In 2023, ransomware actors intensified their operations, targeting high-profile institutions and critical infrastructure, including hospitals, schools, and government agencies. Major ransomware supply chain attacks were carried out exploiting the ubiquitous file transfer software MOVEit, impacting companies ranging from the BBC to British Airways. As a result of these attacks and others, ransomware gangs reached an unprecedented milestone, surpassing $1 billion in extorted cryptocurrency payments from victims.
Last year’s developments highlight the evolving nature of this cyber threat and its increasing impact on global institutions and security at large.
2023: A watershed year for ransomware
2023 marks a major comeback for ransomware, with record-breaking payments and a substantial increase in the scope and complexity of attacks — a significant reversal from the decline observed in 2022, which we forewarned in our Mid-Year Crime Update.
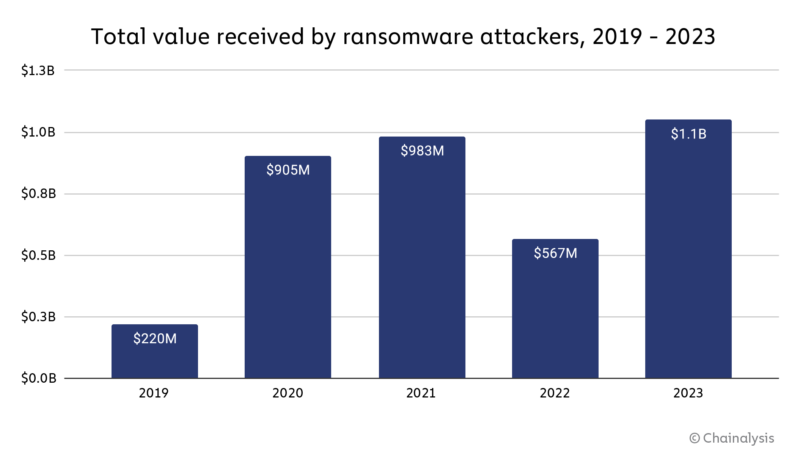
Ransomware payments in 2023 surpassed the $1 billion mark, the highest number ever observed. Although 2022 saw a decline in ransomware payment volume, the overall trend line from 2019 to 2023 indicates that ransomware is an escalating problem. Keep in mind that this number does not capture the economic impact of productivity loss and repair costs associated with attacks. This is evident in cases like the ALPHV-BlackCat and Scattered Spider’s bold targeting of MGM resorts. While MGM did not pay the ransom, it estimates damages cost the business over $100 million.
The ransomware landscape is not only prolific but continually expanding, making it challenging to monitor every incident or trace all ransom payments made in cryptocurrencies. It is important to recognize that our figures are conservative estimates, likely to increase as new ransomware addresses are discovered over time. For instance, our initial reporting for 2022 in last year’s crime report showed $457 million in ransoms, but this figure has since been revised upward by 24.1%.
Looking back at 2022: An anomaly, not a trend
Several factors likely contributed to the decrease in ransomware activities in 2022, including geopolitical events like the Russian-Ukrainian conflict. This conflict not only disrupted the operations of some cyber actors but also shifted their focus from financial gain to politically motivated cyberattacks aimed at espionage and destruction.
As we noted in our 2023 Crypto Crime Report, other factors that played a role in this downturn included a reluctance among some Western entities to pay ransoms to certain strains due to potential sanctions risks. Conti in particular faced issues, suffering from reported links to sanctioned Russian intelligence agencies, exposure of the organization’s chat logs, and overall internal disarray. This led to a decrease in their activities and contributed to the overall reduction in ransomware incidents in 2022. But researchers have noted that many ransomware actors linked to Conti have continued to migrate or launch new strains, making victims more willing to pay.
Another significant factor in the reduction of ransomware in 2022 was the successful infiltration of the Hive ransomware strain by the Federal Bureau of Investigation (FBI), as announced by the Department of Justice early in 2023. Our analysis highlights the substantial impact of this single enforcement action.
