Today, paperwork was filed in the case of Ilya Lichtenstein and Heather Morgan (also known by her rap name Razzlekhan) for their role in laundering the more than 120,000 Bitcoin stolen from Bitfinex in 2016, suggesting the couple will plead guilty in a hearing scheduled for August 3rd. The stolen Bitcoin was valued around $70 million at the time of the theft, but worth over $4 billion at the time of their arrest in February 2022.
As we covered at the time, U.S. authorities were able to recover over 94,000 of the stolen Bitcoin following a joint investigation by the FBI, IRS-CI, and HSI. On August 9th 2022, in a previously unreported set of transactions, U.S. authorities recovered an additional 12,267 Bitcoin directly from the wallets of the initial theft. And on November 18th 2022, U.S. authorities recovered a further 1,155 Bitcoins. On January 5th, an additional 2.5 Bitcoins was recovered. The second, third, and fourth recoveries bring the amount recovered by U.S. authorities to over 108,068 Bitcoin.
The arrest and seizure, along with today’s filing, represent another major victory for law enforcement in the fight against cryptocurrency-based crime. We’ve written previously about how important it is for law enforcement to develop the ability to seize criminally-obtained cryptocurrency, and published a guide last year on how cryptocurrency businesses and law enforcement can work together to facilitate seizures. The Bitfinex investigation is a great example of this collaboration.
Below, we’ll explore how the husband-and-wife duo’s money laundering strategy evolved in the years following the hack, and tell you more about how law enforcement cracked the case.
Tracking Bitfinex’s stolen funds
We constructed the Chainalysis Reactor graph below based on the publicly-available DOJ indictment describing how Lichtenstein and Morgan moved the Bitcoin stolen from Bitfinex. While the information provided in the indictment wasn’t enough to trace the movements of funds to every cryptocurrency service mentioned, the graph below shows how the couple’s money laundering strategy evolved over time. We should also note that while not all of these businesses meet the conventional definition of an exchange, the DOJ indictment refers to all of them as Virtual Currency Exchanges (VCEs) and anonymizes them with simple, numbered labels (VCE 1, VCE 2, etc.), which we’ll also use here.
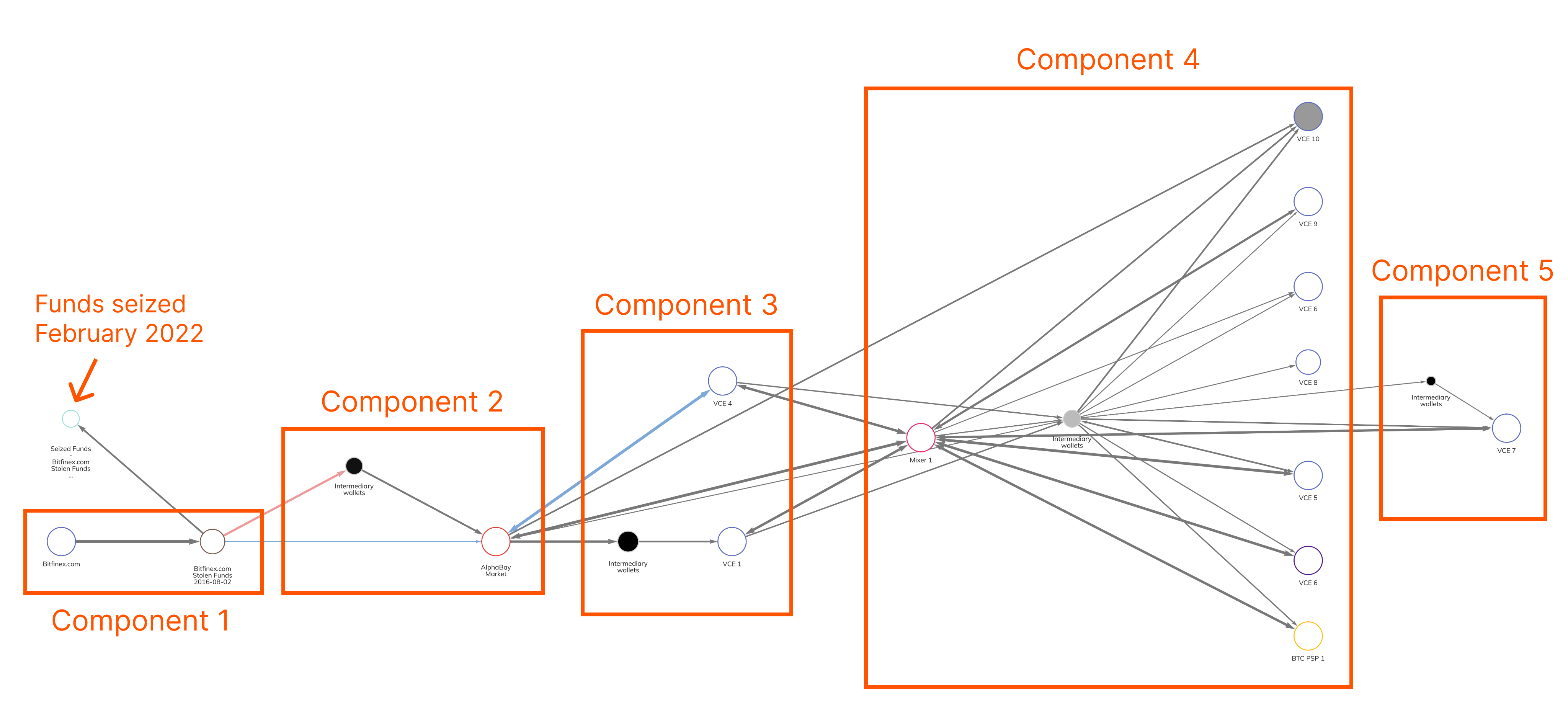
The laundering of the Bitfinex funds had five distinct components, some of which were carried out in overlapping time periods, involving several different cryptocurrency businesses.
