A historic surge of ransomware incidents and payment totals in 2023 was not without resistance, as significant actions were taken against ransomware actors in 2023 and early 2024, including notable disruptions on Qakbot malware, and the LockBit and ALPHV-BlackCat ransomware-as-a-service (RaaS) groups.
At the same time, the diversification of malware strains and services, reinvestment in future attacks, and the ability to quickly adapt and rebrand in the face of adversity speaks to the resilient dynamic nature of threat actors in the ransomware ecosystem.
While disruptions are impactful, the persistence of ransomware affiliates challenges the lasting effectiveness of these measures. To counter this, a concerted effort involving both the public and private sectors is essential, as is broadening the scope of countermeasures. By focusing on the cumulative impact of these disruptions, it is possible to improve the long-term effect of actions targeting ransomware threats.
Ransomware: Easier to deploy, harder to profit
Ransomware activity remains elevated year-over-year. 2023 saw record ransom payment totals, as well as a 70% increase in the number of victims, according to cybersecurity firm Recorded Future’s analysis of dedicated leak sites (DLS).
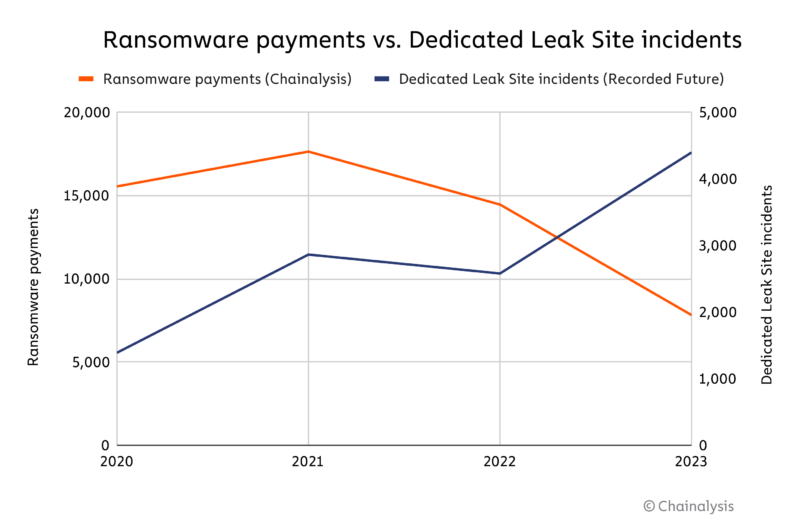
Recorded Future’s method offers a more comprehensive estimate of total victims, providing a valuable proxy to assess the scale of attacks globally. “Recorded Future employs multiple scrapers to pull data from ransomware extortion sites multiple times a day. We also have a team that maintains those scrapers because these sites are so unreliable,” said Allan Liska, Threat Intelligence Analyst at Recorded Future. “One thing that is important to point out is that just because a victim appears on an extortion site, that doesn’t mean they were actually a victim — many extortion sites are notorious for lying about victims to generate notoriety or mentions on social media. This tactic is often used by new groups to attract more affiliates to their RaaS offering, but even some experienced groups do this.” Additionally, it is important to note that not all ransomware victims are posted to DLS.
Despite the surge in attacks in 2023, ransomware attacks involving payments decreased by 46%, according to our data. Essentially, it seems that while deploying ransomware has become easier due the professionalization of the criminal underground and lower barriers-to-entry, it is perhaps harder to profit from these activities. This trend is corroborated by incident response firms like Coveware, which paid just 28% of ransoms in incidents they were involved in last quarter. We attribute the decline in payments in part to enhanced cyber resilience among organizations, enabling them to better prepare, defend, and recover from incidents.
Additionally, the availability of undisclosed decryptors from public and private sector efforts, such as those for the Rhysida strain, and major law enforcement actions like the Hive intervention have reduced the need for ransom payments in some instances, underscoring the value of reporting incidents to law enforcement.
Qakbot takedown: Though impactful, operators adapt by pivoting to new malware
Active since approximately 2008, Qakbot (also known as Qbot or Pinkslipbot) originated as a banking Trojan with keylogging and sophisticated phishing techniques designed to steal financial credentials. Over the years, it has evolved significantly and expanded its malicious capabilities, typically orchestrated by groups such as TA570 and TA577.
This widespread reach, achieved through an expansive botnet for primary command and control communication, faced a major setback with a landmark infrastructure takedown announced by the U.S. Department of Justice (DOJ) in August 2023. “Operation Duck Hunt” successfully eradicated malware associated with the Qakbot botnet from over 700,000 systems and recovered millions in extorted cryptocurrency. The action was carried out by the Federal Bureau of Investigation (FBI) in collaboration with international law enforcement agencies and supported by private sector partners.