Law enforcement takes on ransomware: The Hive intervention
During the infiltration of Hive, the FBI was able to provide decryption keys to over 1,300 victims, effectively preventing the need for ransom payments. The FBI estimates that this intervention prevented approximately $130 million in ransom payments to Hive. But the impact of this intervention extends further than that. Total tracked ransomware payments for 2022 currently stand at just $567 million, indicating the ransom payments prevented by the Hive infiltration significantly altered the ransomware landscape as a whole last year.
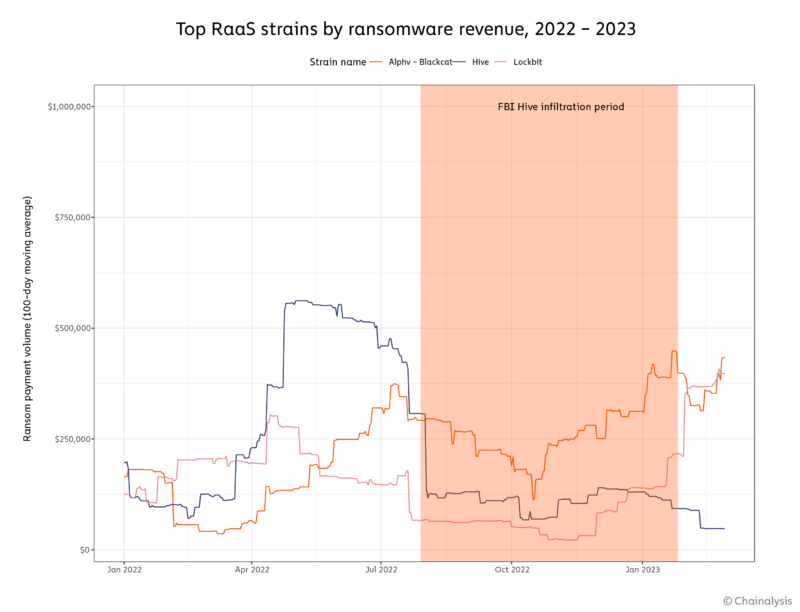
Furthermore, the FBI’s $130 million reduced payment estimate may not tell the whole story of just how successful the Hive infiltration was. That figure only looks directly at ransoms averted through the provision of decryptor keys, but does not account for knock-on effects. The Hive infiltration also most likely affected the broader activities of Hive affiliates, potentially lessening the number of additional attacks they could carry out.
During the six months the FBI infiltrated Hive, total ransomware payments across all strains hit $290.35 million. But our statistical models estimate an expected total of $500.7 million during that time period, based on attacker behavior in the months before and after the infiltration — and that’s a conservative estimate. Based on that figure, we believe the Hive infiltration may have averted at least $210.4 million in ransomware payments.
FBI’s Tampa Division Special Agent in Charge, David Walker, provided further insights into the importance of the infiltration. “The Hive investigation is an example of a gold standard for deploying the key services model.” Said Walker. “The FBI continues to see, through its investigations and victim engagements, the significant positive impact actions such as the Hive takedown have against cyber threat actors. We will continue to take proactive disruptive measures against adversaries.”
Ransomware resurges: 2023 threat landscape
In 2023, the ransomware landscape saw a major escalation in the frequency, scope, and volume of attacks.
Ransomware attacks were carried out by a variety of actors, from large syndicates to smaller groups and individuals — and experts say their numbers are increasing. Allan Liska, Threat Intelligence Analyst at cybersecurity firm Recorded Future, notes, “A major thing we’re seeing is the astronomical growth in the number of threat actors carrying out ransomware attacks.” Recorded Future reported 538 new ransomware variants in 2023, pointing to the rise of new, independent groups.