Component 1: The theft
First, we see the initial theft: In a series of 2,075 transactions taking place in August 2016, the hacker moved 120,000 Bitcoin from Bitfinex to a wallet we labeled “Bitfinex.com Stolen Funds.” Most of the funds never left that wallet. Directly above the hacker’s wallet, we see that those funds were seized by law enforcement and moved to a new wallet nearly six years later in February 2022.
Component 2: Using a darknet market as a mixer
In January 2017, Lichtenstein and Morgan moved a large portion of the funds to the now-defunct darknet market AlphaBay, which the couple essentially used as a mixer by depositing the stolen Bitcoin and withdrawing equivalent amounts. Some funds moved to AlphaBay directly from the initial theft wallet, while others were moved there through intermediary wallets.
Component 3: Movements to VCEs and first cashouts
Soon after that, Lichtenstein and Morgan moved funds from AlphaBay to four cryptocurrency exchanges, which the indictment refers to as VCEs 1-4. The information provided in the indictment only allows us to show movements to VCEs 1 and 4 on the graph above, but the movements to VCEs 2 and 3 likely look similar. Lichtenstein and Morgan created several different accounts using fake identities at these exchanges to receive the Bitcoin laundered through AlphaBay — in at least some cases, compliance teams at the exchanges were able to detect that the accounts likely belonged to the same person, for instance due to similarities in the email addresses used to register them and overlaps in the IP addresses used to access the accounts. Some of the exchanges froze the accounts due to this suspicious activity, as well as Lichtenstein and Morgan’s inability to verify their identities or the source of the funds.
Component 4: Mixer usage and more VCEs
By 2019, AlphaBay had been taken down by law enforcement, so Lichtenstein and Morgan needed a new money laundering method. They began sending funds to a popular mixer, and then on to more VCEs (VCEs 5-10 in the indictment) where they swapped the Bitcoin for other assets, including Monero. Additionally, the pair sent some funds to a precious metals seller via a merchant services provider (labeled BTC PSP 1) in order to swap their cryptocurrency for gold. The indictment details how Lichtenstein and Morgan in some instances attempted to convince exchange representatives that their Bitcoin came from payment for advertising services, even creating a shell corporation to sell the story.
Component 5: Funds exchanged for cash at VCE 7
Finally, in 2020 and 2021, Lichtenstein and Morgan were able to convert more funds into fiat currency at VCE 7 and move them into a U.S. bank account. The pair was also able to buy gift cards for Walmart and other businesses at VCE 10 — a specialized service devoted to crypto-for-gift card trades rather than a conventional cryptocurrency exchange — using the Bitcoin they’d moved to VCE 10 previously.
Blockchain analysis and traditional police work solved this case
In the end, the gift card purchases described above provided crucial clues in the investigation. After tracing the initial movements of cryptocurrency, investigators discovered that a personal wallet address beginning with 36B6mu, which had received over $1 million worth of Bitcoin associated with the Bitfinex hack, provided funding for the account at VCE 10 used to purchase gift cards. Agents discovered that the Walmart gift card specifically was redeemed through Walmart’s iPhone app under an account in Heather Morgan’s name. That enabled agents to get a search warrant for Lichtenstein and Morgan’s home and cloud storage accounts, where they found files containing details of the cryptocurrency addresses used to move the stolen funds — including their private keys — along with the false information used to open accounts at cryptocurrency exchanges and plans to acquire fake passports. That discovery enabled investigators to trace the flow of funds in its entirety.
This case illustrates how blockchain analysis combined with traditional financial investigation techniques can empower law enforcement to solve cryptocurrency-related crime, win convictions, and seize stolen funds — in this case, over $3 billion worth at the time of arrest. We commend the agents at IRS-CI, FBI, and HSI who conducted this investigation, and look forward to working with our customers in the public sector to prevent further theft and abuse of crypto assets.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
