On February 20, 2024, the U.K.’s National Crime Agency (NCA), alongside the U.S. Department of Justice (DOJ), announced the disruption of Lockbit, which has been one of the most prolific Ransomware-as-a-Service (RaaS) groups operating over the last few years. In this operation, the NCA, FBI, and international law enforcement partners worked together to seize servers and public-facing websites that were integral to Lockbit’s operations, and have obtained decryptor keys for Lockbit victims to recover their data without paying a ransom. The DOJ also announced charges against Artur Sungatov and Ivan Kondratyev, two Russian nationals accused of acting as Lockbit RaaS affiliates and using the strain in ransomware attacks. Additionally, OFAC sanctioned both individuals for their ransomware activities, and included ten total cryptocurrency addresses as SDN List identifiers. These actions come following the May 2023 indictment and sanctioning of Lockbit-affiliated ransomware developer Mikhail Matveev.
We’re proud to share that the NCA used Chainalysis tools in carrying out this investigation. Below, we’ll talk more about the unique position Lockbit occupied within the ransomware ecosystem and why this action was important.
Lockbit was one of the most widely used RaaS strains
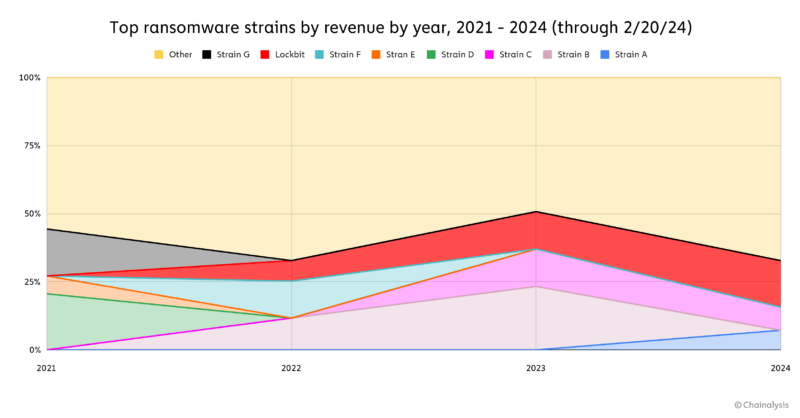
According to the DOJ, Lockbit attacked over 2,000 victims and made over $120 million in revenue. Our data shows that Lockbit’s prominence within the ransomware ecosystem was growing quickly over time.
| Year | Lockbit’s rank in ransomware strain revenue |
| 2021 | 8 |
| 2022 | 4 |
| 2023 | 2 |
| 2024 | 2 |
Furthermore, Lockbit was among the most resilient strains in the ransomware ecosystem since the RaaS launched, and remained active for longer than most other strains.
As a RaaS strain, Lockbit malware was available for other cybercriminals known as affiliates to rent in order to launch their own ransomware attacks in exchange for a cut of any revenue from those attacks. Our data suggests that Lockbit was one of the most prolific and widely used RaaS strains in operation, with potentially hundreds of affiliates, including many associated with other prominent strains.
Lockbit’s willingness to provide services to so many affiliates may be one reason for the chaos researchers have observed within the group, such as the group’s continuing attacks against hospitals even after core administrators vowed to stop targeting healthcare providers, and an incident in which Lockbit administrators publicly refused to pay an affiliate for an attack. These incidents and seeming inability to coordinate may be the result of a lack of affiliate vetting.
At times, Lockbit’s administrators engaged in publicity stunts whose value appears questionable in comparison to their risk to the group’s operational security. For example, in 2022, a Lockbit administrator known by the online handle LockBitSupp announced that they would pay $1,000 to anyone who got a tattoo of the Lockbit logo. Analysis of LockBitSupp’s on-chain activity during this time period suggests that, shockingly, many took them up on the offer. We can see some of these payments on the Chainalysis Reactor graph below.