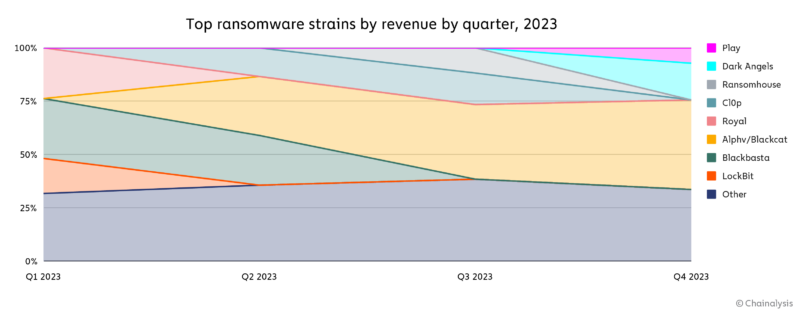
We can see some of that variety on the graph below, which shows the most active ransomware strains by quarter for 2023.
We can also see significant differences in the victimization strategies of the top ransomware strains on the chart below, which plots each strain’s median ransom size versus its frequency of attacks. The chart also illustrates numerous new entrants and offshoots in 2023, who we know often reuse existing strains’ code. This suggests an increasing number of new players, attracted by the potential for high profits and lower barriers to entry.
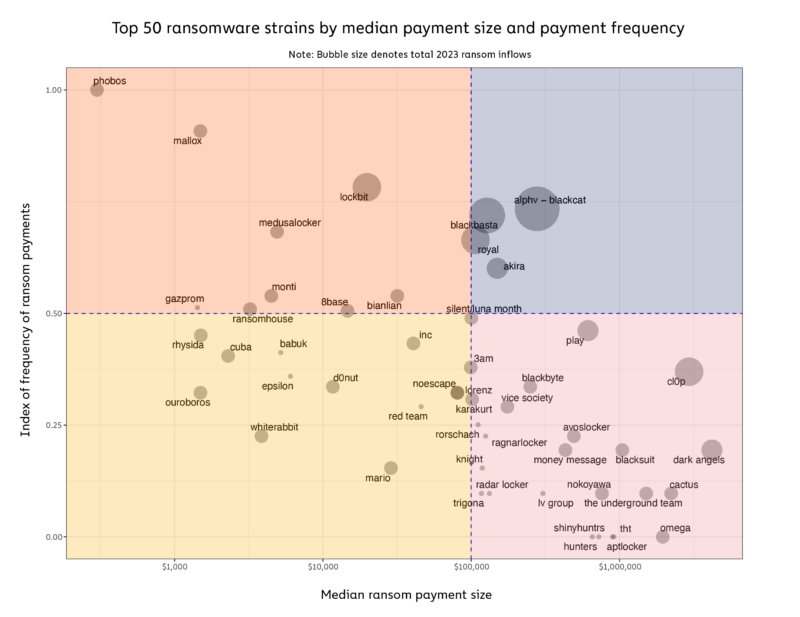
Some strains, like Cl0p, exemplify the “big game hunting” strategy, carrying out fewer attacks than many other strains, but collecting large payments with each attack. As we’ll explore later, Cl0p leveraged zero-day vulnerabilities that allowed it to extort many large, deep-pocketed victims en masse, spurring the strain’s operators to embrace a strategy of data exfiltration rather than encryption.
Overall, big game hunting has become the dominant strategy over the last few years, with a bigger and bigger share of all ransomware payment volume being made up of payments of $1 million or more.
