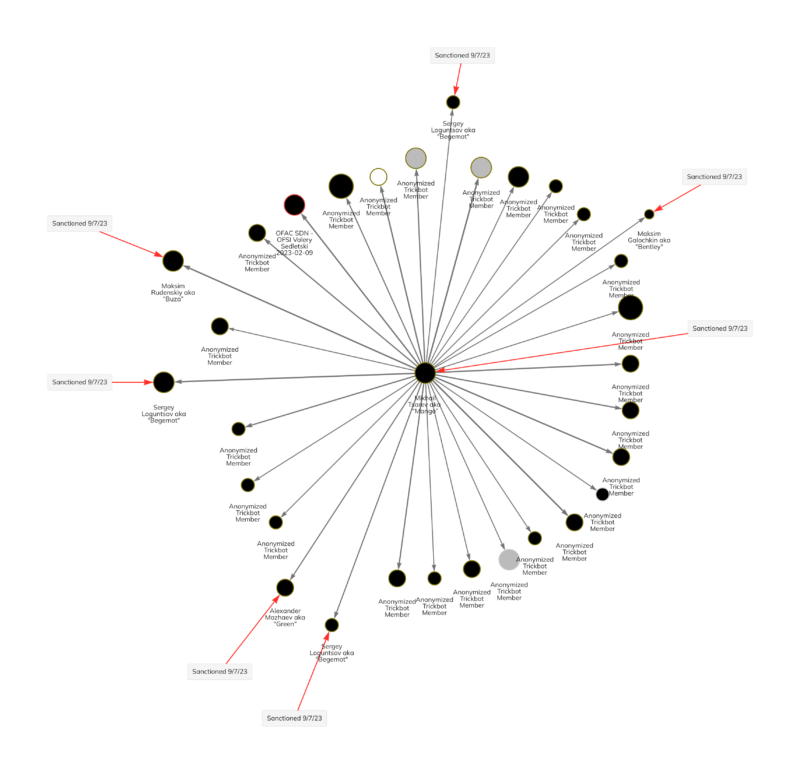
Continuing the crackdown on Russia-based ransomware group Trickbot, the U.K. HM Treasury Office of Financial Sanctions Implementation (OFSI) and the U.S. Office of Foreign Assets Control (OFAC) have imposed sanctions against an additional eleven individuals. Today’s announcement implicates well-known actors including Maksim Galochkin, also known by the alias “Bentley,” Maksim Rudenskiy aka “Buza,” “Silver,” or “Binman,” and Mikhail Tsarev aka “Mango,” along with other members. This action follows the joint U.K. and U.S. sanctioning of seven Trickbot figures earlier this year — a historic first.
Ransomware is one of the most prevalent issues in cybercrime, accounting for at least $449.1 million in extorted funds from January through June of this year, according to Chainalysis data. The Trickbot cybercrime group is behind the deployment of several ransomware strains including Ryuk, Conti, Diavol, and Karakurt. Those strains are responsible for at least $833M worth of cryptocurrency extortion throughout their lifespans.
While Bitcoin payments continue to be the instrument of choice for ransomware actors, it turns out that processing illicit transactions on an immutable public ledger can be an asset to counter cybercrime.
“These sanctions are a continuation of our campaign against international cyber criminals. Attacks by this ransomware group have caused significant damage to businesses and ruined livelihoods, with victims having to deal with the prolonged impact of financial and data losses.” Said Rob Jones, Director General of Operations at the National Crime Agency. “Cryptocurrencies are a preferred method of payment within the online cybercriminal ecosystem, and a vital part of the business model that enables ransomware actors to extort victims. However, cryptocurrencies also offer investigative opportunities for law enforcement and we work closely with private and public sector partners to exploit these opportunities in our fight against international cyber crime.”
Chainalysis solutions can help identify the actors behind ransomware and other cyber attacks, which in turn, helps authorities disrupt the operational flow and supply chain of the entire network. This is essential for dismantling cybercrime groups like Trickbot, which demonstrates deep ties to other malicious entities.
Trickbot and cyber attacks
First identified in 2016, Trickbot Group is among the highest crypto-earning cybercrime organizations, following North Korea’s Lazarus Group. Trickbot Group has ties to Russian intelligence services and is a known collaborator with other cybercrime entities. Ransomware strains associated with Trickbot have infected millions of devices worldwide, including computers belonging to hospitals and healthcare centers.