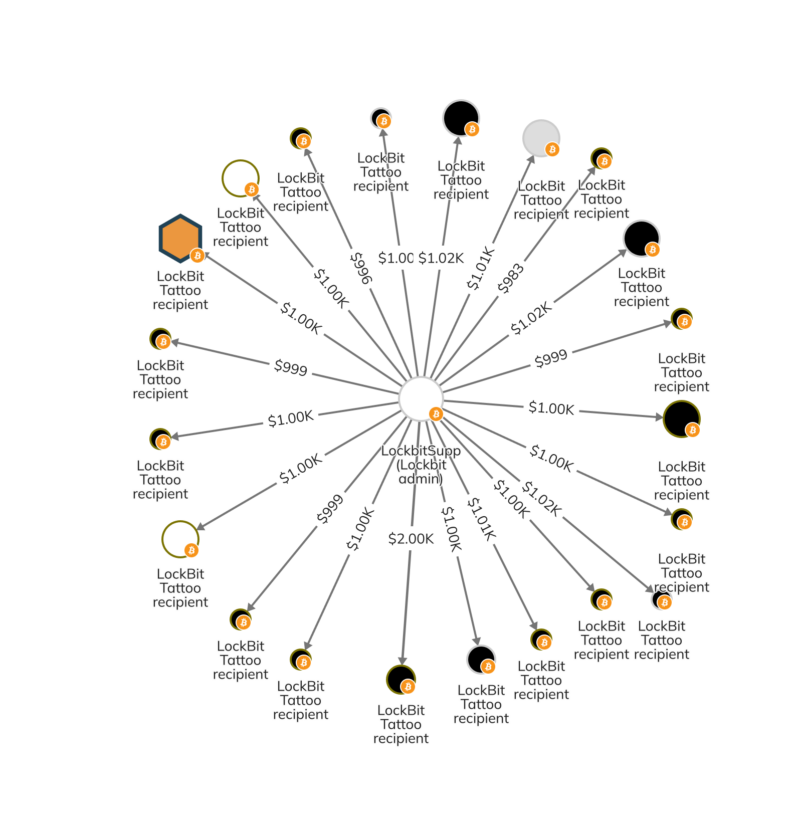
Suffice it to say, administrator behavior like this and the seemingly low bar for affiliate access to Lockbit doesn’t paint the group as the most professional in the ransomware ecosystem.
Lockbit and sanctions risk
Even before recent sanctions explicitly targeting Lockbit affiliates, the strain’s low barrier to entry made the RaaS an attractive cover for threat actors to obfuscate their sanctions ties. For instance, in June 2022, cybersecurity firm Mandiant released research suggesting that Russian ransomware gang Evil Corp had begun using Lockbit. Mandiant positioned this as likely an effort by Evil Corp to disguise itself, as at that time Evil Corp’s own connection to sanctioned Russian entities was decreasing its victims’ willingness to pay ransoms — you can read our prior research on ransomware strain rebranding to learn more about this practice. On-chain data confirms the connection between Lockbit and Evil Corp, as we see on the Reactor Graph below.
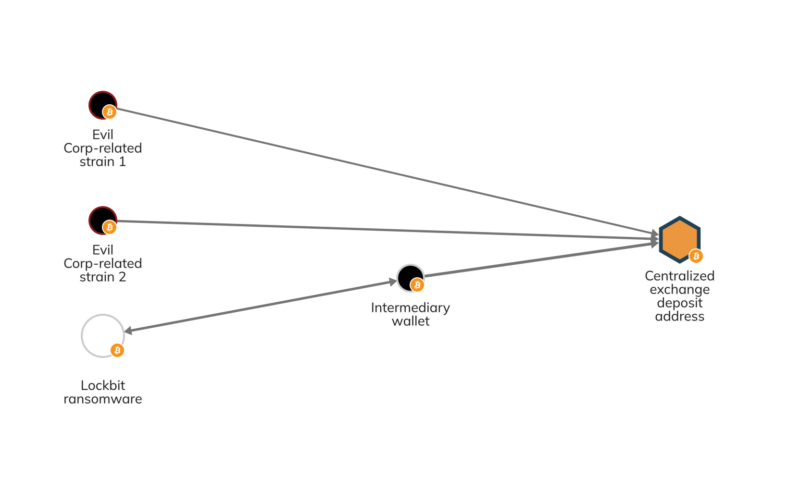
Here, we see Lockbit and two other strains that have been identified as Evil Corp rebrands sending funds to the same exchange deposit address.