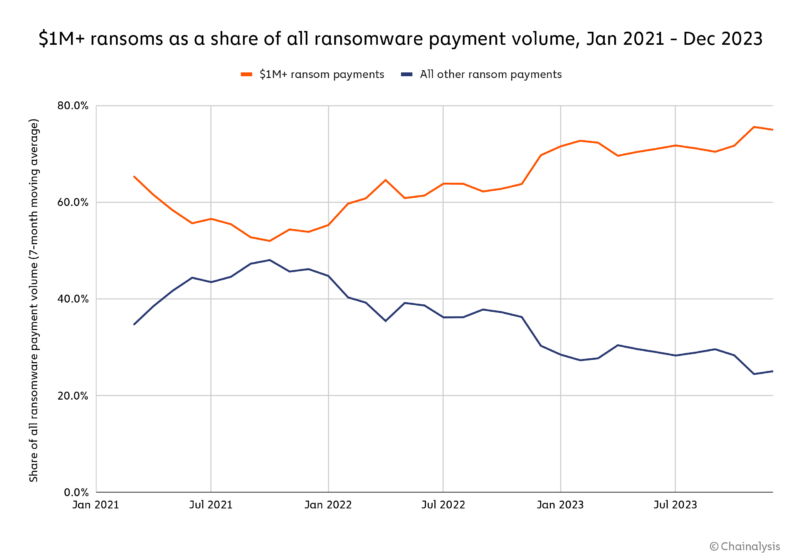
Other strains, like Phobos, have adopted the Ransomware as a Service (RaaS) model, in which outsiders known as affiliates can access the malware to carry out attacks, and in exchange pay the strain’s core operators a cut of the ransom proceeds. Phobos simplifies the process for less technically sophisticated hackers to execute ransomware attacks, leveraging the typical encryption process that is the hallmark of ransomware. Despite targeting smaller entities and demanding lower ransoms, the RaaS model is a force multiplier, enabling the strain to carry out a large quantity of these smaller attacks.
ALPHV-BlackCat is also a RaaS strain like Phobos, but is more selective in the affiliates it allows to use its malware, actively recruiting and interviewing potential candidates for their hacking capabilities. This enables the group to attack bigger targets for larger sums.
It’s also important to keep in mind that rebranding and overlapping strain usage remains prevalent for ransomware attackers. As we’ve covered previously, ransomware administrators often rebrand or launch new strains, while affiliates often switch strains or work for multiple simultaneously. Rebrands often allow ransomware attackers to distance themselves from strains publicly linked to sanctions or that have incurred too much scrutiny. Rebrands and affiliate switching can also allow attackers to hit the same victims twice under different strain names.
Fortunately, blockchain analysis makes it possible to identify ransomware rebrands, by showing on-chain links between wallets of seemingly disparate strains. We can see an example on the Chainalysis Reactor graph below, which shows links between the Trickbot administrator known as Stern, Royal ransomware, and its newer iteration known as 3am.
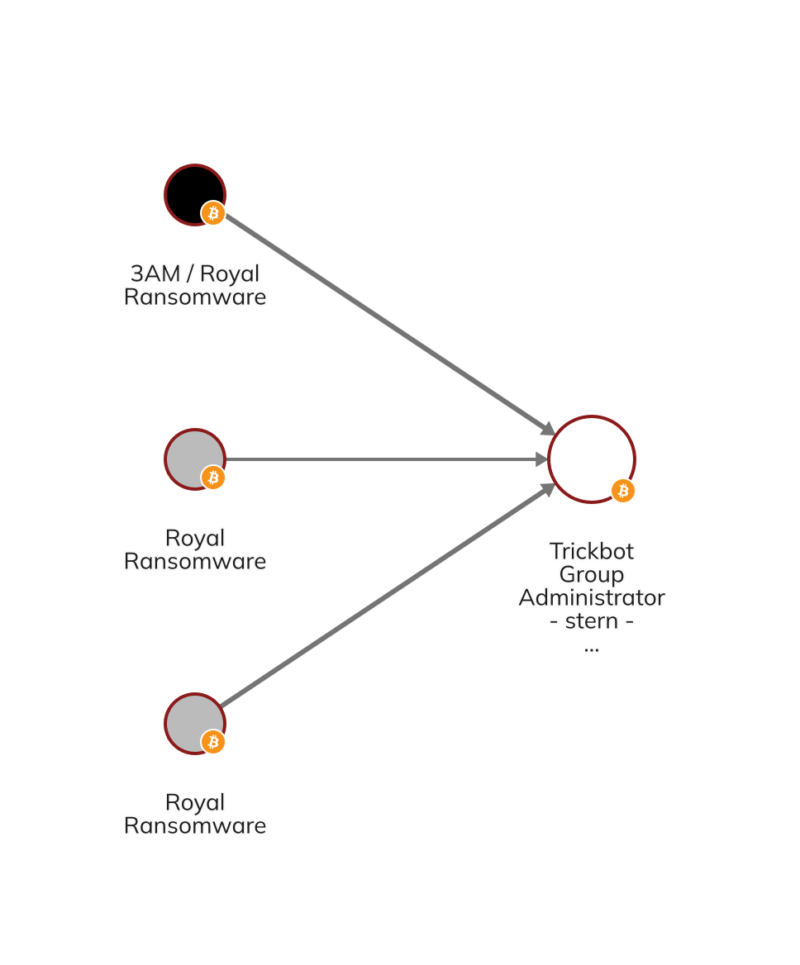
The frequency of rebranding, especially among actors behind the biggest and most notorious strains, is an important reminder that the ransomware ecosystem is smaller than the large number of strains would make it appear.
