbad, including ransomware actors, various darknet markets, scams and even from Garantex, which was sanctioned in April of 2022, alongside Hydra, the darknet market.
Are you a Reactor user? View this graph.
Below we see outbound flows from Sinbad to CSAM-related entities specifically, indicating users utilized Sinbad to obfuscate the origin of their funds before purchasing CSAM material.

Are you a Reactor user? View this graph.
Cryptocurrency addresses associated with Sinbad.io
The following bitcoin addresses linked to Sinbad were added to OFAC’s Specially Designated Nationals and Blocked Persons List (SDN List):
- bc1qq7p0es3dv5hcynjjf40f2xjjr6qp5py47d2f6n847vduuq9gvnyq7y9ecd
- 1JHdQHkBZiim1cb4hyUh2PbzEbbg6z2TrF
Chainalysis has additionally identified a number of other addresses related to the mixer, all of which are now labeled to reflect today’s sanctions designation in Chainalysis products.
OFAC lands another blow against crypto money laundering
Today’s OFAC action follows last year’s historic sanctions against crypto mixers Blender.io and Tornado Cash. Like Sinbad, both services were implicated in providing mixer services to Lazarus Group.
This move by the U.S. Treasury highlights a continued effort to disrupt financial networks that facilitate illicit activities, especially those carried out by hostile nation state actors.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