Several high-profile ransomware groups, such as Conti, Black Basta, and REvil, had been observed using Qakbot through Initial Access Brokers (IABs) as a preliminary infection route. These activities have caused extensive damage, affecting entities ranging from businesses, healthcare systems, to government agencies.
In the graph below, we see the Qakbot administrator wallet receiving cuts of ransomware proceeds directly and indirectly.
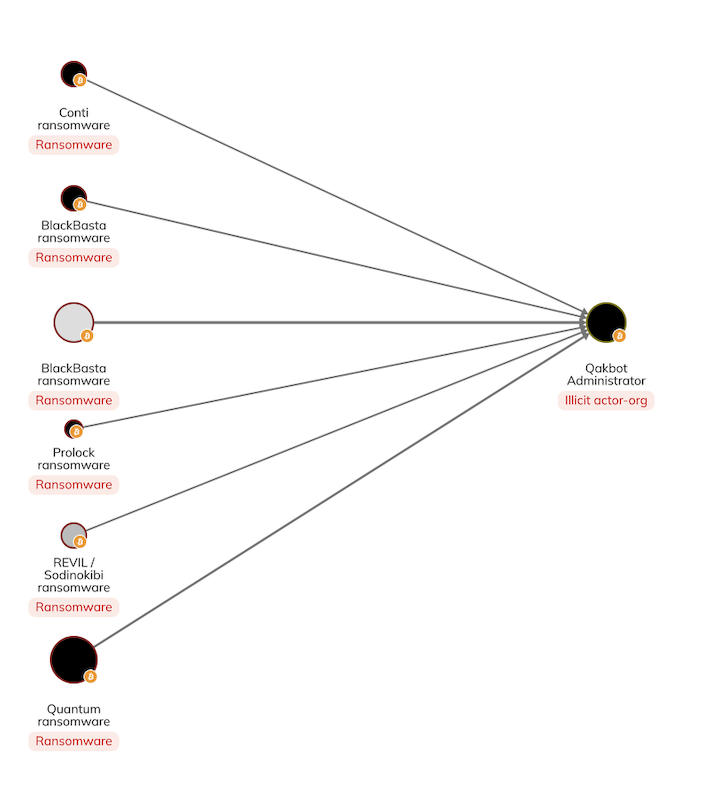
Are you a Reactor user? View the graph.
Ransomware strains like Conti, Prolock, Quantum, Sodinokibi/REvil, and Black Basta, leveraged the loader in successful ransomware attacks.
While Black Basta ransomware earned over $150 million in ransomware payments in 2023, without the Qakbot disruption, the toll would certainly have been far greater. As the chart below shows, there was a steep decline in Black Basta ransomware payments in June 2023, following peak months of April and May.
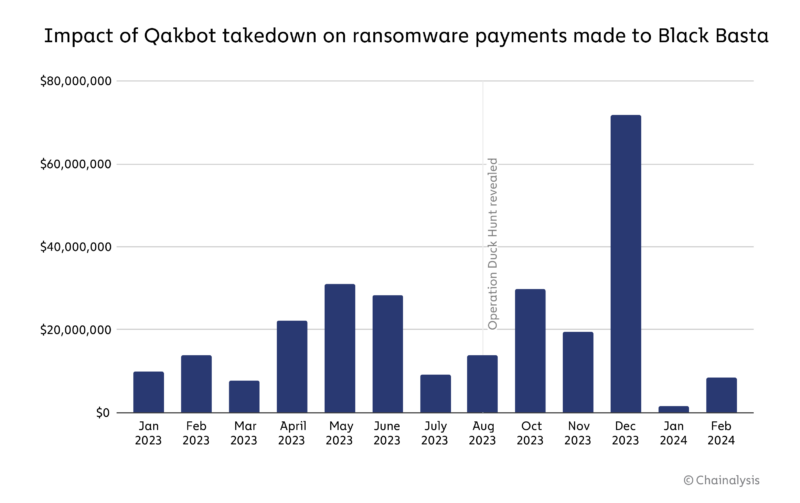
Activity appears to have picked up again some months later as Black Basta found alternatives, but the losses averted are undeniable. From August when the Qakbot takedown was announced, there was a significant year over year underperformance of Black Basta compared to its activity in 2022.
Despite the takedown of Qakbot, evidence shows that Black Basta has pivoted to new malware and is making a comeback. In fact, the number of transfers associated with Black Basta is recording all-time highs.