The spread of Ransomware-as-a-Service (RaaS) and availability of hacking tools have made it easier to launch attacks
The growth of initial access brokers (IABs) has made it easier for bad actors to carry out ransomware attacks. As their name would suggest, IABs penetrate the networks of potential victims, then sell that access to ransomware attackers for as little as a few hundred dollars. We found a correlation between inflows to IAB wallets and an upsurge in ransomware payments, suggesting monitoring IABs could provide early warning signs and allow for potential intervention and mitigation of attacks.
IABs combined with off-the-shelf RaaS, means that much less technical skill is required to carry out a successful ransomware attack. Andrew Davis, General Counsel at Kivu Consulting, a firm specializing in cybersecurity incident response, told us more about this trend. “The increase in attack volume can be attributed to the affiliate model’s ease of access and the adoption of ransomware-as-a-service, a disturbingly effective business model for cybercriminals,” said Davis.
We can see examples of this activity on the Reactor graph below, which shows a ransomware operator sending funds to several IABs and other purveyors of tools useful for ransomware attacks.
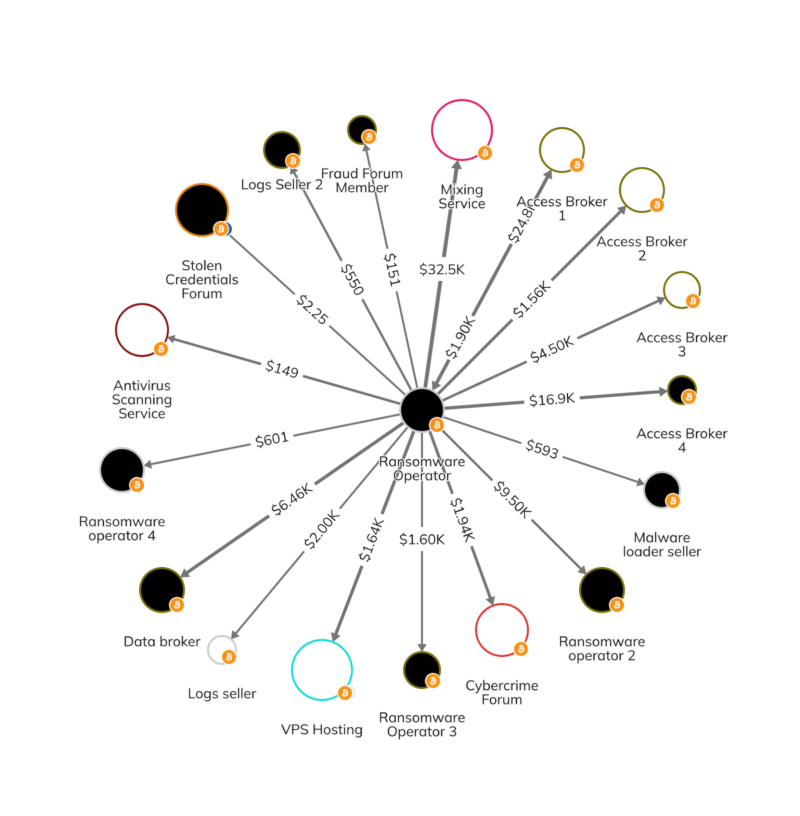
The ransomware actors depicted above have executed attacks that have brought in millions of dollars.