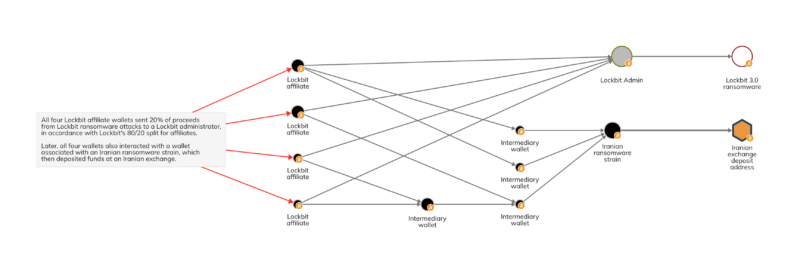
Similarly, we also see on-chain evidence of Lockbit affiliates working with an Iranian ransomware strain and depositing at an Iranian exchange suggesting the pictured Lockbit affiliate is likely Iranian.— Iran is, of course, one of the most heavily sanctioned jurisdictions in the world.
Finally, blockchain analysis also shows that a Lockbit administrator also donated crypto to a pro-Russia self-proclaimed military journalist based in Sevastopol known as Colonel Cassad. Throughout social media, Colonel Cassad has solicited donations for Russian militia group operations in the sanctioned jurisdictions of Donetsk and Luhansk, as we identified early on in the Russian war against Ukraine.
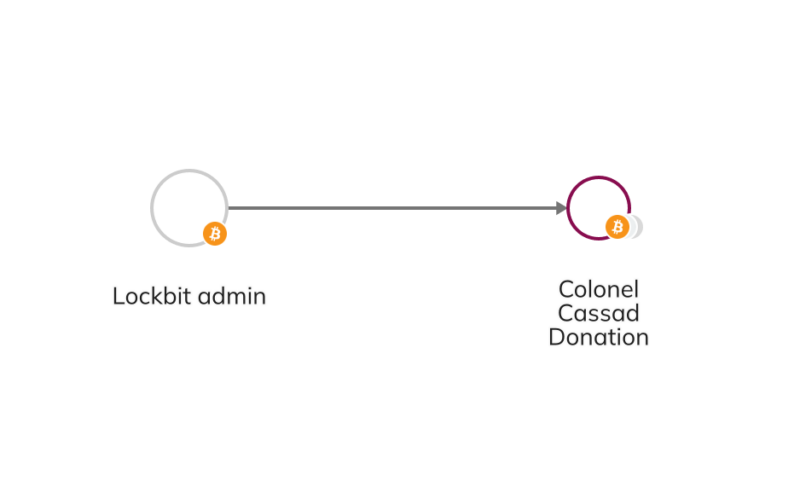
Talos cybersecurity researchers have previously written about links between Colonel Cassad and Russian state hacking unit Fancy Bear, which has been sanctioned by the EU.
OFAC notes ten cryptocurrency addresses in sanctions against Lockbit affiliates Artur Sungatov and Ivan Kondratyev
In its SDN List entries for Lockbit affiliates Ivan Kondratyev and Artur Sungatov, OFAC included a total of ten cryptocurrency addresses controlled by the two individuals — nine for Kondratyev and one for Sungatov. Those addresses are below.
Ivan Kondratyrev cryptocurrency addresses
- 1A7SKE2dQtezLktCY8peLsdAtkqxV9r1dC (Bitcoin)
- Bc1q8ew45w2agdffrnwp6adt2gqrc9n4mkev9ns29c (Bitcoin)
- bc1qagp0gy58v8hqvw4p2wsphcxg067rrppp45hexr (Bitcoin)
- bc1qn6segn8km4nfdp9vueu6msfjsaxaqgun9h60n9 (Bitcoin)
- bc1qx9upga7f09tsetqf78wa3qrmcjar58mkwz6ng6 (Bitcoin)
- 0xf3701f445b6bdafedbca97d1e477357839e4120d (Ethereum)
- 15cRqR3TXS1JehBGWERuxFE8NhWZzfoeeU (Bitcoin)
- bc1q5jqgm7nvrhaw2rh2vk0dk8e4gg5g373g0vz07r (Bitcoin)
- 32pTjxTNi7snk8sodrgfmdKao3DEn1nVJM (Bitcoin)
Artur Sungatov cryptocurrency address
- 18gaXypKj9M23S2zT9qZfL9iPbLFM372Q5 (Bitcoin)
Authorities have taken down a major player in ransomware
These law enforcement actions represent a big win in the fight against ransomware. As we’ve explored above, Lockbit was one of the most prolific strains operating for several years — taking down its infrastructure and obtaining decryptor keys will save many organizations from damaging ransomware attacks. We commend all agencies involved.