“TA577’s prominence in the realm of e-crime is not merely a matter of chance, but a testament to the threat actor’s ability to adapt,” said Kelsey Merriman, Staff Threat Researcher at Proofpoint, a cybersecurity and compliance company. “With a combination of campaign volume, evasion techniques, TTP changes, unwavering persistence, and the quick turnaround to ransomware, it remains as one of the greatest threats in the landscape. The Qakbot disruption was an overall positive, however it only impacted the malware — the operations of the prolific actor behind some of the most high-volume and iterative campaigns continues, just with new malware.”
Additionally, the Qakbot malware has not disappeared from the landscape entirely. Since late November 2023, Proofpoint has observed over ten campaigns distributing Qakbot malware in very low volumes. Most of these campaigns are not attributed to a tracked threat actor and appear to be testing delivery techniques to potentially use in the future. Notably, while TA577 favors Pikabot in recent campaigns, Proofpoint observed TA577 conduct just one Qakbot campaign in January before returning to other payloads.
Even after significant disruptions to malware, ransomware groups ultimately adapted and found alternatives, but not without substantial operational friction on dependent ransomware groups’ activities. Threat actors behind Qakbot have taken several months to reconstitute. Despite the marked success of “Operation Duck Hunt,” it’s important to acknowledge the prolific nature of the market for malware-as-a-service.
LockBit disruption: Deep infiltration leaves affiliates scrambling
First observed in 2020, LockBit operates as a ransomware-as-a-service (RaaS), allowing bad actors to use their malware to launch attacks that encrypt and potentially leak victim data unless a ransom is paid. Recognized as the most prolific ransomware strain due to its low barrier-to-entry, Lockbit accounted for 21% of data leak site postings in 2023 according to Recorded Future.
In February 2024, the National Crime Agency (NCA) and multinational law enforcement agencies, supported by private sector intelligence, carried out “Operation Cronos,” successfully seizing control of LockBit sites on the dark web along with their hacking infrastructure. The operation also resulted in the confiscation of their source code and cryptocurrency accounts. Additionally, NCA also recovered over 1000 decryptor keys to help victims recover encrypted data. Two individuals were arrested, and sanctions were levied on Russian LockBit affiliates.
According to the FBI, LockBit was linked to over 2,000 attacks, receiving at least $120 million in ransom payments from January 2020 to May 2023. Victims included local governments, public schools, and emergency services. Prior to this disruption, payments to LockBit represented over 15% of total ransomware payments.
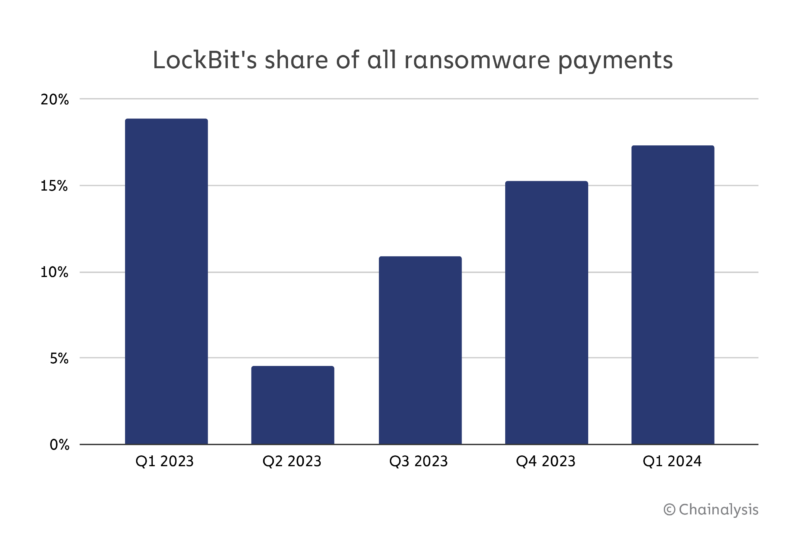
In the chart below, we can see that this disruption has significantly curtailed payments to LockBit.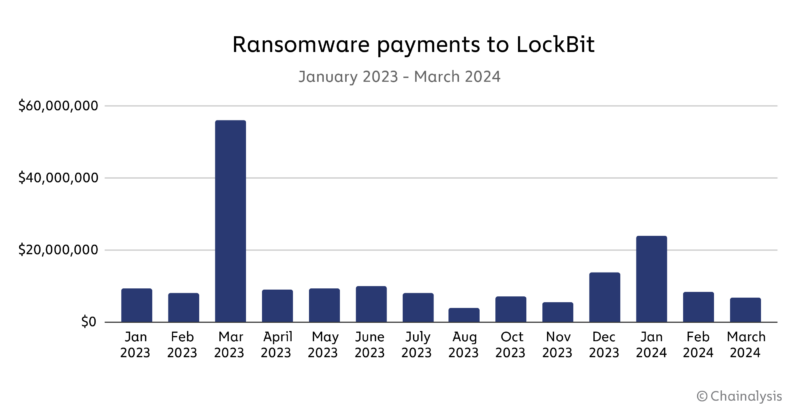
This operation was not merely about shutting down websites: It involved a meticulously planned infiltration that compromised the foundational trust within the LockBit community, significantly undermining LockBit’s operations and leaving its affiliates in disarray.