Cl0p case study: How zero-day attacks enable big game hunting
2023 was remarkable for the number of high-impact ransomware incidents that utilized zero-day vulnerabilities, which are particularly beneficial for threat actors because they leverage security gaps before developers have the opportunity to create and distribute a fix. Zero-day exploits can be even more damaging if they affect software that is ubiquitous but not well-known to end users who are the ultimate victims of an attack, usually because the software is used primarily by vendors serving those end users.
Cl0p’s most notorious attack of 2023 was its exploitation of the MOVEit zero-day. MOVEit is a file transfer software used by many IT and cloud applications, so this vulnerability exposed the data of hundreds of organizations and millions of individuals at once. “Many victims of the MOVEit exploitation did not know that they were affected because they were not aware that they were exposed to the software,” said Allan Liska of Recorded Future.
Beginning in May of 2023, Cl0p began exploiting the MOVEit vulnerability, enabling the group to target a huge number of victims. With so many targets, encrypting data and distributing decryptor keys to those who pay becomes logistically impractical. Data exfiltration – stealing data without blocking access and threatening to release it to the public – proves to be a more efficient tactic and hedges against possible decryptors foiling the attack. Lizzie Cookson, Senior Director of Incident Response at Coveware, comments on this tactic. “Encryption requires more expertise, resources, and a specific type of victim landscape,” said Cookson. “Exfiltration requires less dwell time, less experience and skill to execute and can often be accomplished without malicious software.”
Cl0p’s MOVEit campaign allowed it to become for a time the most prominent strain in the entire ecosystem, amassing over $100 million in ransom payments and accounting for 44.8% of all ransomware value received in June, and 39.0% in July.
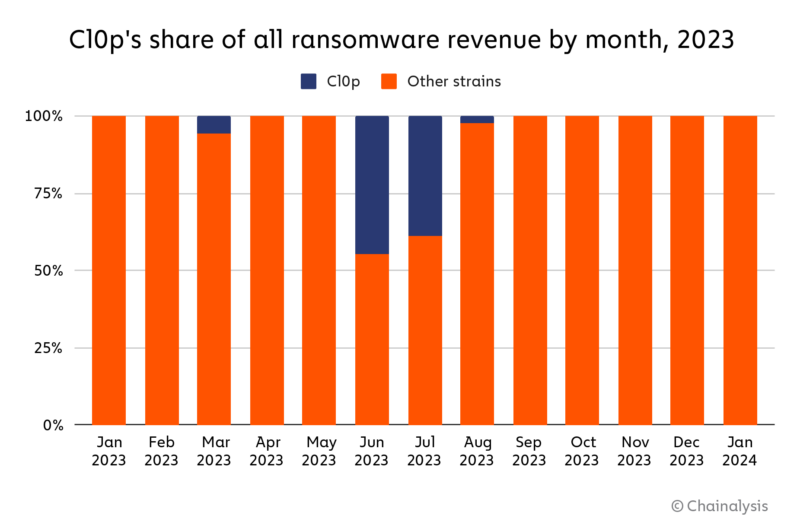
In addition to being extremely lucrative, Cl0p’s MOVEit campaign shows that leaner extortion efforts can still get victims to pay.
Ransomware off-ramping: Where do the funds go?
Analyzing the movement of ransomware funds provides essential insights into the methods and services used by threat actors, enabling law enforcement to target and disrupt their financial networks and infrastructure.
It’s important to keep in mind that threat actors may take weeks, months, or even years to launder their proceeds from ransomware, and so some of the laundering observed in 2023 is from attacks that occurred well into the past.