The following individuals have been designated by OFSI and OFAC:
- Andrey Zhuykov, aka “Defender” or “DIF”
- Maksim Galochkin, aka “Bentley,” “Crypt,” or “Volhvb”
- Maksim Rudenskiy, aka “Buza,” “Silver,” or “Binman”
- Mikhail Tsarev, aka “Mango”
- Dmitry Putilin, aka “Grad” “Staff”
- Maksim Khaliullin, aka “Kagas”
- Sergey Loguntsov, aka “Begemot”
- Alexander Mozhaev, aka “Green” or “Rocco”
- Vadym Valiakhmetov, aka “Weldon,” “Mentos,” or “Vasm”
- Artem Kurov, aka “Naned”
- Mikhail Chernov, aka “Bullet”
OFAC and OFSI did not include specific Trickbot-associated cryptocurrency addresses in their announcement. However, Chainalysis has identified cryptocurrency wallets linked to the sanctioned individuals and we continue to label those addresses in our paid products.
Breaking down the Trickbot team members sanctioned today and their Bitcoin activity
The members in today’s designation span a variety of teams and roles within Trickbot, highlighting the group’s organizational structure. Individuals sanctioned today include roles in administration, testing, obfuscation, and development. We examine some of the specific individuals designated below.
Mikhail Tsarev aka “Mango”
Mango is a prominent Team Lead and right-hand man to Trickbot Group lead Stern, and looms large in the leaked Conti chats as well as on the blockchain. Mango received millions of dollars in cryptocurrency from Stern derived from the proceeds of ransomware. We can see Mango disbursing the Bitcoin to various departments for salaries and equipment to keep Trickbot Group in operation.
Maksim Galochkin aka “Bentley,” “Crypt,” or “Volhvb”
Bentley is a frequent contact of Mango’s and was the technical lead for Trickbot and BazarBackdoor — another type of malware used by the group. Bentley managed the crypting team, who is responsible for the processes of obfuscating malware to avoid antivirus detection on victim machines. He requests payments for server infrastructure and to pay the employees maintaining them. Bentley and many of the other actors featured in this designation are using funds to make payments in cryptocurrency for infrastructure like bulletproof hosting, virtual private server hosting, or services like crypting, AV checking, and salary disbursements. VPS hosting provided infrastructure for development, internal communication, malware command and control, and ransomware negotiation operations.
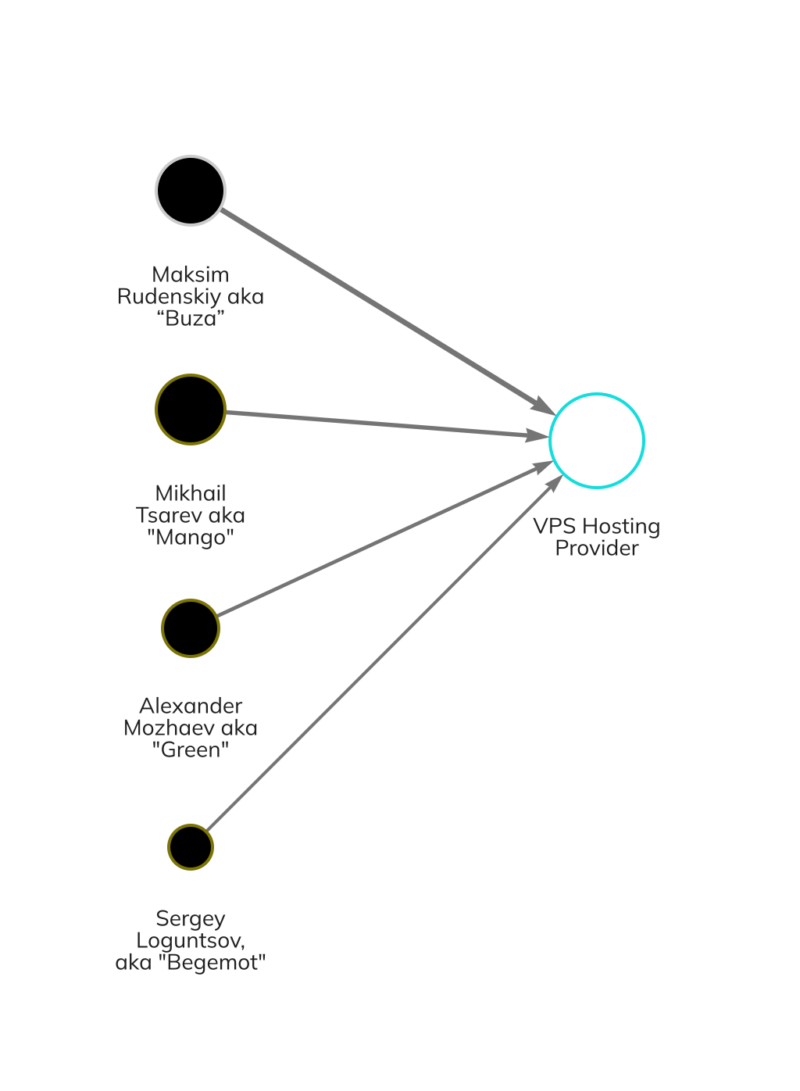
Maksim Rudenskiy aka “Buza,” “Silver,” or “Binman”
Buza is another technology lead who manages developers and is involved in hiring and dispensing payments for the team. He is involved in crypters, loaders, and cryptography — the encryption technique behind ransomware.