Still, the purported leader of LockBit insists that despite the setback, he is not finished and promises to continue his onslaught of hacking. “LockBit is as motivated as ever to make a comeback, has posted new victims, and claims to have released a new ransomware variant for use in its extortion campaigns,” said Jon DiMaggio, Chief Security Strategist at threat intelligence platform Analyst1, “While the takedown may not permanently end the LockBit gang’s operation, it certainly slowed them down and cost time and money. More importantly, it diminished their capacity to recruit top-tier affiliates, at least for now, by compromising the integrity of the operation.”
Although the action is over, the investigation is likely ongoing. With the help of Chainalysis, the NCA has identified and analyzed hundreds of active wallets and identified 2,200 Bitcoin — worth nearly $110 million — in unspent LockBit ransomware proceeds still yet to be laundered.
BlackCat: Anatomy of a ransomware rugpull
ALPHV/BlackCat RaaS was a highly active ransomware family that emerged in November 2021. This group operated on the common RaaS model, offering their malware to affiliates while taking a share of the ransom payments.
BlackCat gained notoriety for its methods of gaining initial access through stolen credentials and launched attacks on a multitude of global organizations, including oil companies, schools, and hospitals. Their tactics were notably aggressive, often involving double or triple extortion methods, including distributed-denial-of-service (DDoS) threats, and they introduced innovative strategies such as establishing a public data leak site to escalate pressure on their victims for payments.
In December 2023, the DOJ announced the disruption of BlackCat, provisioning 300 decryptor keys to victims and saving approximately $68 million dollars in payments, but BlackCat was able to reconstitute.
In March of 2024, the BlackCat ransomware group reportedly vanished after an exit scam, following a supposed $22 million ransom payment from UnitedHealth’s Change Healthcare unit. After the alleged payment, BlackCat displayed a law enforcement seizure notice on their darknet site to suggest that their operations had been forcibly terminated. This was debunked as a ruse by the admin in order to pocket the multimillion dollar payment without giving the affiliate their due share of 80-85%.
BlackCat’s exit marks a major disruption in the ransomware payment ecosystem, as the group was capturing over 30% of all ransomware payments before the exit scam, as shown in the chart below. BlackCat was the highest grossing RaaS at the end of 2023.
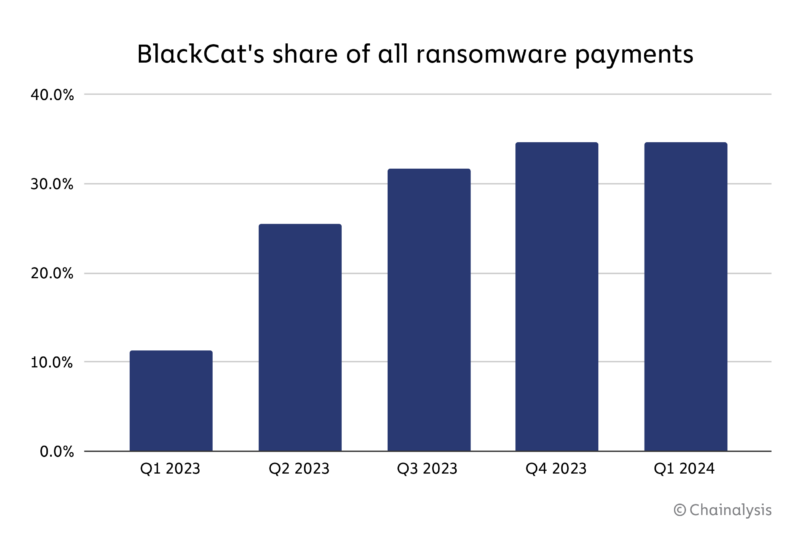
The implications of an exit scam does not bode well for any future iterations of the group. Even the Wild West of the ransomware ecosystem has its own code of criminal ethics, with ransomware affiliates entrusting aspects of their security and oftentimes their earnings in the hands of the ransomware operation they elect to join. This incident has significantly tarnished the group’s reputation, and perhaps more generally, planted seeds of doubt in the ransomware-as-a-service business model.