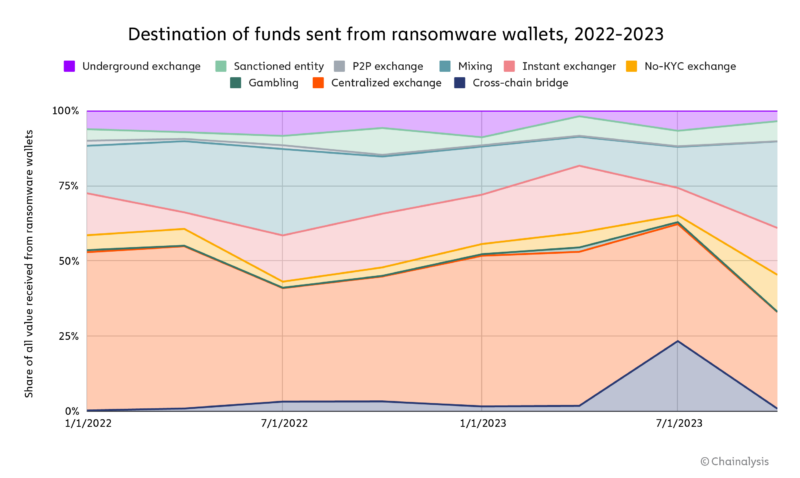
Centralized exchanges and mixers have consistently represented a substantial share of transactions, suggesting they are preferred methods for laundering ransomware payments.
However, this year saw the embrace of new services for laundering, including bridges, instant exchangers, and gambling services. We assess that this is a result of takedowns disrupting preferred laundering methods for ransomware, some services’ implementation of more robust AML/KYC policies, and also as an indication of new ransomware actors’ unique laundering preferences.
We also see significant concentration in the specific services within each category that ransomware actors turn to for laundering.
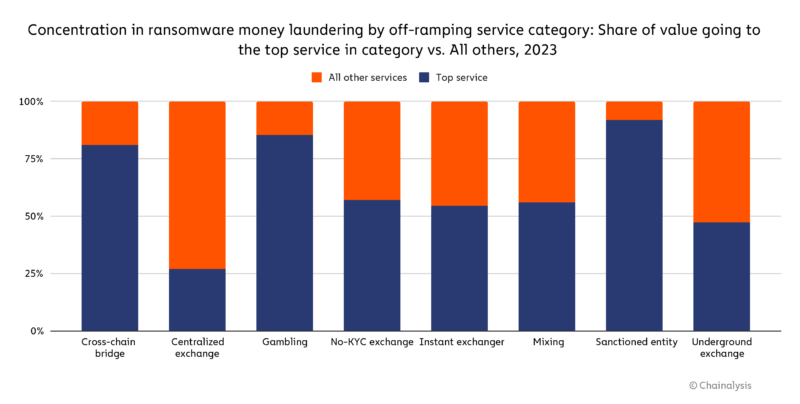
Exchanges showed the lowest level of concentration, while gambling services, cross-chain bridges, and sanctioned entities showed the highest levels of concentration. Mixers, no-KYC exchanges, and underground exchanges were in the middle, with roughly half of all funds sent to each category from ransomware wallets went to one service. Mixer concentration may have increased as a result of the Chipmixer takedown, which eliminated a popular option for ransomware attackers. In general, this overconcentration may expose ransomware actors to bottlenecks that make them vulnerable, as law enforcement could significantly disrupt operations by taking down a relatively small number of services.
Lessons from 2023
The ransomware landscape underwent significant changes in 2023, marked by shifts in tactics and affiliations among threat actors, as well as the continued spread of RaaS strains and swifter attack execution, demonstrating a more efficient and aggressive approach. The movement of affiliates highlighted the fluidity within the ransomware underworld and the constant search for more lucrative extortion schemes.
Threat actors continue to innovate and adapt to regulatory changes and law enforcement actions, but 2023 also saw significant victories in the fight against ransomware with collaboration between international law enforcement, affected organizations, cybersecurity firms, and blockchain intelligence. Lizzie Cookson of Coveware pointed out, “The Hive takedown and the BlackCat disruption are both great examples of how the FBI has been prioritizing victims’ assistance, helping victims and imposing costs on bad actors.” Andrew Davis of Kivu Consulting also noted an uptick in proactive engagement from law enforcement, indicating a stronger, more determined approach to aiding victims and tracking down cybercriminals.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