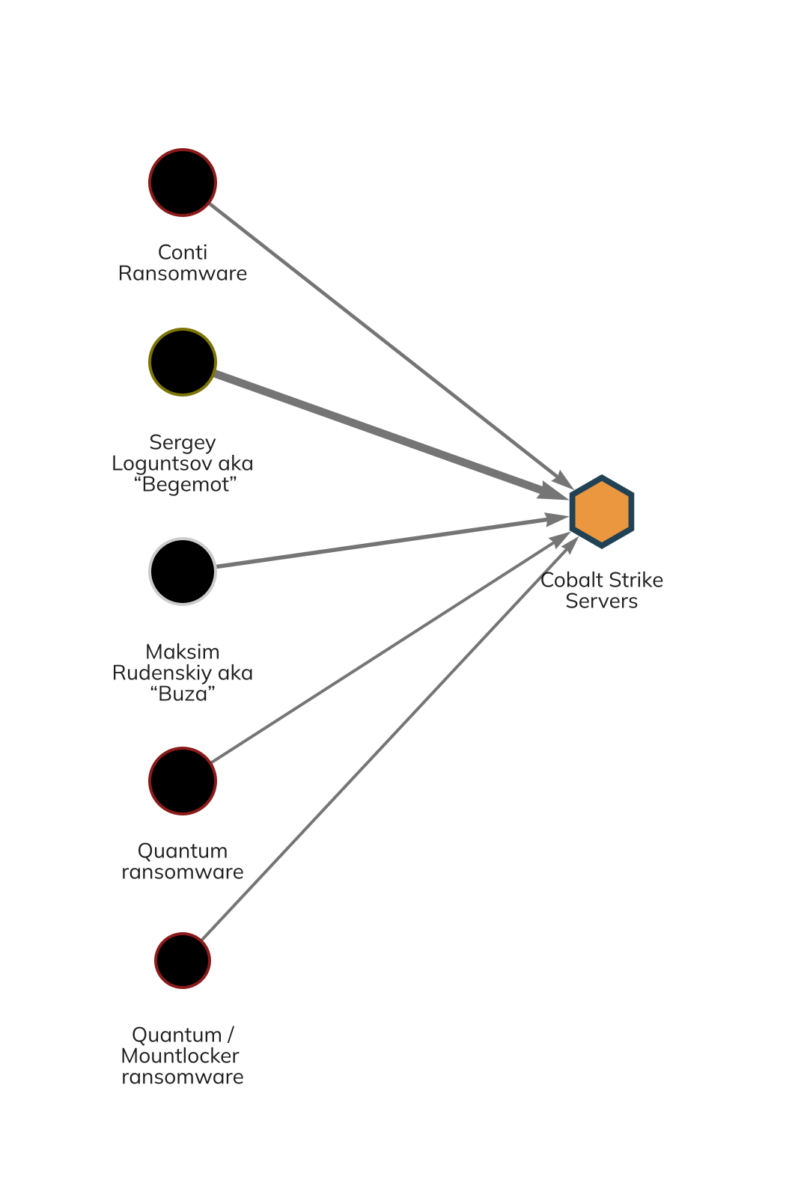
Some of the wallets belonging to individuals sanctioned today indicate connections to or shared infrastructure providers with newer ransomware strains that have emerged since Conti’s decline, such as Royal, Quantum, and Mountlocker. Below we see payments for Cobalt Strike servers — a popular penetration testing tool — from two of the actors sanctioned today, plus wallets associated with Conti, Quantum, and Mountlocker.
Globalizing blockchain intelligence
As cybercriminals continue to use blockchain technology for illicit activities, enforcement agencies across the globe are collaborating and using on-chain data to tackle cybercrime on an international level.
Through the analysis of blockchain data, law enforcement agencies can uncover information that leads to the identities and roles of individuals involved in ransomware and other cybercrimes. Specialized technology like Chainalysis enables them to trace the flow of funds with remarkable precision.
The landmark partnership between the U.S. OFAC and the U.K.’s Foreign, Commonwealth, and Development Office; National Crime Agency; and His Majesty’s Treasury, demonstrates a unified global commitment to combat cybercrime in a blockchain-enabled world.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.

