On April 24, 2023, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned three individuals operating in China for facilitating Democratic People’s Republic of Korea (DPRK) cryptocurrency money laundering activities used to fund weapons of mass destruction and missile programs. Cryptocurrency addresses were included in the SDN list entries for two of the three individuals, and the Department of Justice (DOJ) also charged one of them in an unsealed indictment released today.
In this blog, we’ll examine the details of these charges and sanctions, and the new information they reveal about North Korea’s cryptocurrency money laundering processes.
Who was charged and sanctioned?
The three individuals sanctioned by OFAC are Wu Huihui (Wu), Cheng Hung Man (Cheng), and Sim Hyon Sop (Sim). Sim was also charged by the DOJ for his role in money laundering conspiracies.
Wu is a China-based over-the-counter (OTC) cryptocurrency trader who converted millions of dollars’ worth of stolen cryptocurrency into fiat currency on behalf of DPRK actors working with Lazarus Group, a North Korea-affiliated cybercriminal syndicate.
Cheng, an OTC trader based out of Hong Kong, directly supported Wu’s actions. Through the use of shell companies, Cheng and Wu helped the DPRK circumvent U.S. sanctions and convert cryptocurrency — much of it stolen in hacks — into cash.
Sim helped the already-OFAC-designated Korea Kwangson Banking Corp (KKBC) orchestrate money-laundering schemes to support DPRK weapons production and purchase goods on behalf of the Koren government. According to OFAC, Sim received tens of millions’ worth of cryptocurrency while acting as a representative of KKBC, much of which came from North Korean IT workers who fraudulently worked overseas, including in the U.S. These workers often leveraged fake information to apply and work for companies in the technology and cryptocurrency industries, while specifically requesting payment in cryptocurrencies. North Korea’s usage of IT workers to generate foreign income has been previously highlighted in a joint advisory by the U.S. government.
Sim reportedly then coordinated with OTC traders, including Wu and Cheng. In the scheme, Sim would receive the salaries from the IT workers, send payments to shell companies operated by Wu and Cheng, and in converting the cryptocurrency to fiat, utilize those funds to purchase goods on behalf of DPRK.
Money laundering tactics using mixers
Chainalysis research has revealed that North Korea-linked hackers typically use mixers to launder large amounts of money, and that they use mixers at a much higher rate than other illicit actors. In the past, these hackers have utilized mixers such as Tornado Cash and Sinbad.
The information revealed today by OFAC and the DOJ gives us more insight into what happens after North Korean actors leverage mixers using intermediaries – including OTCs – before ultimately converting cryptocurrency into cash at an exchange. The Chainalysis Reactor graph below shows some of this activity.
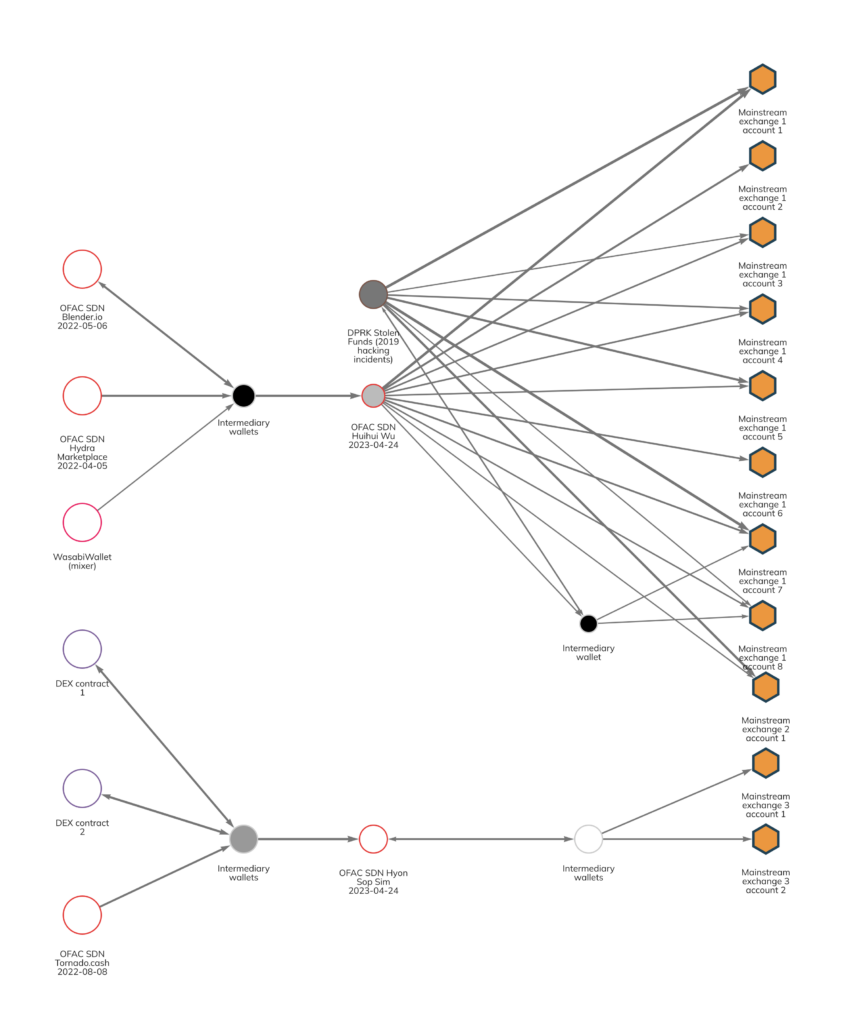
Here, we can see how DPRK actors leveraged mixing services to obfuscate the origin of ill-gotten funds, as well as decentralized exchanges. These funds then went to Wu’s and Sim’s wallets, and other OTC markets. Wu and Sim transferred to mainstream exchanges, after which they converted cryptocurrency to fiat currency. Additionally, we see how DPRK funds related to two 2019 hacks and held in addresses mentioned in a previous forfeiture complaint were cashed out at a number of the same service deposit addresses leveraged by these OTC traders.
Monitoring malicious cryptocurrency-based cyber crimes
Lazarus Group is responsible for the biggest cryptocurrency hack ever in addition to countless thefts and similar financial crimes. In 2022 alone, we attributed $1.7 billion in stolen cryptocurrencies to Lazarus Group. Its activities, as well as those of other DPRK threat actors such as the fraudulent IT workers highlighted in today’s designation, present serious threats to the public safety and financial systems of countries around the world.
OFAC’s and DOJ’s actions demonstrate their dedication to reducing malicious cyber crimes in connection with cryptocurrencies. Today’s designated actors carry secondary sanctions risk, meaning even non-U.S. persons may be subject to sanctions if they engage in significant transactions with Wu, Cheng, or Sim. This further emphasizes the importance of cryptocurrency participants knowing their exposure to these individuals and entities associated with them.
We will continue to provide more research on the role of cryptocurrency in cybercrimes in the near future.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