Adaption, diversification: How ransomware actors respond to disruptions
While disruptions lead to operational friction and disarray in ransomware groups, as evidenced by decreased ransomware payments and activities, the ransomware model’s inherent flexibility allows affiliates and members of the ransomware supply chain to pivot to new strategies, including monetizing stolen data from previous victims.
We have noticed a trend: the number of strains affiliates seem to be using has been increasing. This suggests a period of experimentation and adaptation aimed at circumventing future disruptions.
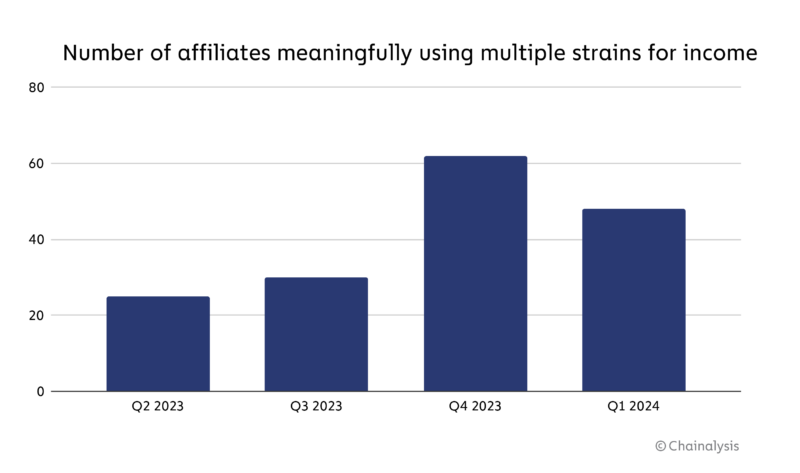
While the number of affiliates using multiple strains for income declined in the first quarter of 2024, it still remains elevated. This might signify that affiliates exposed to disruption are testing out new strains, pivoting away from the strains that were disrupted, or perhaps going out on their own.
The enduring challenge lies in the adaptability of ransomware actors. It is relatively low-cost for affiliates to change strains, and they do so with agility. Actions that increase the perceived risks, distrust, and operational downtime for affiliates can create a lasting impact on their activities.
We previously cited signals in our data of new threat actors engaged in ransomware activity in our 2024 Crypto Crime Report. We continue to monitor affiliates and former affiliates’ behavior into 2024 and the impact of recent events on their risk calculus and decisions to remain engaged in ransomware.
Victories accumulate, but the war against ransomware continues
The fight against ransomware, marked by significant disruptions and historically impactful collaborations between the public and private sectors, underscores the complex relationship between immediate impacts and the long-term adaptability of cybercriminal networks.
The ongoing decrease in ransom payments, despite a reported increase in the number of attacks, reflects the growing reluctance of victims to comply with the demands of cybercriminals. Sanctions and a broader aversion among organizations to fund criminal activities speaks to an evolving sentiment where paying ransoms is increasingly seen as unacceptable or unnecessary.
Innovative disruption strategies involving a whole-of-government approach targeting every part of the cybercriminal ecosystem — from the infrastructure, to the laundering mechanisms, to arrests, sanctions, and asset seizures, along with the use of blockchain intelligence tools, are essential for understanding and counteracting the affiliates’ adaptation mechanisms. Continued victim reporting and collaboration with law enforcement can provide valuable intelligence, and as we’ve seen over the last year, and potentially provide victims with a decryptor that prevents them from paying the ransom. To that end, Chainalysis Head of Cyber Threat Intelligence Jacqueline Burns Koven testified before a U.S. House of Representatives Financial Services Committee hearing on ransomware. During her testimony, Koven spoke to not only the innovative disruption strategies required, but also to the importance of public-private partnerships and bi-directional information sharing.
Strong public-private partnerships and bi-directional information sharing are key elements of the success we’ve seen in disrupting ransomware and its money laundering networks.
More from @JBurnsKoven in today’s @FinancialCmte & @FSCDems hearing on ransomware: pic.twitter.com/U53UmDKLFX
— Chainalysis (@chainalysis) April 16, 2024
Read Jacqueline Burns Koven’s full written testimony to the committee. A full recording of the hearing is also available.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

